A service authentication method, device and medium
A technology of business authentication and authentication, which is applied in the field of microservices, can solve problems such as easy to be attacked, business data security risks, and network requests are easy to be tampered with, so as to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
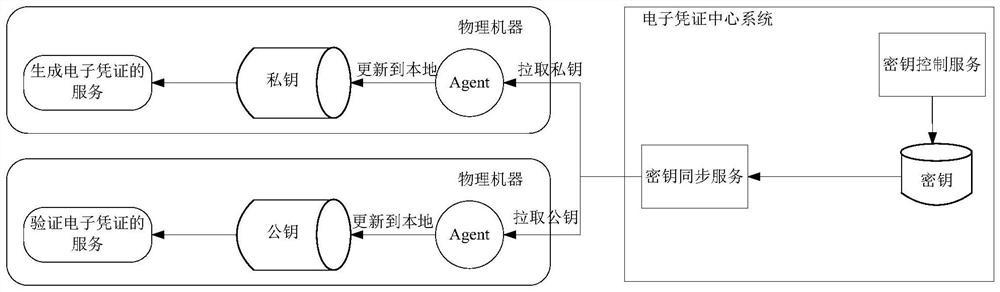
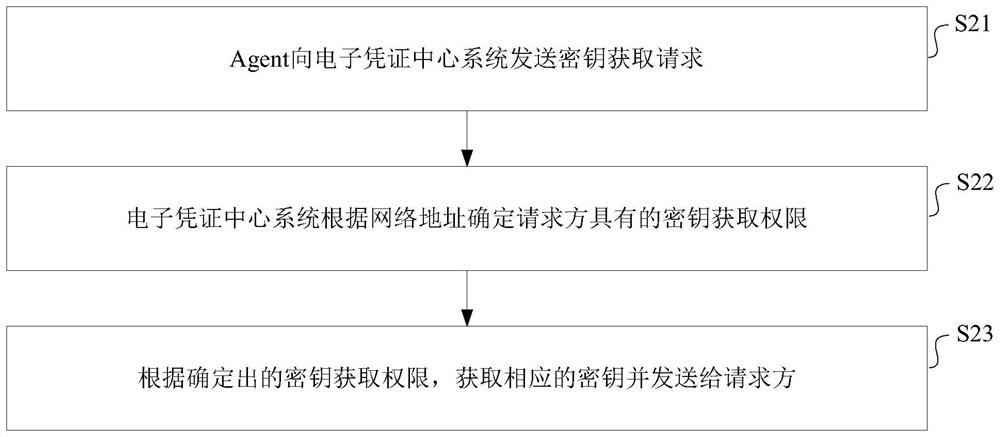
[0226] In another embodiment, the first electronic certificate may further include at least one of the following verification information: the first user identification, the generation time of the first electronic certificate, the first business parameter and the type of the first electronic certificate. In this implementation, after the current microservice uses the stored public key to successfully decrypt the first electronic certificate, it can further verify the verification information obtained during decryption. If all the verification information is successfully verified, it is determined that the The verification of the first electronic certificate passes, and if the verification of one piece of verification information fails, it is determined that the verification fails.
[0227] During specific implementation, for the first user ID, the current microservice can compare whether the first user ID is the same as the second user ID carried in the received user processing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com