Application memory leak detection method and device
A technology for memory leaks and detection methods, which is applied in the field of detection methods and devices for memory leaks, and can solve problems such as inability to detect memory leaks in time, inability to use in an online environment, and affecting normal use of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
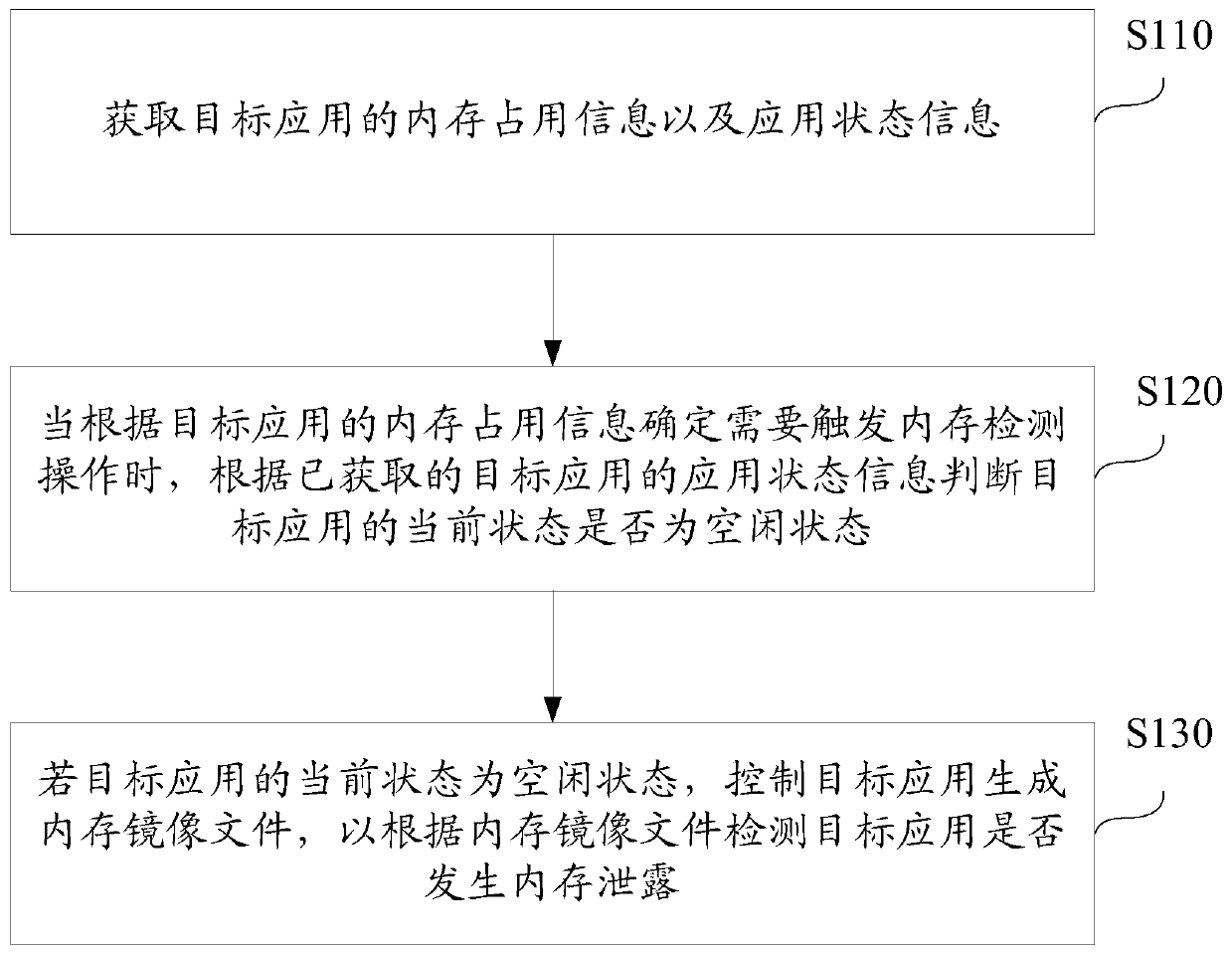
[0074] figure 1 A flow chart of a method for detecting an application memory leak provided by Embodiment 1 of the present invention is shown. like figure 1 As shown, the method includes:
[0075] Step S110: Obtain memory usage information and application state information of the target application.
