Three-party decryption method based on parent-child relationship verification
A technology of parent-child relationship, parent element, applied in the usage of multiple keys/algorithms, transmission systems, digital transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be specifically introduced below in conjunction with the accompanying drawings and specific embodiments.
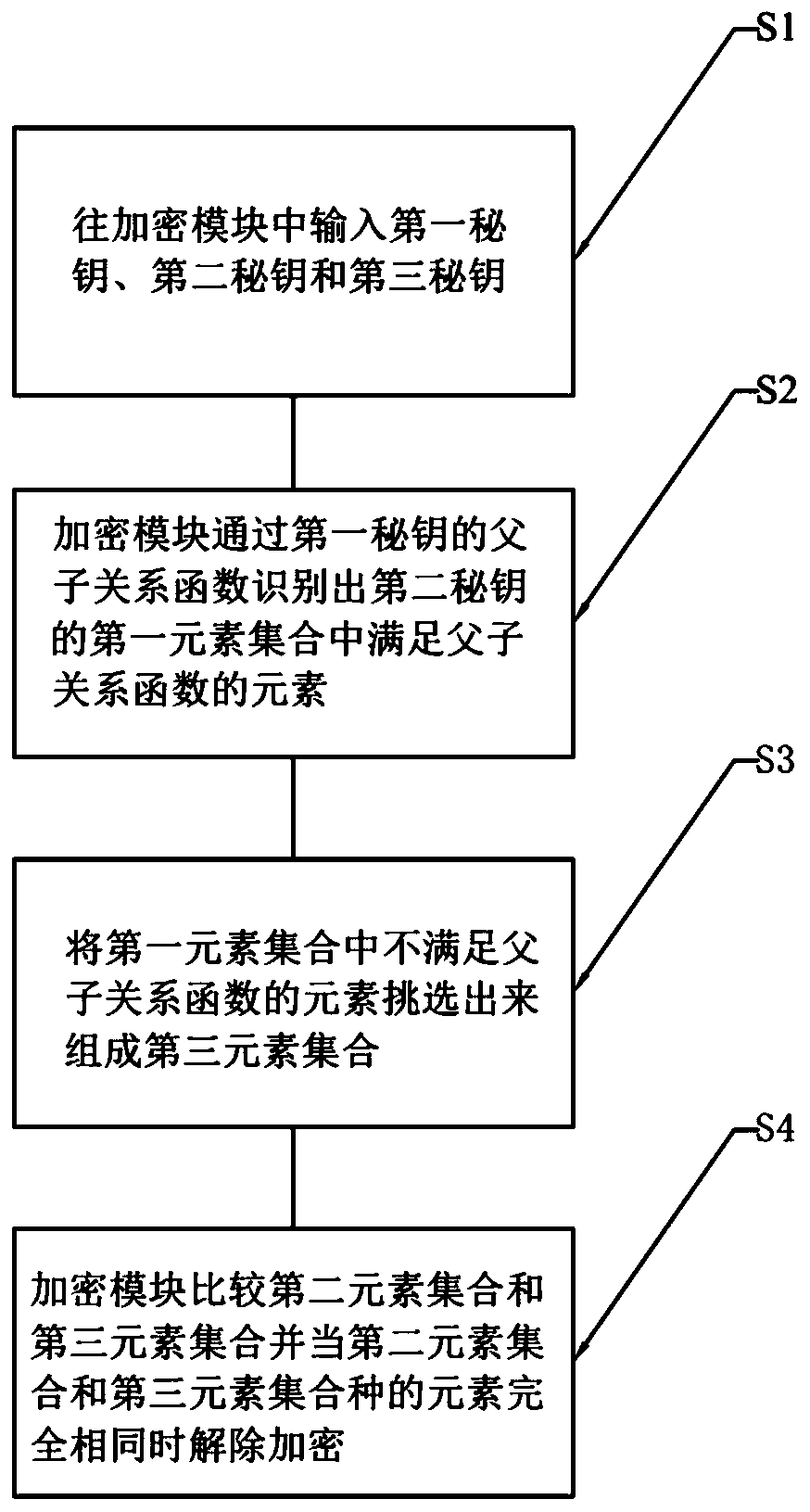
[0045] Such as figure 1 Shown is a three-party decryption method based on parent-child relationship verification of the present invention. The method is based on parent-child relationship verification. In an element set, for example, for the element set {A, B, C}, the elements in the element set satisfy f (A)=B, and f(B)=C, we believe that each element in the element set satisfies the parent-child relationship function f(x), and elements A, B, and C satisfy the parent-child relationship. Among them, element A is the parent element of element B, element B is the child element of element A, element B is the parent of element C, and element C is the child of element B. And the parent element of element A is not included in the element set, we call element A the root, and the child element of element C is not included in the element set, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com