Data encryption and decryption method and device
A data encryption and decryption algorithm technology, applied in the field of information security, can solve the problems of single, fixed, and easily cracked static keys and encryption algorithms, and achieve the effect of improving the efficiency of encryption and decryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
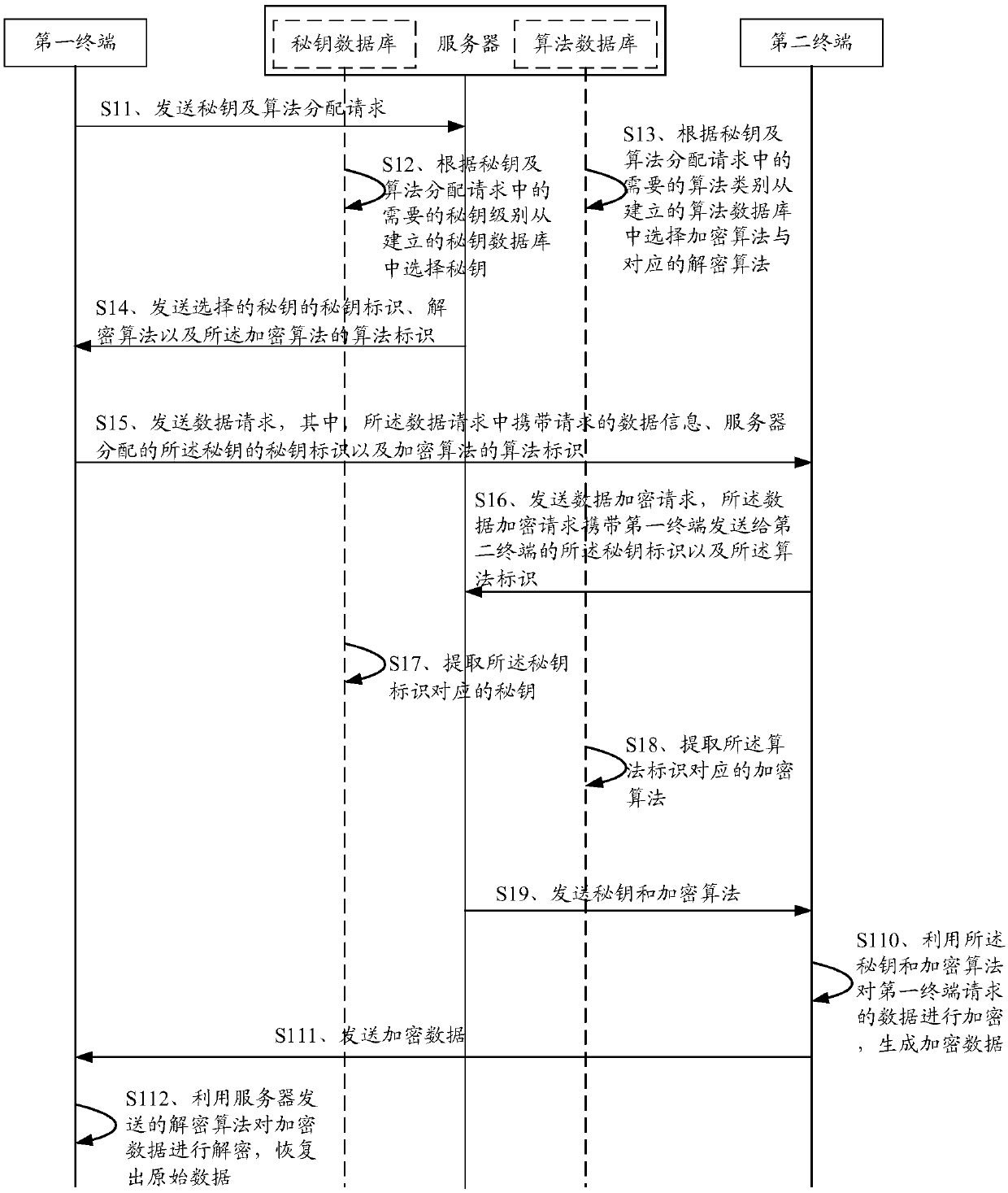
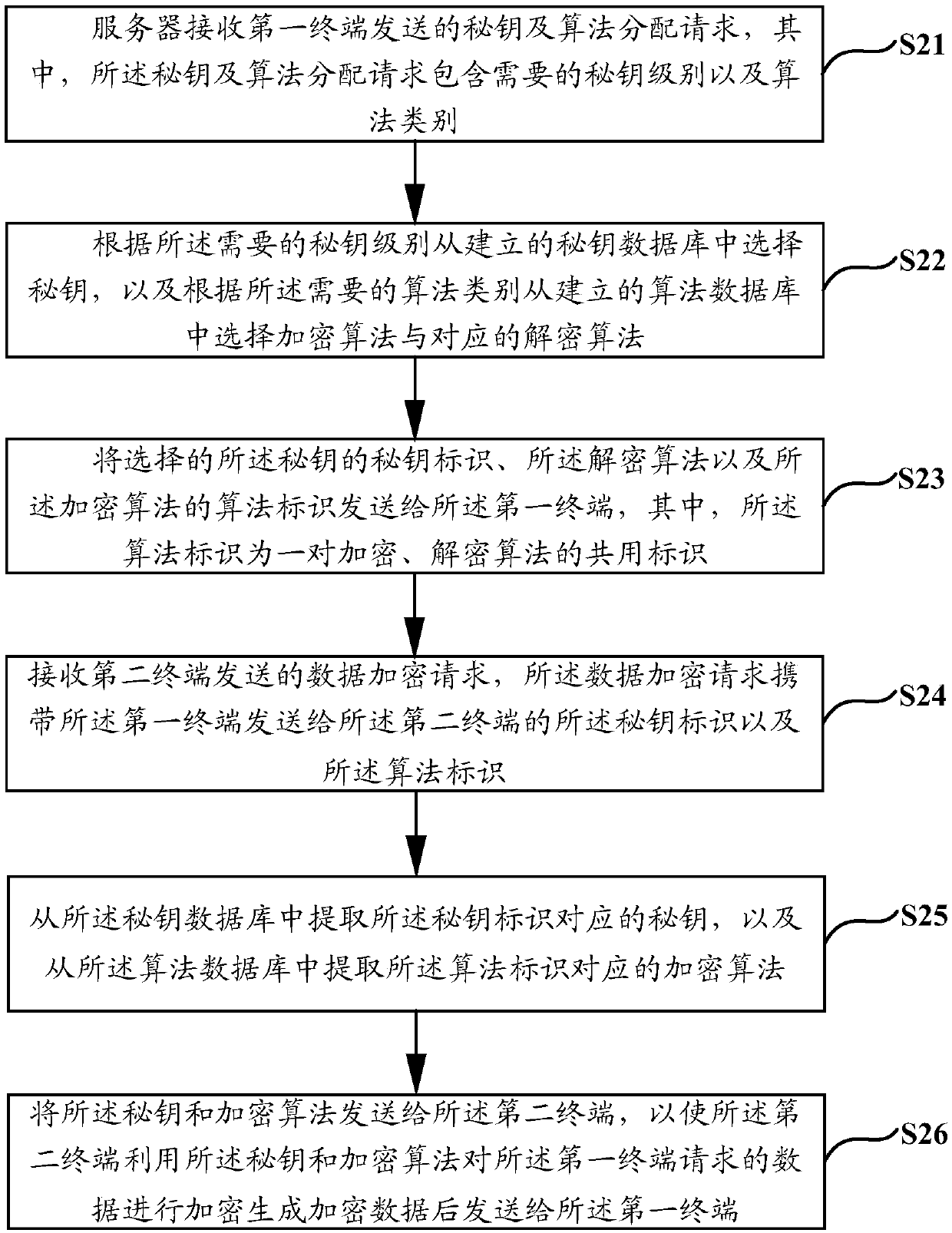
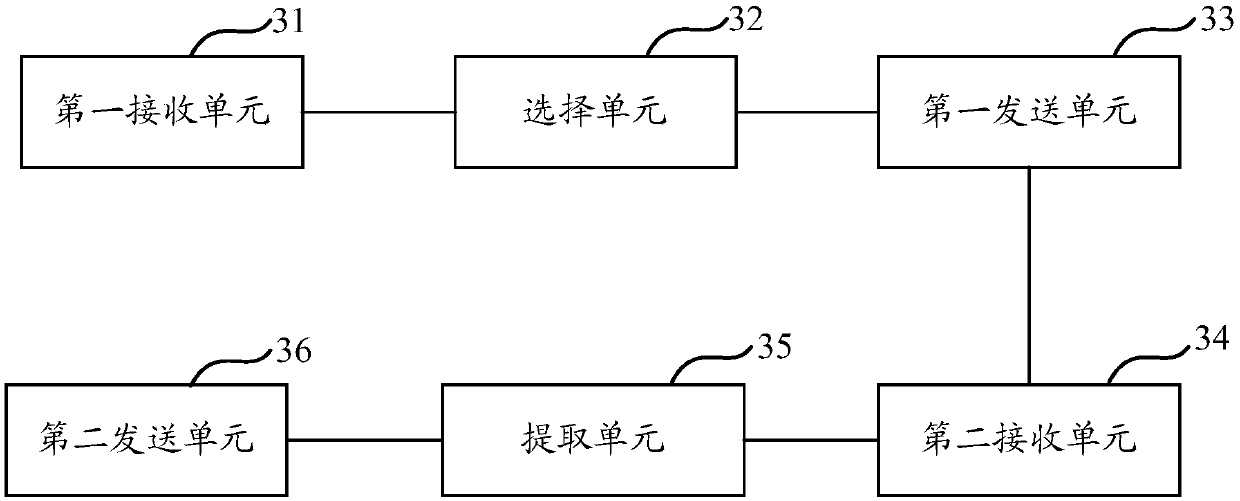
[0074] In order to solve the problem that the static secret key and the encryption algorithm are single, fixed for a long time and easy to be cracked in the existing data encryption method, the embodiment of the present invention provides a data encryption and decryption method and device.
[0075] The implementation principle of the data encryption and decryption method provided by the embodiment of the present invention is: the server receives the secret key and algorithm distribution request sent by the first terminal, wherein the secret key and algorithm distribution request includes the required secret key level and algorithm type, and the server receives Store a pre-established secret key database and algorithm database, select a secret key from the established secret key database according to the required secret key level, select an encryption algorithm and a corresponding encryption algorithm from the established algorithm database according to the required algorithm typ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com