[0076] During specific implementation, the above-mentioned information can be obtained flexibly in various ways. For example, the detection code used to obtain the above-mentioned information can be integrated in the target application, and then the above-mentioned information can be obtained through the detection code integrated in the target application; Set up a detection application independent of the target application, so that the memory usage information and application status information of one or more target applications can be obtained through the detection application.
[0077] Specifically, the memory usage information of the target application is used to represent ...
Embodiment 2
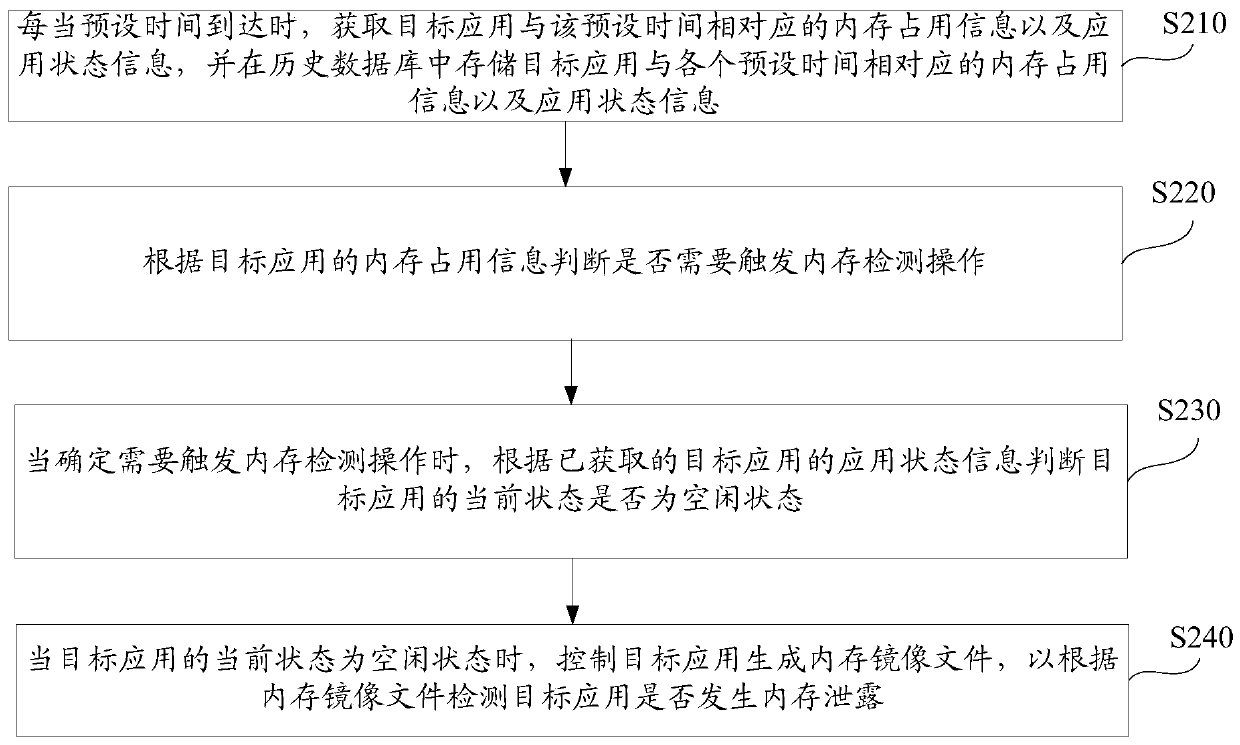
[0087] figure 2 A flow chart of a method for detecting an application memory leak provided by Embodiment 2 of the present invention is shown. like figure 2 As shown, the method includes:
[0088] Step S210: Whenever the preset time arrives, obtain the memory usage information and application status information of the target application corresponding to the preset time, and store the memory usage information and application status information of the target application corresponding to each preset time in the history database. Application state information.
