Underwater mobile node re-authentication method based on trust chain
A mobile node and re-authentication technology, applied in electrical components, transmission systems, etc., can solve the problems of high computational complexity, high communication overhead and storage overhead of underwater mobile node re-authentication, and achieve less communication overhead and reduce communication conflicts. and collision, the effect of low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
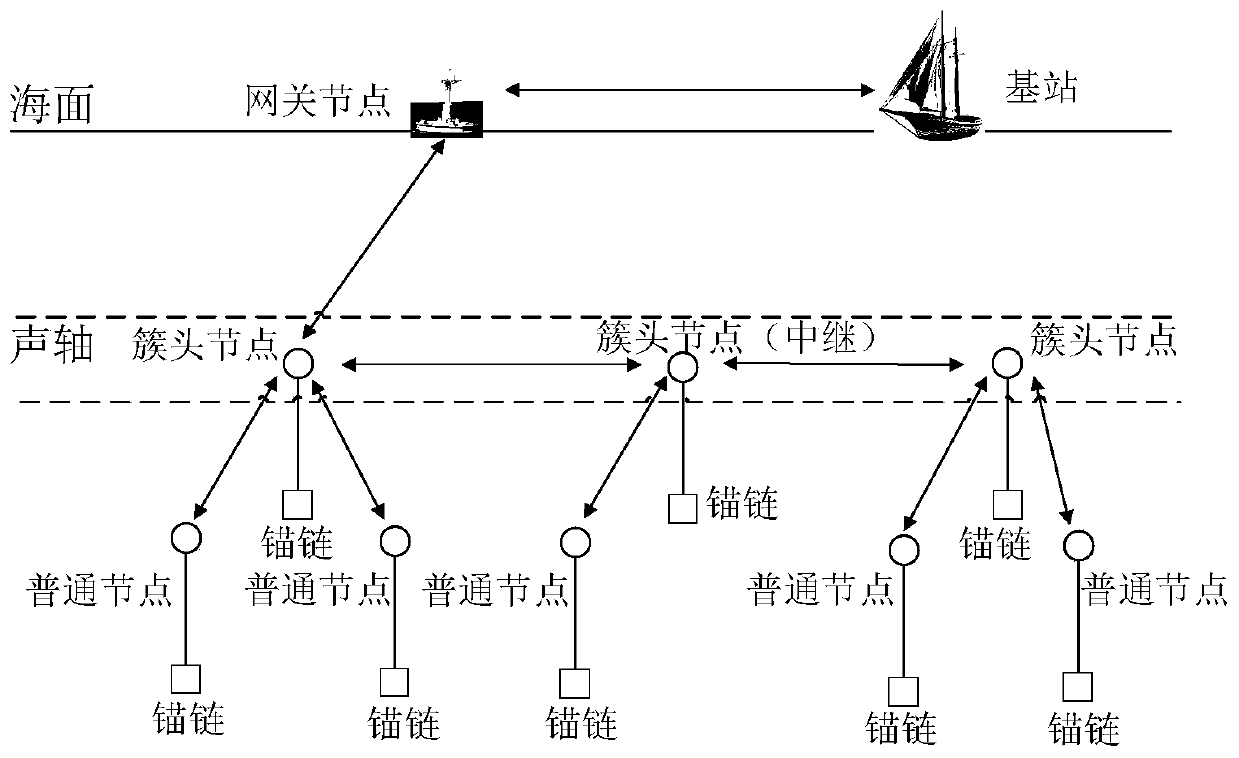
[0021] Such as figure 1 As shown, a trust chain-based underwater mobile node re-authentication method includes the following steps:
[0022] (1) The cluster head broadcasts periodically to check whether the member nodes have left the communication range of the node;
[0023] (2) ctr is a special character string specified by the cluster head for broadcast query, and the cluster head broadcast ciphertext M 0 , member nodes receive M 0 A response message M will be generated 1 And send it to the cluster head, after receiving the response from the member nodes, the cluster head thinks that the node is still in the communication coverage area of the cluster at this time; once the cluster head does not receive the feedback from the member nodes, the cluster head thinks that the node has moved ;
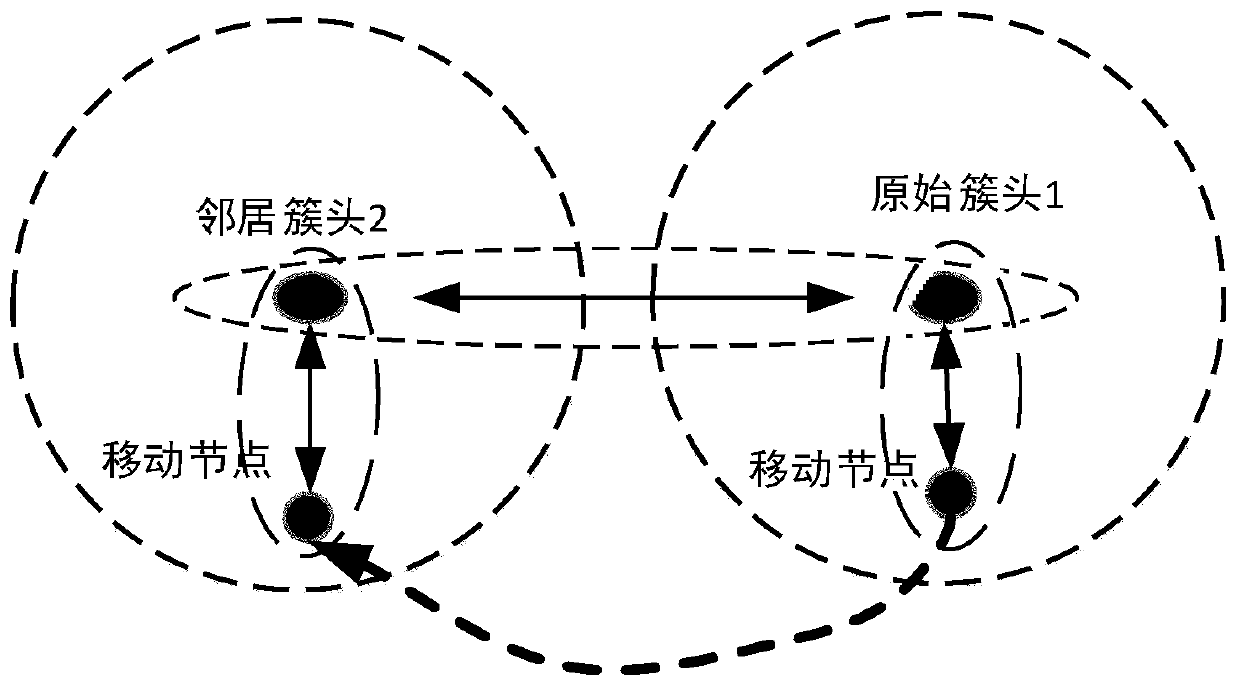
[0024] (3) The member node has moved and left the communication range of the cluster head. At this time, the cluster head will send a message to its neighbor cluster head to notify th...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap