File encryption and decryption method
A file encryption and file technology, applied in the direction of instruments, electrical digital data processing, digital data protection, etc., can solve the problem that the encryption and decryption file method is easy to be cracked, and achieve the effect of ensuring that it will not be deciphered
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] The present embodiment provides a kind of file encryption method, comprises the following steps:
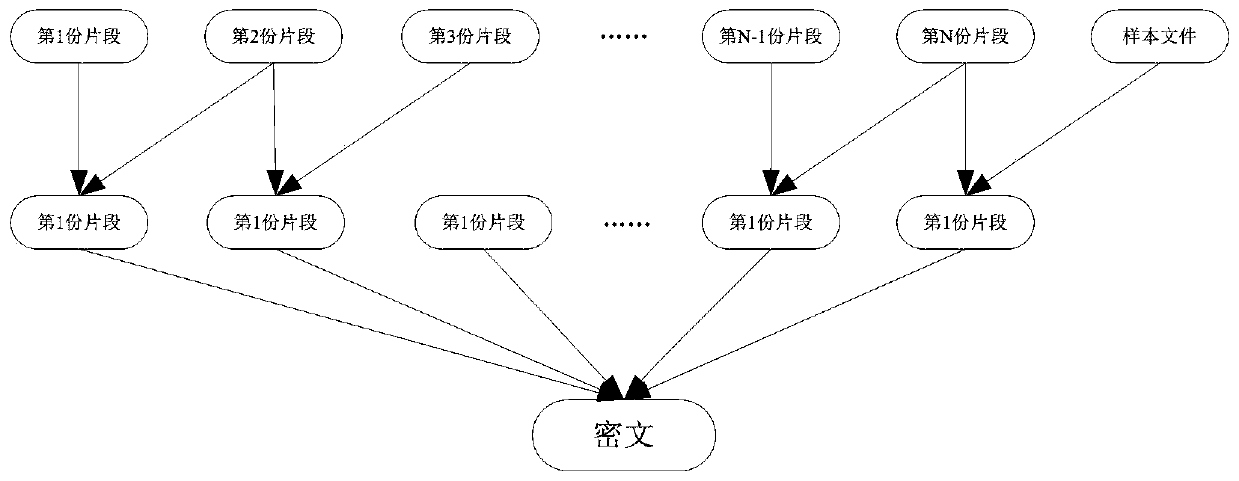
[0047] Step 1, read the file to be encrypted, the length of the file to be encrypted is L; randomly select a section of file with a length of L from the sample file as the current file, and perform an XOR operation between the file to be encrypted and the current file to obtain an intermediate file, Where L is greater than or equal to 1, and the unit is byte;
[0048] Step 2, randomly generate n fragment lengths, and divide the intermediate file into n fragments according to the fragment lengths;
[0049] Step 3, disrupting the order of the n fragments in the intermediate file to obtain the current intermediate file;
[0050] Step 4, XOR operation is performed on the n fragments of the current intermediate file to obtain the preliminary intermediate file;
[0051] Such as figure 1 shown, including:
[0052] Step 41, let i=1, i is the encryption cycle factor;
[0053] ...
Embodiment 2
[0066] This embodiment provides a file decryption method, comprising the following steps:
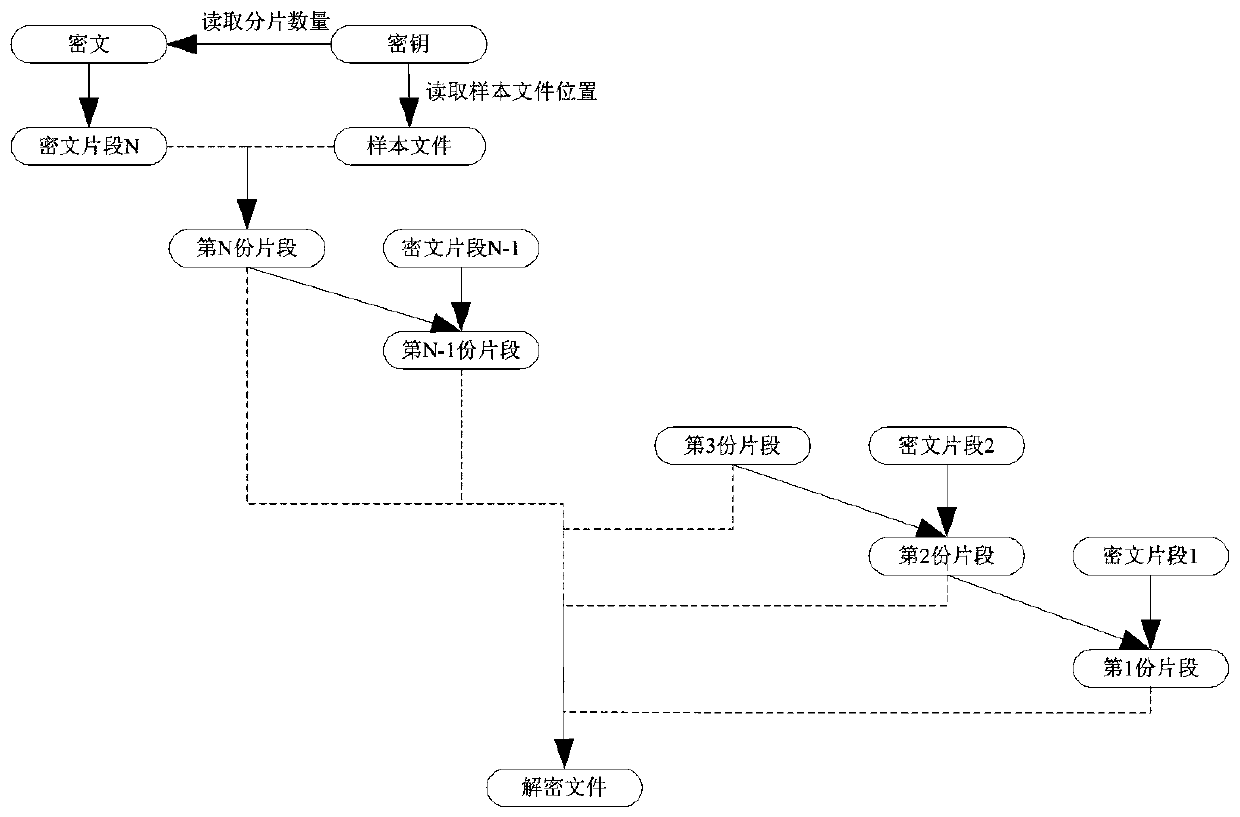
[0067] Step 1, read the encrypted file in the key, the encrypted file includes m fragments, and use the encrypted file as the current decrypted file;
[0068] Step 2, decrypt the m fragments in the current decrypted file to obtain the plaintext file;
[0069] Such as figure 2 shown, including:
[0070] Step 21, randomly obtain a piece of file from the sample file as the current decrypted slice, and perform an XOR operation on the mth slice in the current decrypted file and the current decrypted slice to obtain the m'th slice of the plaintext file;
[0071] Step 22, let j=m-1, j is decryption cycle factor;
[0072] Step 23, performing an XOR operation on the jth fragment in the current decrypted file and the (j+1)'th fragment of the plaintext file to obtain the j'th fragmentation of the plaintext file;
[0073] Step 24, repeat step 23, until j=1, obtain plaintext file, described pla...
Embodiment 3
[0087] This embodiment provides a file encryption and decryption method, such as Figure 4 As shown, the file encryption method provided in Embodiment 1 and the file decryption method provided in Embodiment 2 are included.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com