Data sending protection method, device and system and computer readable storage medium
A technology for protecting devices and data, which is applied in the field of communication and can solve the problems of increasingly sensitive time delays and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
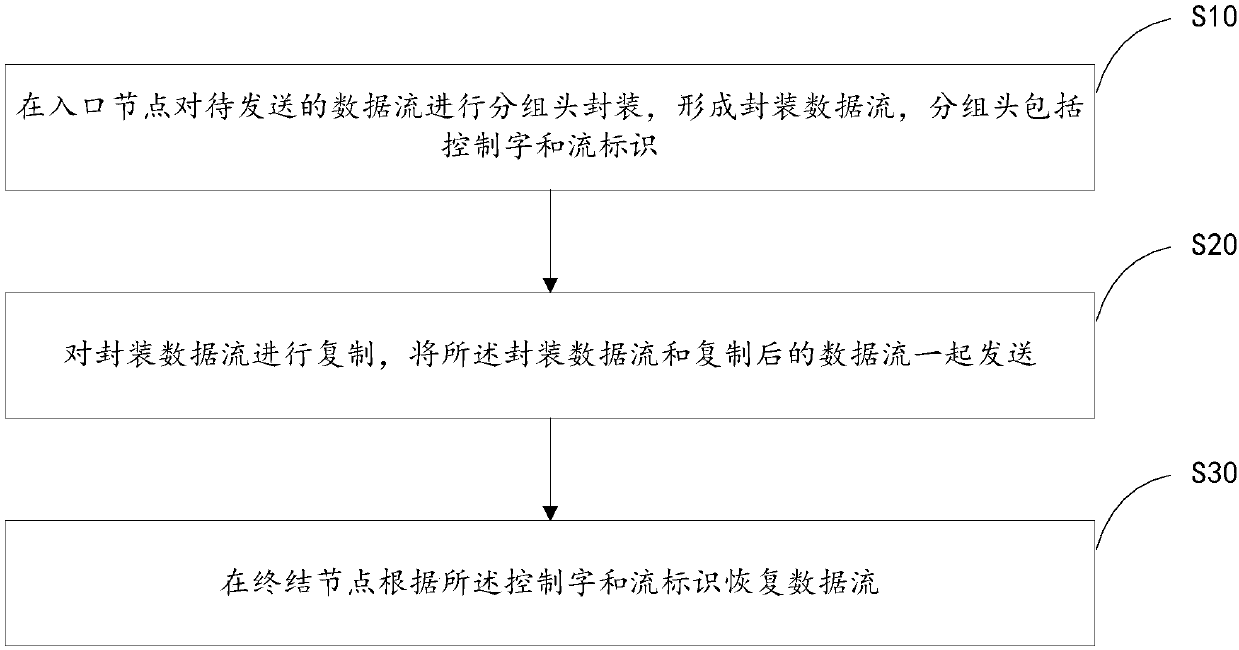
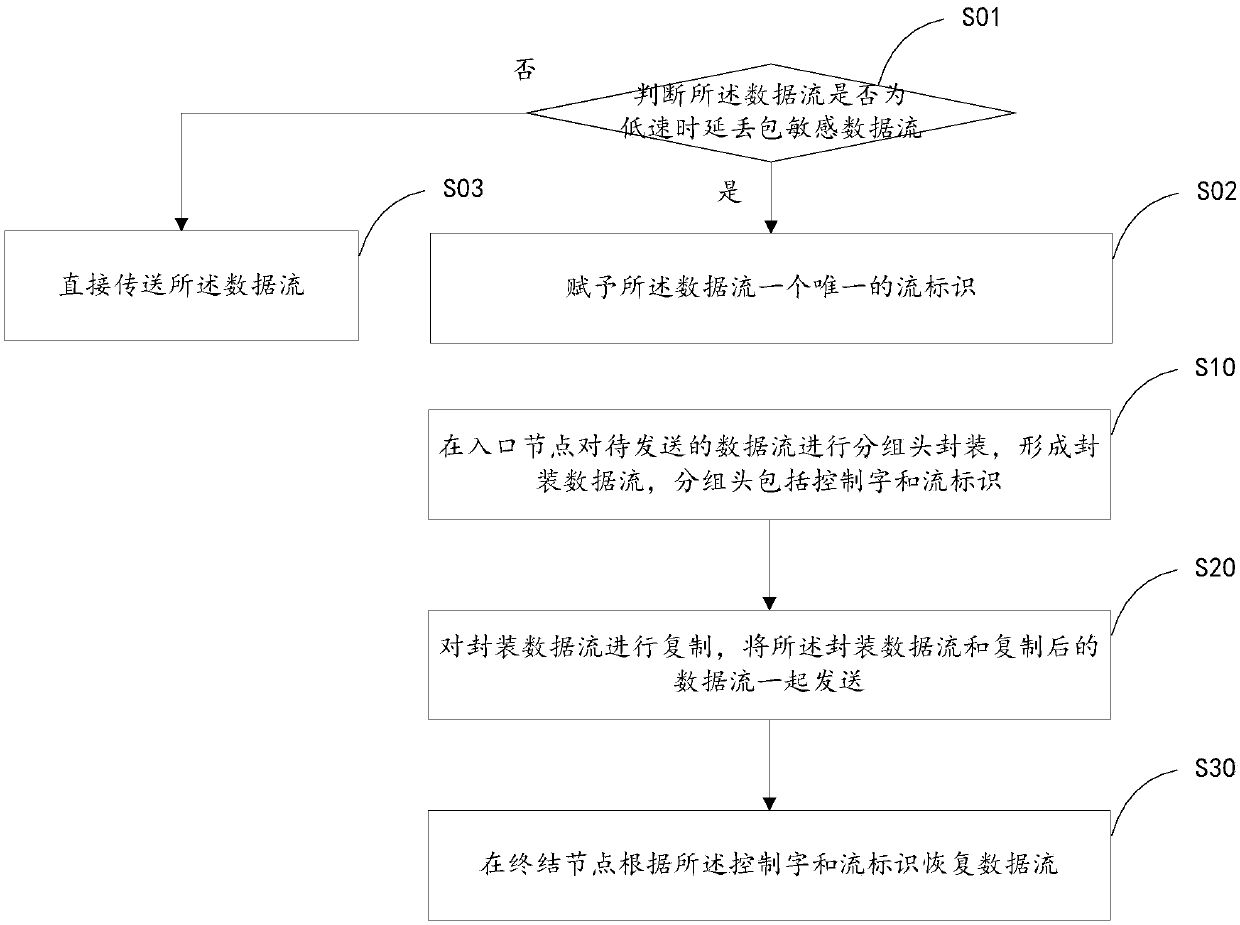
[0044] Such as figure 1 As shown, in this embodiment, a data transmission protection method includes:
[0045] S10. Perform packet header encapsulation at the ingress node on the data flow to be sent to form an encapsulated data flow, where the packet header includes a control word and a flow identifier;
[0046] S20. Copy the encapsulated data stream, and send the encapsulated data stream and the copied data stream together;
[0047] S30. Recover the data flow at the termination node according to the control word and the flow identifier.
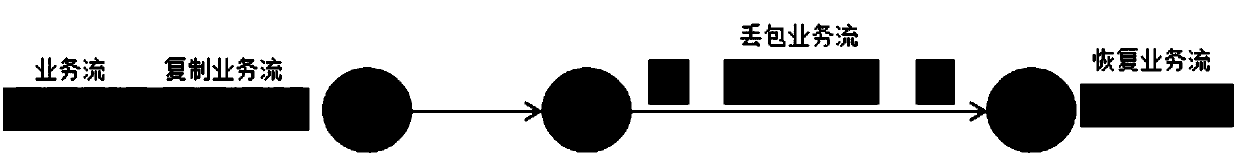
[0048] In this embodiment, by redundantly duplicating the data flow of the low-speed deterministic network service on the same path, the influence of the packet loss event is reduced or even eliminated, and the service delay is reduced.
[0049] In this embodiment, the duplication and recovery of data streams (also referred to as service streams) are all completed at the edge network nodes, and the ingress node is the edge node at the sen...
Embodiment 2
[0069] Such as Figure 6 As shown, in this embodiment, a data transmission protection device includes:
[0070] The encapsulation module 10 is used to perform packet header encapsulation on the data flow to be sent at the ingress node to form an encapsulated data flow, and the packet header includes a control word and a flow identifier;
[0071] The copying and sending module 20 is used to copy the encapsulated data stream, and send the encapsulated data stream together with the copied data stream;
[0072] A restoration module 30, configured to restore the data flow at the termination node according to the control word and the flow identifier.
[0073] In this embodiment, by redundantly duplicating the data flow of the low-speed deterministic network service on the same path, the influence of the packet loss event is reduced or even eliminated, and the service delay is reduced.
[0074] In this embodiment, the duplication and recovery of data streams (also referred to as se...
Embodiment 3
[0095] In this embodiment, a data transmission protection system includes a memory, a processor, and at least one application program stored in the memory and configured to be executed by the processor, and the application program is configured to use To implement the data transmission protection method described in the first embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com