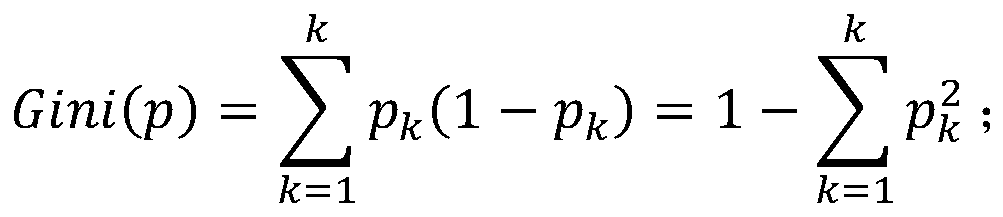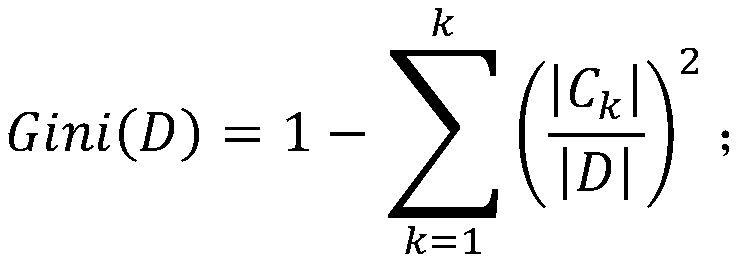Industrial control network brute force cracking flow detection method based on random forest
A random forest and industrial control network technology, applied in the field of network security, can solve the problem of few applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
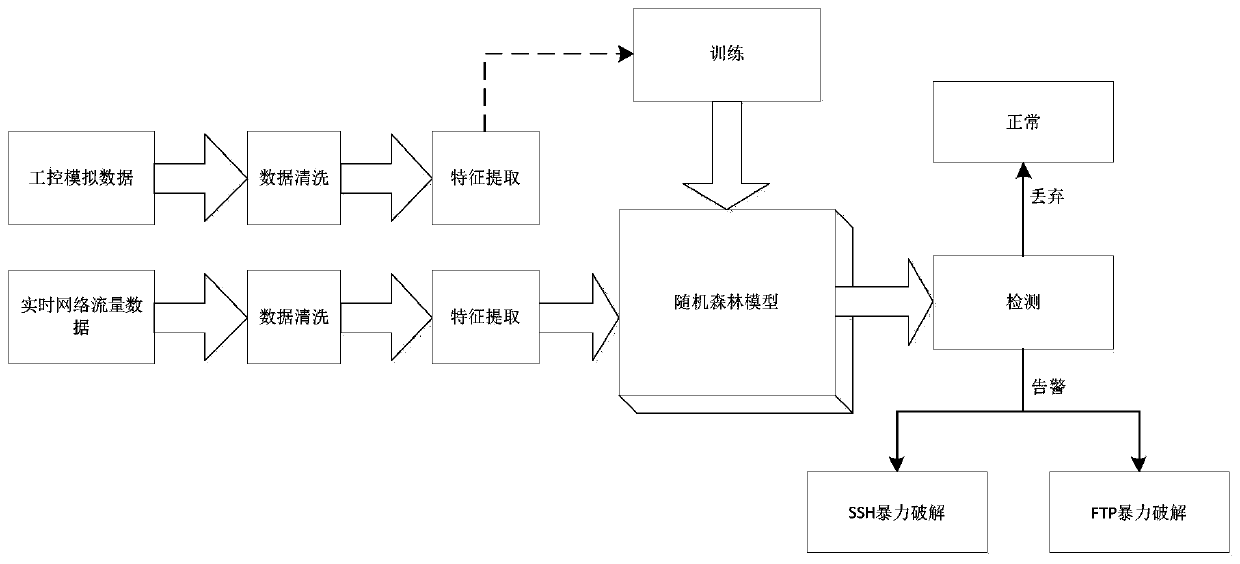
[0024] A random forest-based industrial control network brute force cracking traffic detection method of the present invention mainly includes two parts:
[0025] First, train the brute force detection model based on random forest;
[0026] First of all, it is necessary to prepare the training set, obtain the industrial control network traffic data after brute force cracking by simulating the industrial control network environment, filter out the data that cannot extract the complete traffic characteristics, and then extract the multi-dimensional traffic characteristics from the industrial control simulated traffic data after data cleaning as training set;
[0027] Secondly, use the training set to train the random forest; the nodes on the decision tree of the random forest represent the traffic characteristics, and the value range of the traffic characteristics represents the category of the network traffic data is brute force or normal. The decision trees in the random fore...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap