Visitor password generation method, verification method, server and intelligent door lock
A technology of visitor password and verification method, applied in the field of visitor password generation method, verification method, server and smart door lock, can solve the problem that the visitor password cannot be determined correctly, the door cannot be opened normally, and the increase of the visitor password is intercepted or stolen. Risks and other issues to achieve the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
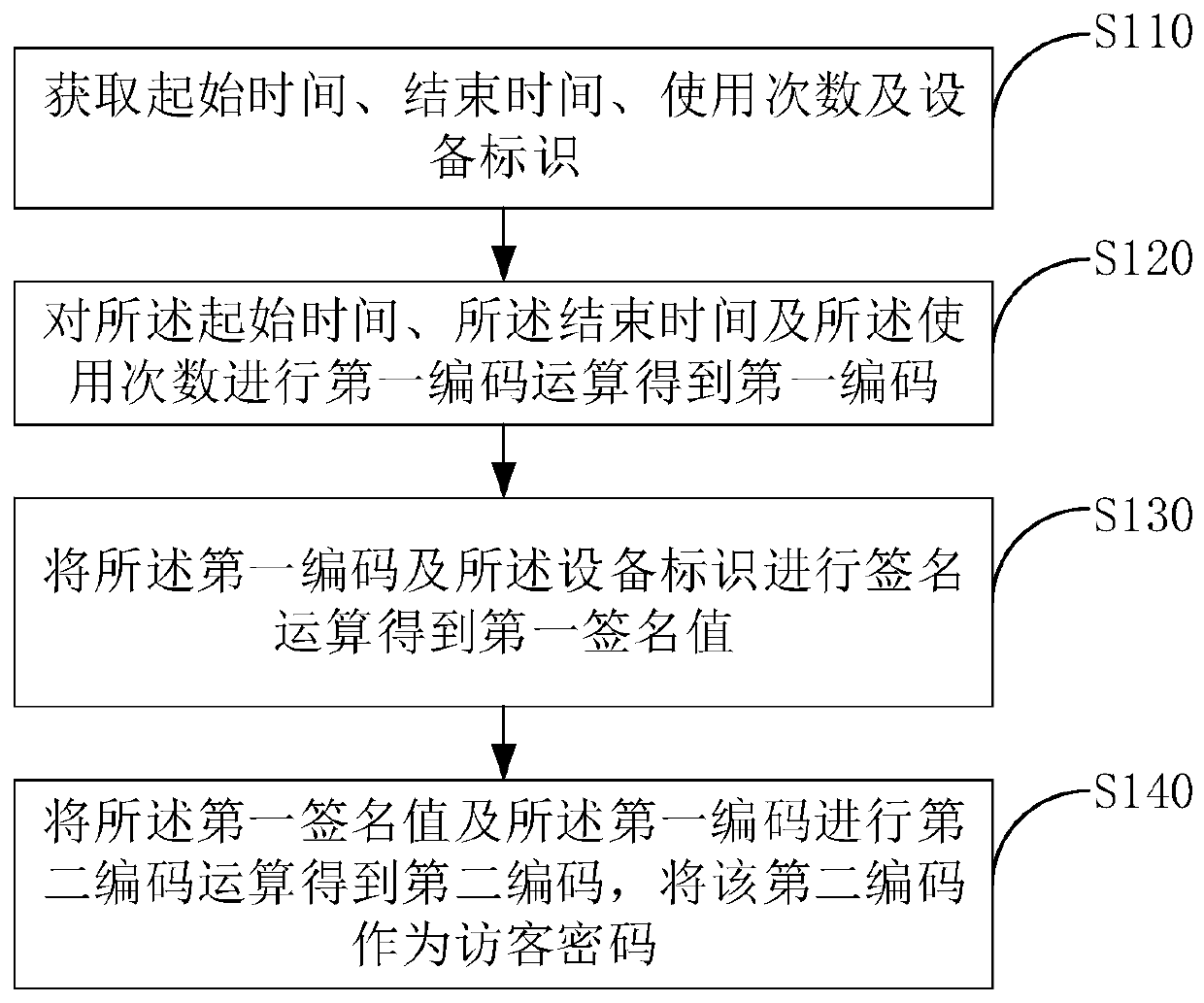
[0065] figure 1 A schematic flowchart of a method for generating a guest password provided by the first embodiment of the present invention is shown.
[0066] The method for generating a guest password comprises the steps of:
[0067] In step S110, start time, end time, usage times and device identification are obtained.
[0068] Specifically, the guest password generation method can be applied to a server. The user terminal sends a visitor password application to the server, wherein the visitor password application includes a start time, an end time, the number of times of use and the device identification of the smart door lock that the visitor wants to open.
[0069] In step S120, a first coding operation is performed on the start time, the end time, and the number of times of use to obtain a first code.
[0070] Further, step S120 includes:
[0071] Split the start time into a start hour unit and a start year-month-day unit; split the end time into an end-hour unit and...
Embodiment 2
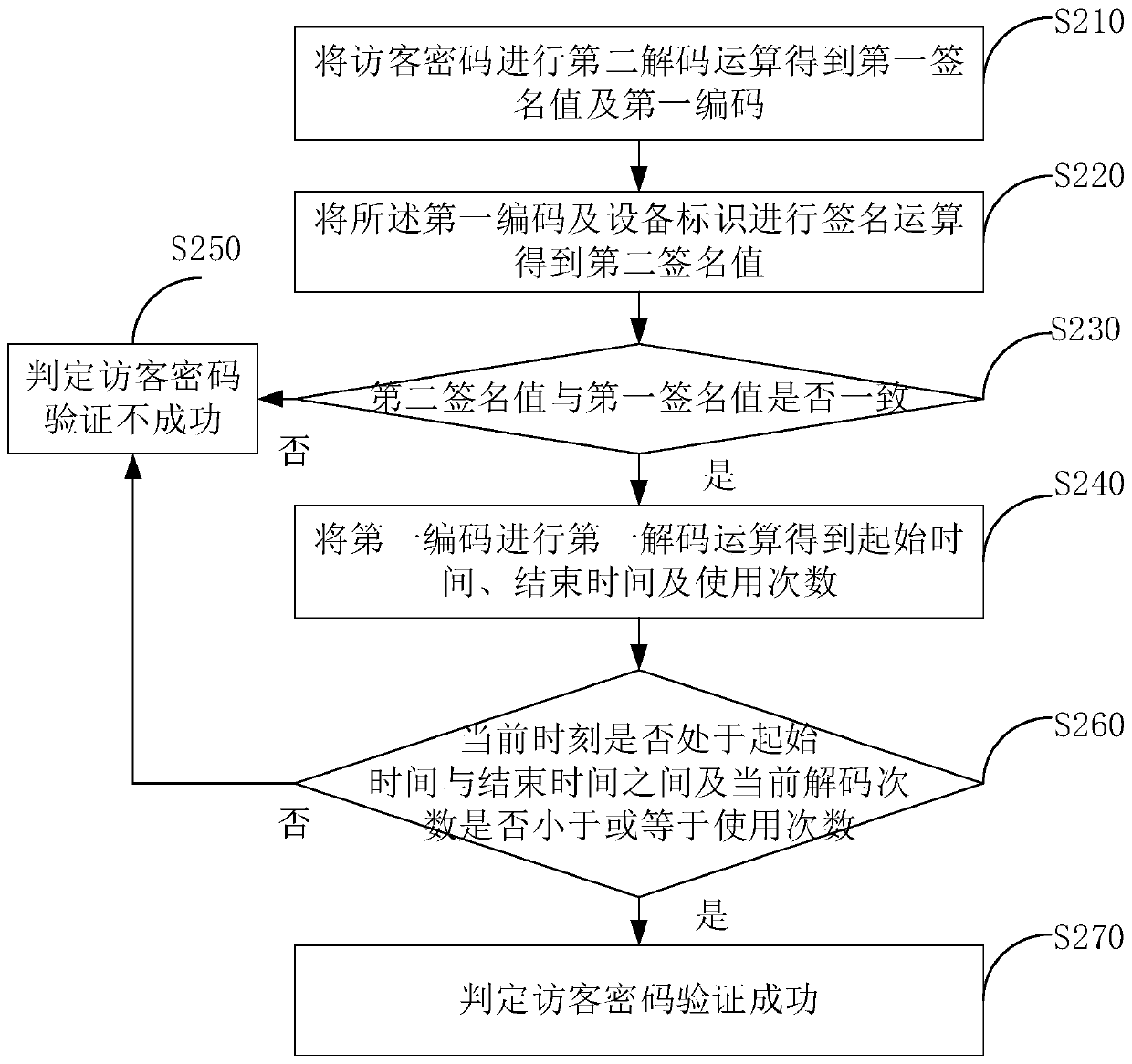
[0112] figure 2 A schematic flowchart of a visitor password verification method provided by the second embodiment of the present invention is shown.