[0089] During specific implementation, step S210 may be triggered periodically according to a preset interval, for example, step S210 is triggered every 30 minutes. Alternatively, step S210 may be triggered once or multiple times within a preset system self-check period. For example, the period from 3:00 am to 3:30 am or from 3:00 am to 5:00 am may be set as the system self-inspection period, and step S210 may be trig...
Embodiment 3
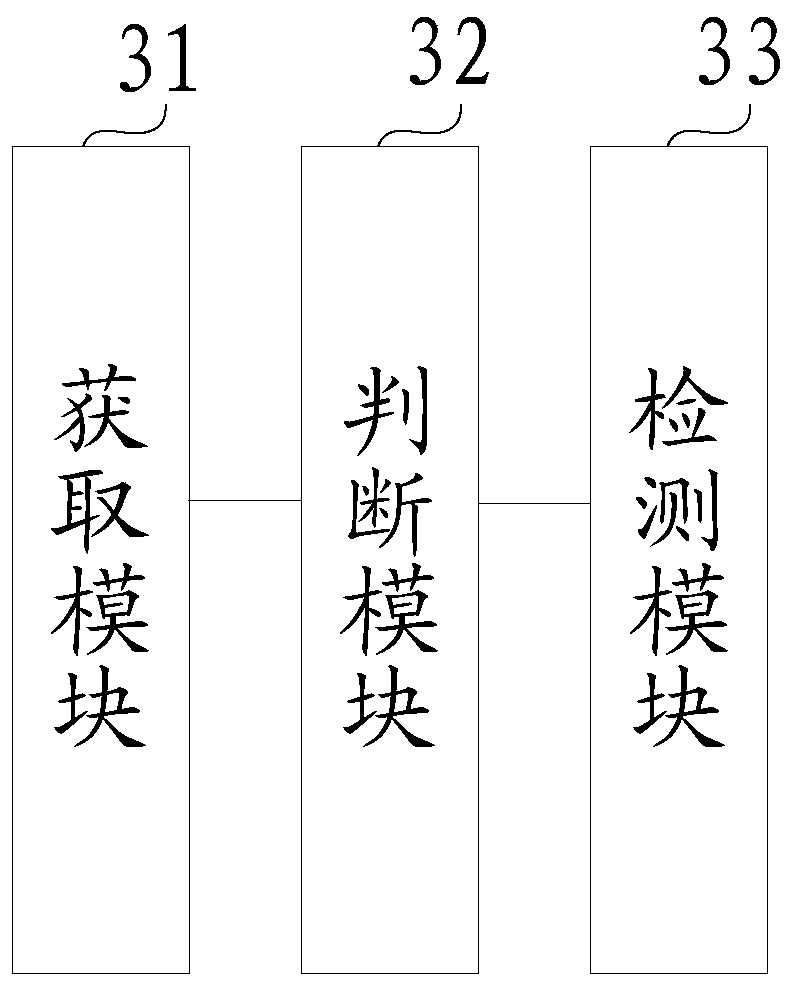
[0128] image 3 It shows a schematic structural diagram of a device for detecting application memory leaks provided by Embodiment 3 of the present invention, and the device includes:
[0129] An acquisition module 31, adapted to acquire memory usage information and application status information of the target application;
[0130] The judging module 32 is adapted to judge whether the current state of the target application is an idle state according to the obtained application state information of the target application when it is determined according to the memory occupation information of the target application that a memory detection operation needs to be triggered;
[0131] The detection module 33 is adapted to control the target application to generate a memory image file if the current state of the target application is an idle state, so as to detect whether a memory leak occurs in the target application according to the memory image file.
[0132] Optionally, the judgi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com