Application layer malicious request detection method based on Transformer model
A detection method and application layer technology, applied in neural learning methods, biological neural network models, character and pattern recognition, etc., can solve the problems of improving the effectiveness and efficiency of malicious traffic detection methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
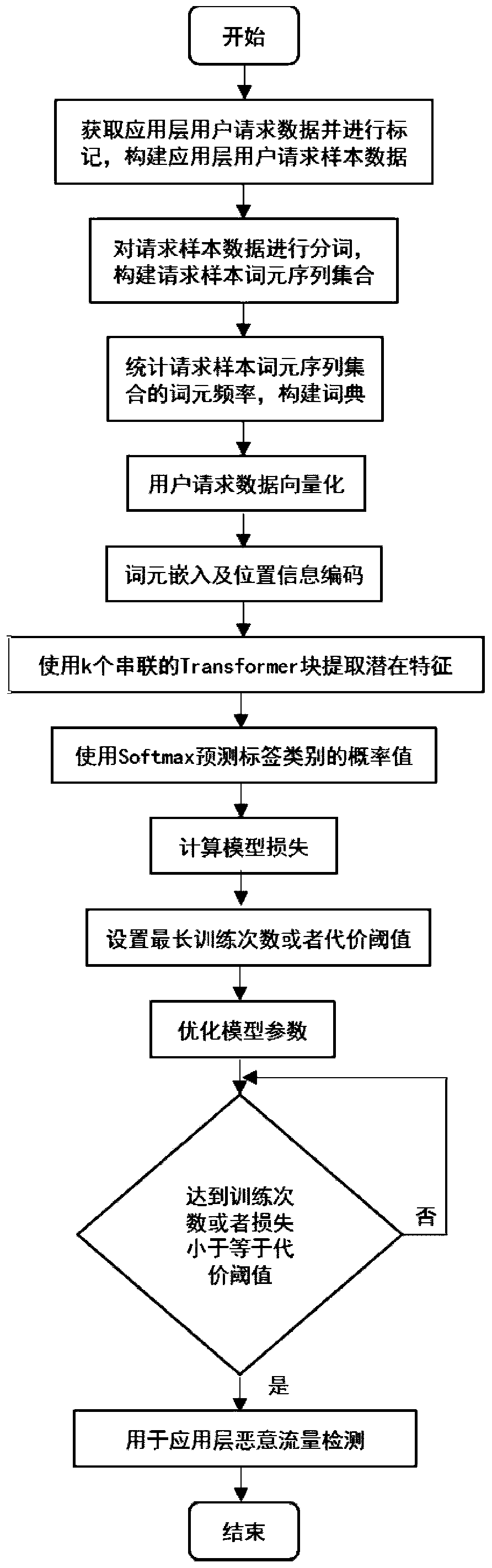
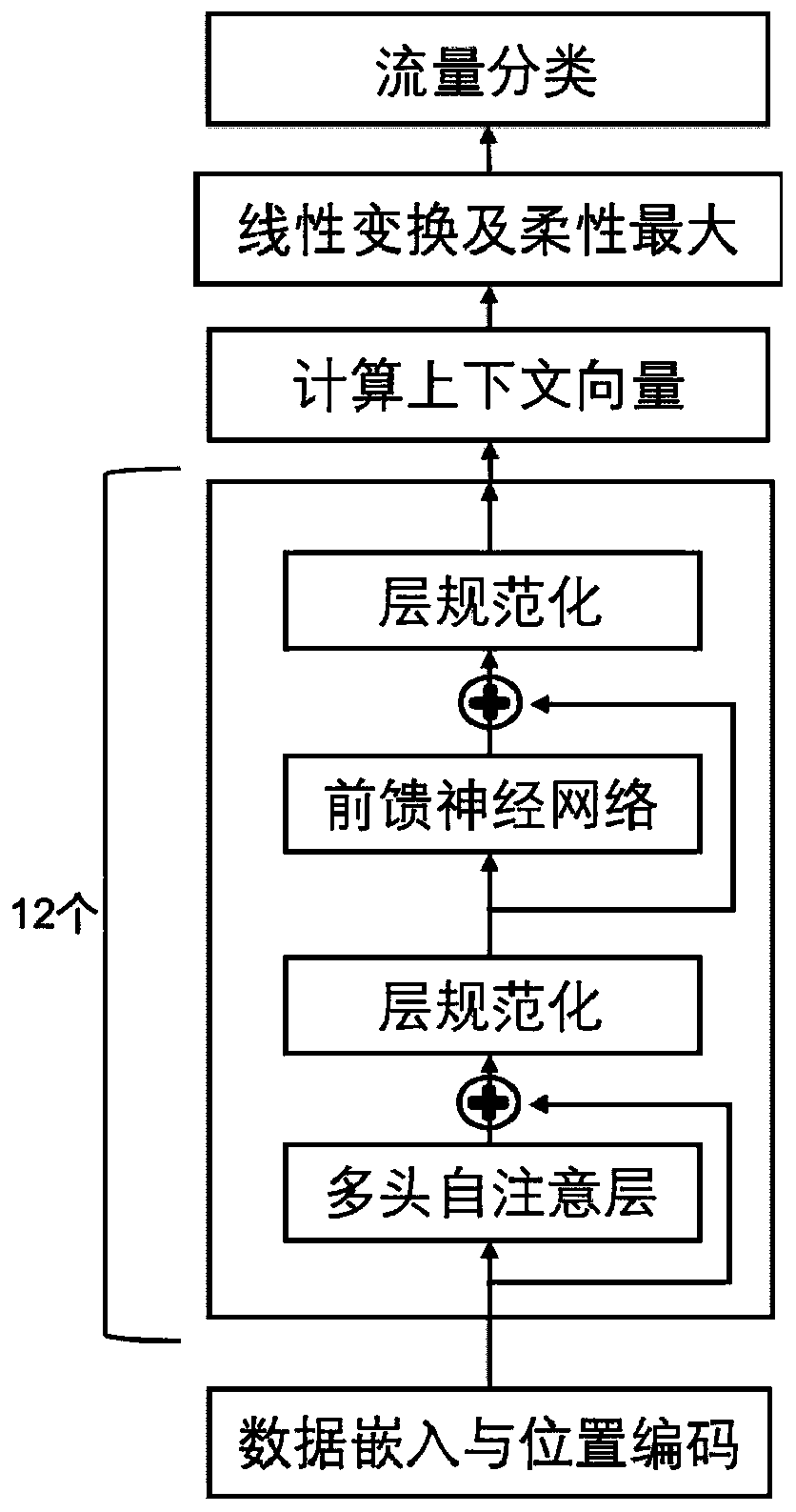
[0039] The specific implementation method of the inventive method is as follows:
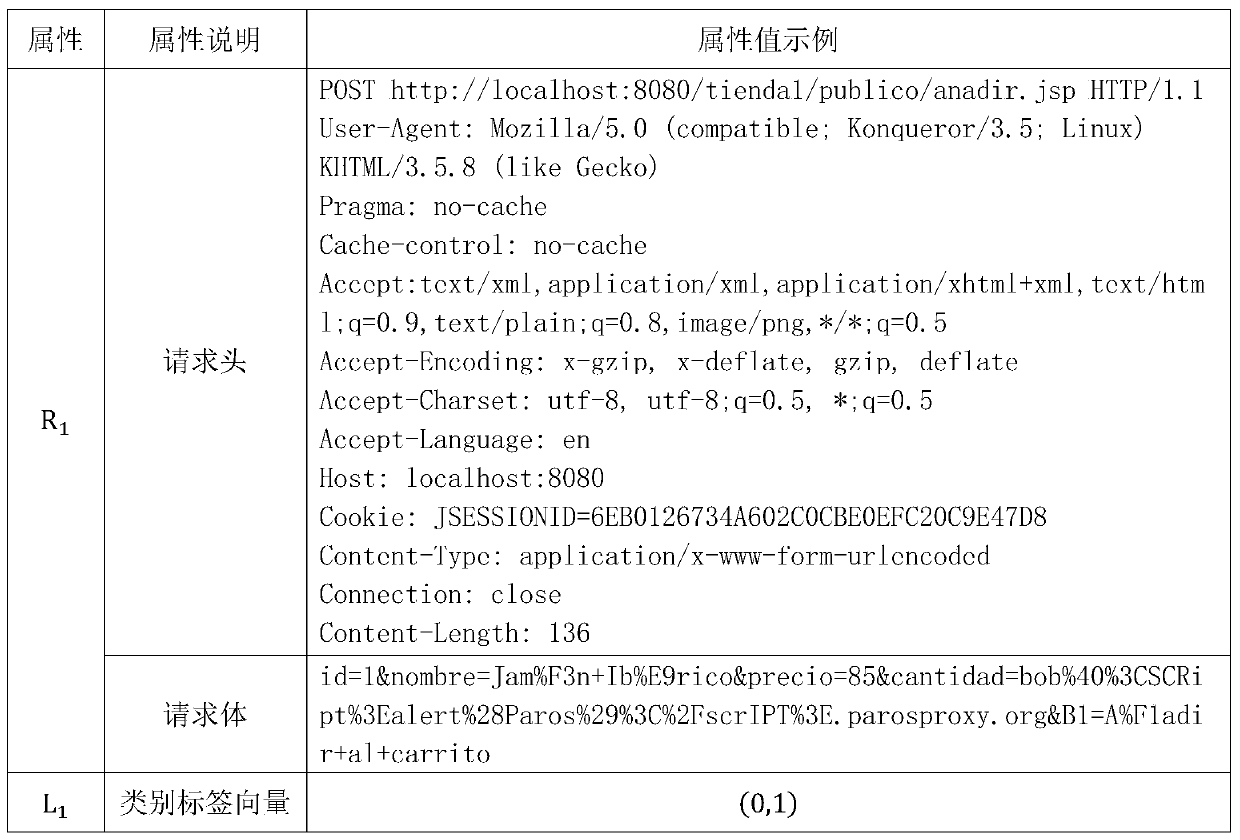
[0040] Step 1. The process of data acquisition. First, the application layer user request data recorded by the application service is obtained to form the application layer user request data set R, in which each application layer user request data R i The included features include request header and request body, the request header contains the data attribute information requested by the user, and the request body contains the data content information requested by the user; then according to a single application layer user request data R i , according to manual detection or other feasible detection methods, get its real category label vector L i , where the first element value represents R i is the probability value of a normal request, and the second element value represents R i is the probability value of a malicious request, L i The value of (0, 1) or (1, 0), (0, 1) represents R...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com