[0113] The visitor password verification method can be applied to a smart door lock, and is suitable for decrypting the visitor password generation method in Embodiment 1.
[0114] The first decoding operation in this embodiment is the inverse operation corresponding to the first encoding operation in embodiment 1, the second decoding operation is the inverse operation corresponding to the second encoding operation in embodiment 1, and the third decoding operation is Corresponds to the inverse operation of the third encoding operation in Embodiment 1.
[0115] The visitor password verification method includes the following steps:
[0116] In step S210, the visitor password is subjected to a second decoding operation to obtain a first signature value and a first code.
[0117] Specifically, after the server generates the visi...
Embodiment 3
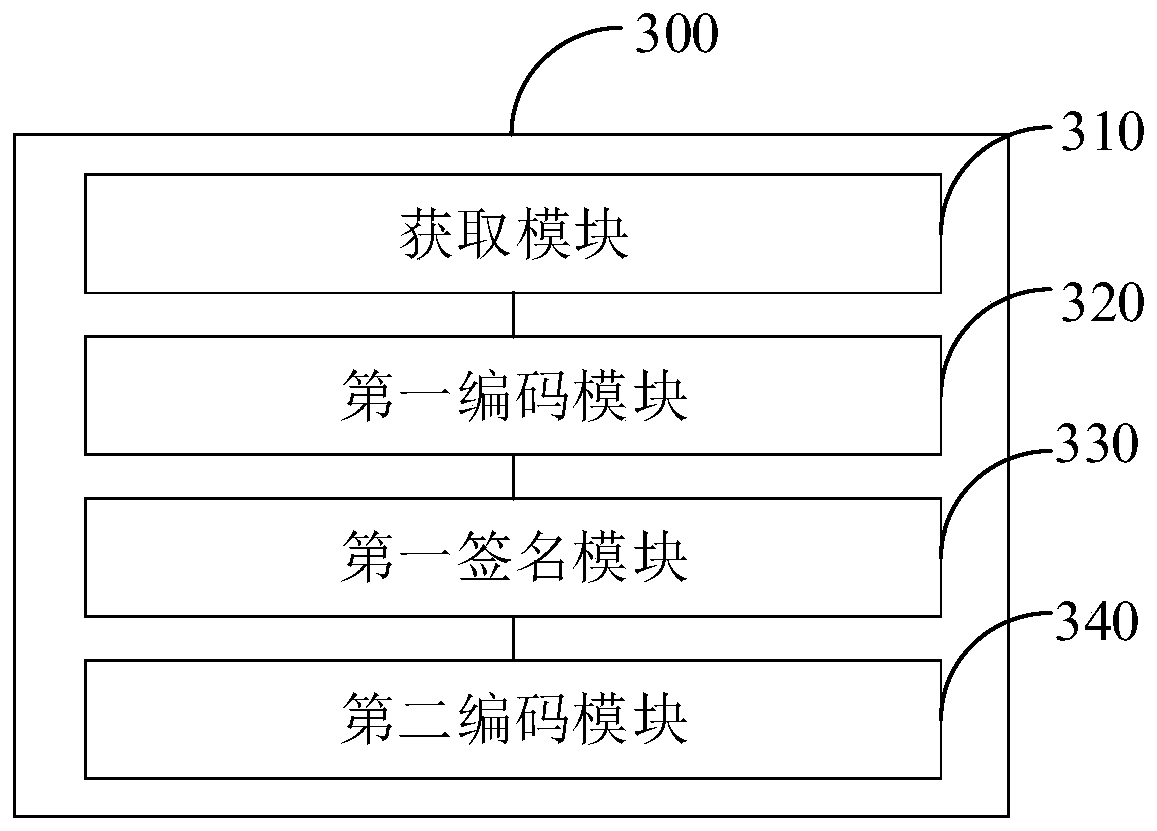
[0152] image 3 A schematic structural diagram of a device for generating a guest password provided by the third embodiment of the present invention is shown.
[0153] The visitor password generation device 300 is corresponding to the visitor password generation method in Embodiment 1, and each option in Embodiment 1 is also applicable to this embodiment.
[0154] The visitor password generation device 300 includes an acquisition module 310 , a first encoding module 320 , a first signature module 330 and a second encoding module 340 .
[0155] The acquiring module 310 is configured to acquire the start time, the end time, the number of times of use and the device identification.
[0156] The first coding module 320 is configured to perform a first coding operation on the start time, the end time, and the usage times to obtain a first code.
[0157]The first signature module 330 is configured to perform a signature operation on the first code and the device identifier to obta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com