Database table field encryption and decryption method and data server
A technology of data server and encryption method, which is applied in the database field, can solve the problem of low security of database table fields, and achieve the effect of improving data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0080] Example 1
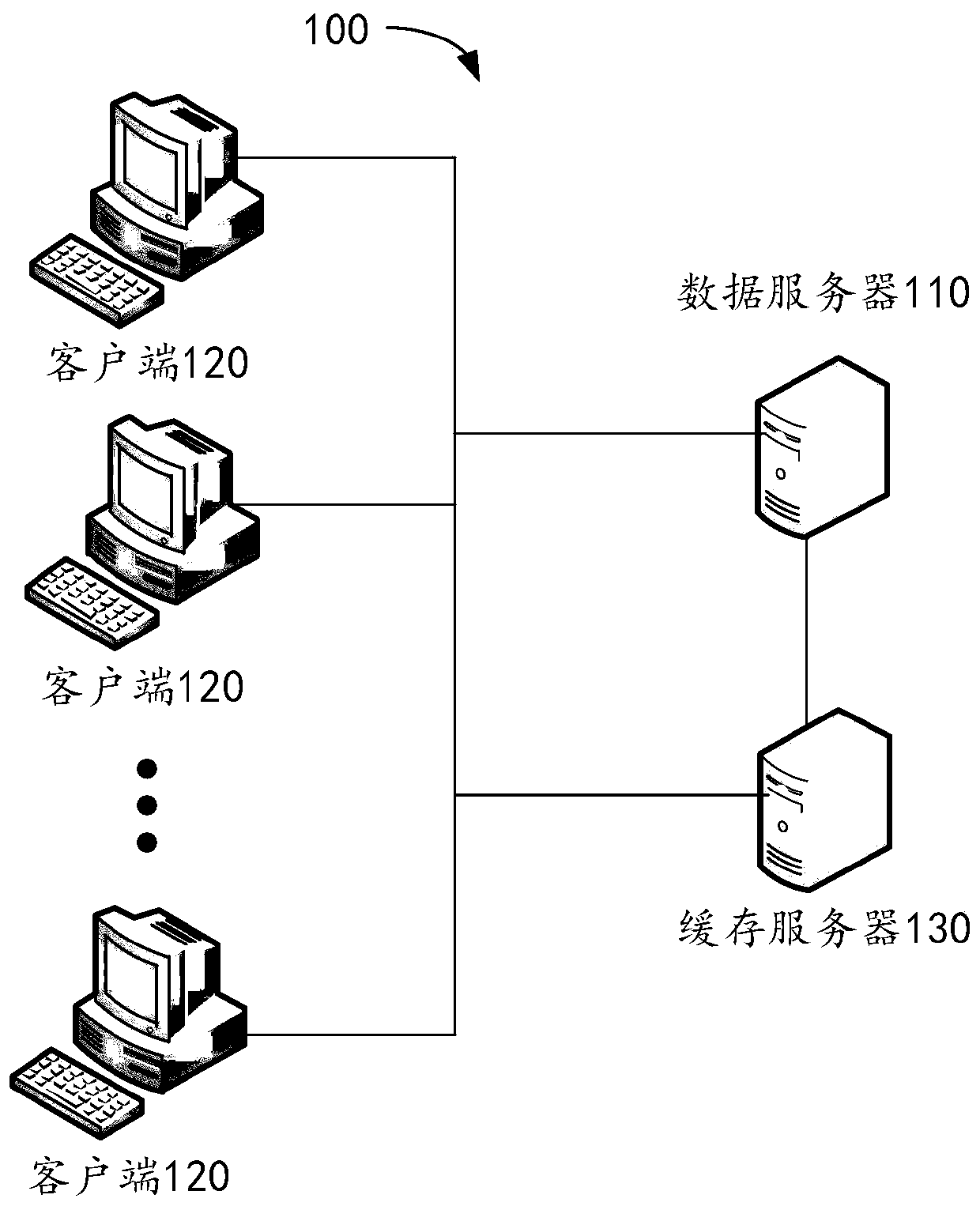
[0081] see figure 2 , figure 2 It is a schematic flowchart of an encryption method for a database table field provided by an embodiment of the present invention; wherein, the encryption method for a database table field is applied to a data server, and the data server is connected to at least one client for receiving the client The data query command sent by the terminal.
[0082] like figure 2 As shown, the encryption methods of the database table fields include:
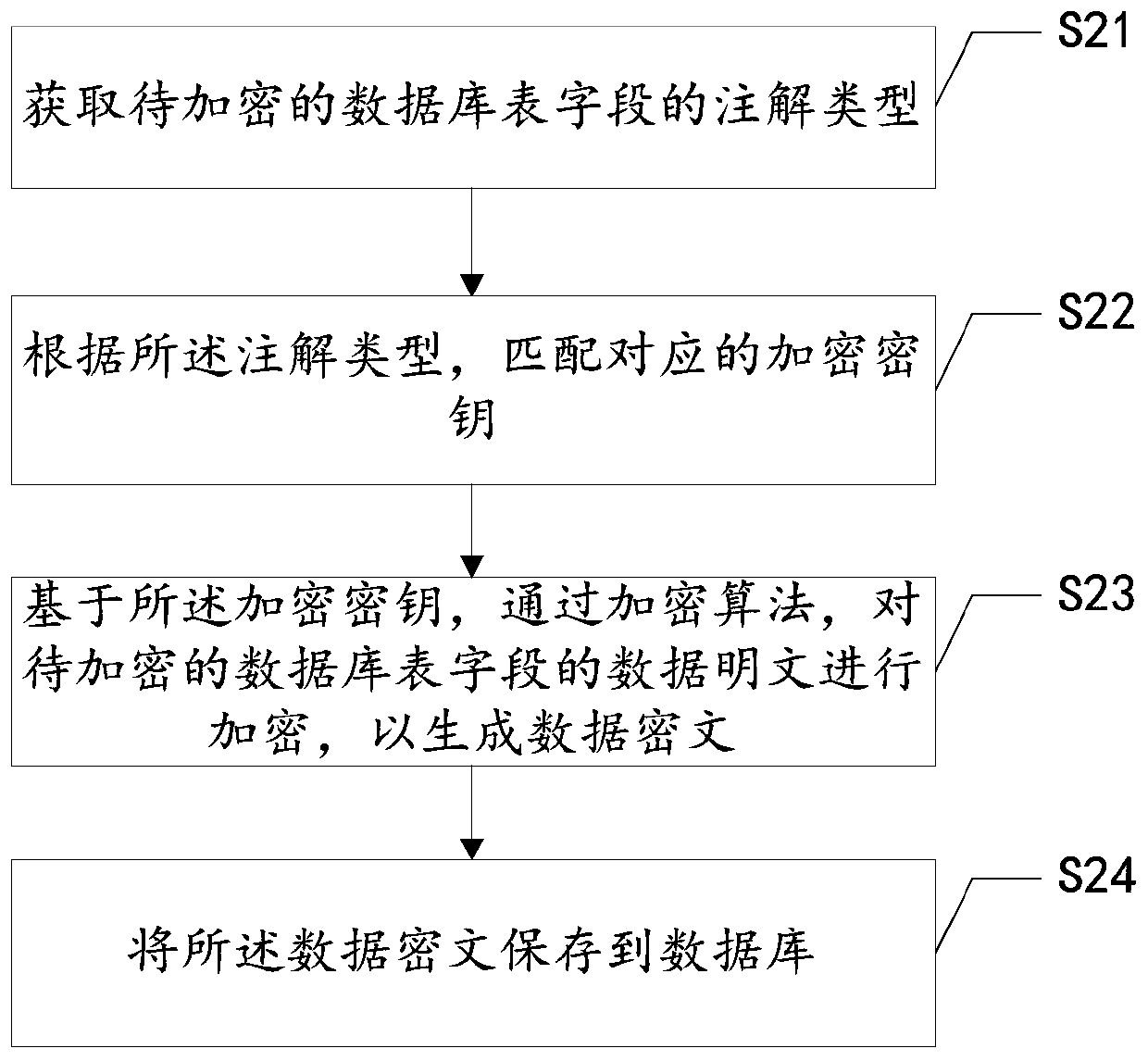
[0083] Step S21: obtaining the annotation type of the database table field to be encrypted;
[0084] Specifically, the data server adds annotation types to the table fields that need to be encrypted by the database operation layer. The annotation types include: settlement account type, certificate number type, and four-element type of bank card. The four elements of bank card include: bank card The name, bank card number, reserved mobile phone number and ID number of the cardholder. In a...
