High-safety key task scheduling method based on inter-core migration
A task scheduling and task technology, applied in the direction of program startup/switching, resource allocation, program control design, etc., can solve problems such as poor security, and achieve the effect of improving security and increasing the success rate of scheduling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
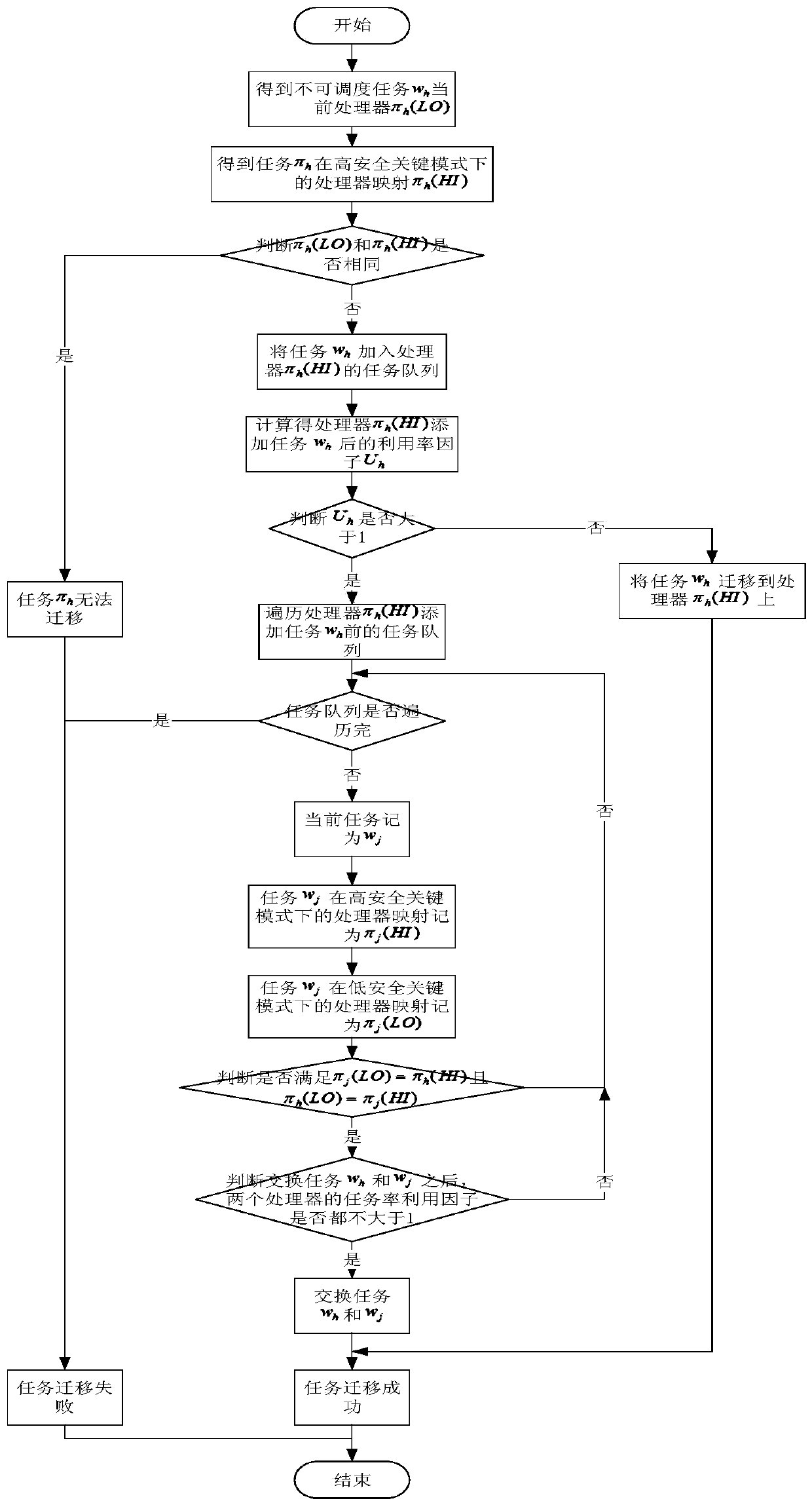
[0021] refer to figure 1 . The specific steps of the method for scheduling high-security critical tasks based on inter-core migration in the present invention are as follows:
[0022] Step 1. Get the unschedulable task w h The current processor π h (LO) and its processor mapping π in the high safety critical mode HI-cri h (HI).
[0023] Step 2. Judgment task w h Processor Mapping π in Low Safety Critical Mode LO-cri h (LO) and Processor Mapping in High Safety-Critical Modes π h Whether (HI) are the same, if they are the same, it means that the task cannot be migrated between cores, and skip to step 5; if not, it means that the task can be migrated, and skip to step 3.
[0024] Step 3, assign task w h join processor pi h (HI) task queue, calculate π by formulas (1) and (2) h (HI) task set utilization U h , judging processor π h (HI) task set utilization U h Whether it is greater than 1, if it is greater than 1, it means that the task w h Migrate to Processor π h ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com