Example Embodiment
[0135] Embodiment 2
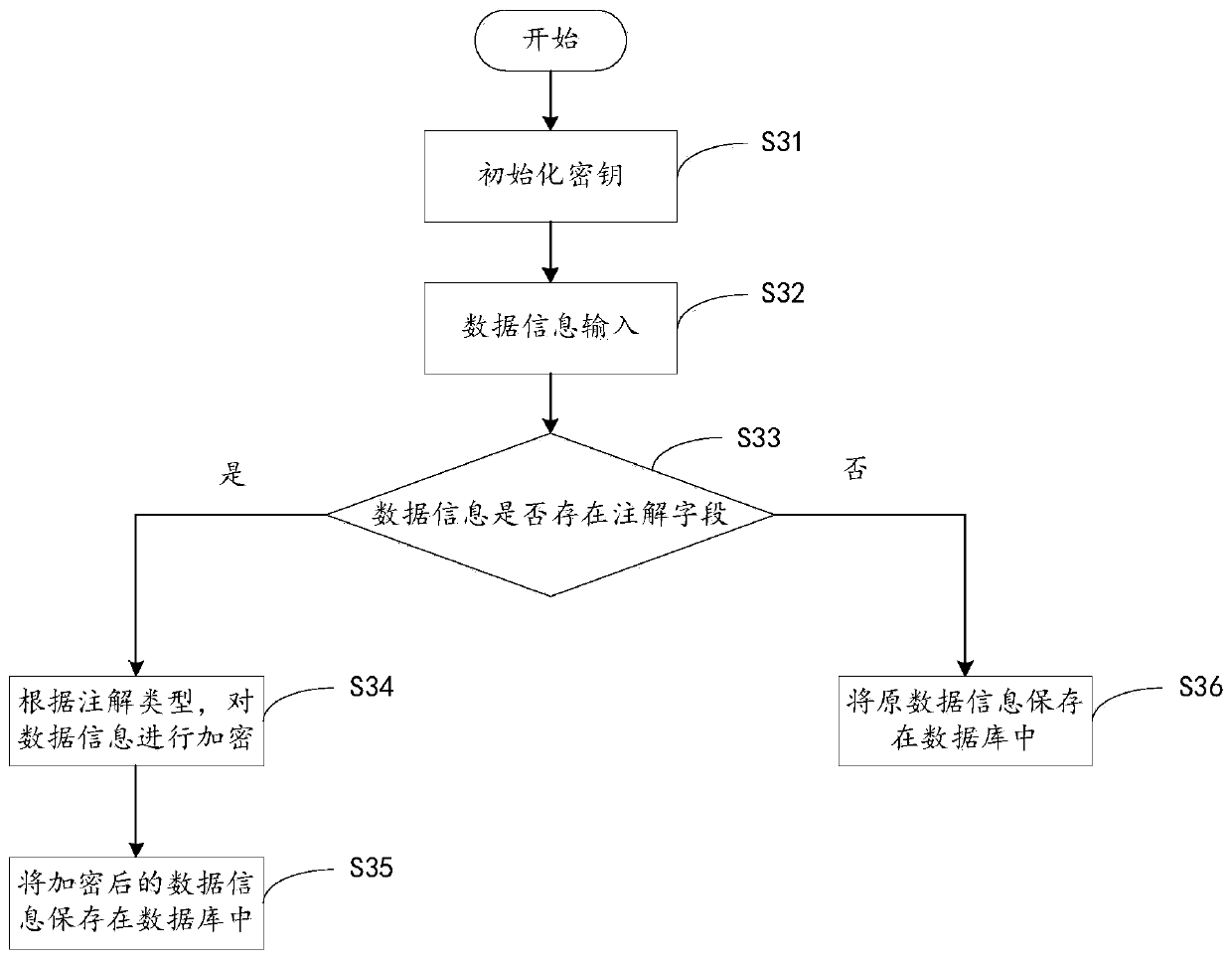
[0136] see again Figure 4 , Figure 4 It is a schematic flowchart of a method for decrypting a database table field provided by an embodiment of the present invention;
[0137] like Figure 4 As shown, the decryption method of the database table field, applied to the data server, includes:
[0138] Step S41: receiving a data query instruction sent by the client;
[0139] Specifically, the client requests data from the data server through a data query instruction. For example, the data query instruction is an SQL statement, wherein after the SQL statement is executed by the data server, the data is retrieved from the database of the data server. The data is read by query in the data server, and the data returned by the data server is placed in the result set. Among them, the SELECT statement is used to select rows from the database and view standard methods in the result set, and the java.sql.ResultSet interface represents the result set of the databas...
Example Embodiment
[0154] Embodiment 3
[0155] The embodiment of the present invention also provides an encryption device for database table fields, please refer to Figure 5 , Figure 5 It is a schematic structural diagram of a database table field encryption device provided by an embodiment of the present invention;
[0156] like Figure 5 As shown, the encryption device 50 of the database table field, applied to the data server, includes:
[0157] The annotation type obtaining unit 51 is used to obtain the annotation type of the database table field to be encrypted;
[0158] An encryption key matching unit 52, configured to match the corresponding encryption key according to the annotation type;
[0159] The data ciphertext generating unit 53 is configured to encrypt the data plaintext of the database table field to be encrypted by the encryption algorithm based on the encryption key to generate the data ciphertext;
[0160] The data ciphertext saving unit 54 is configured to save the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com