Identity authentication method based on biological characteristics and identity authentication system thereof
A biometric and identity authentication technology, applied in the computer field, can solve problems such as low accuracy, reduced user experience of face recognition, and lack of Bluetooth function.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0251] The first implementation mode (the first mode of the plaintext comparison mode)
[0252] Figure 11 is a schematic flowchart showing the biometric-based identity authentication method of the first embodiment.
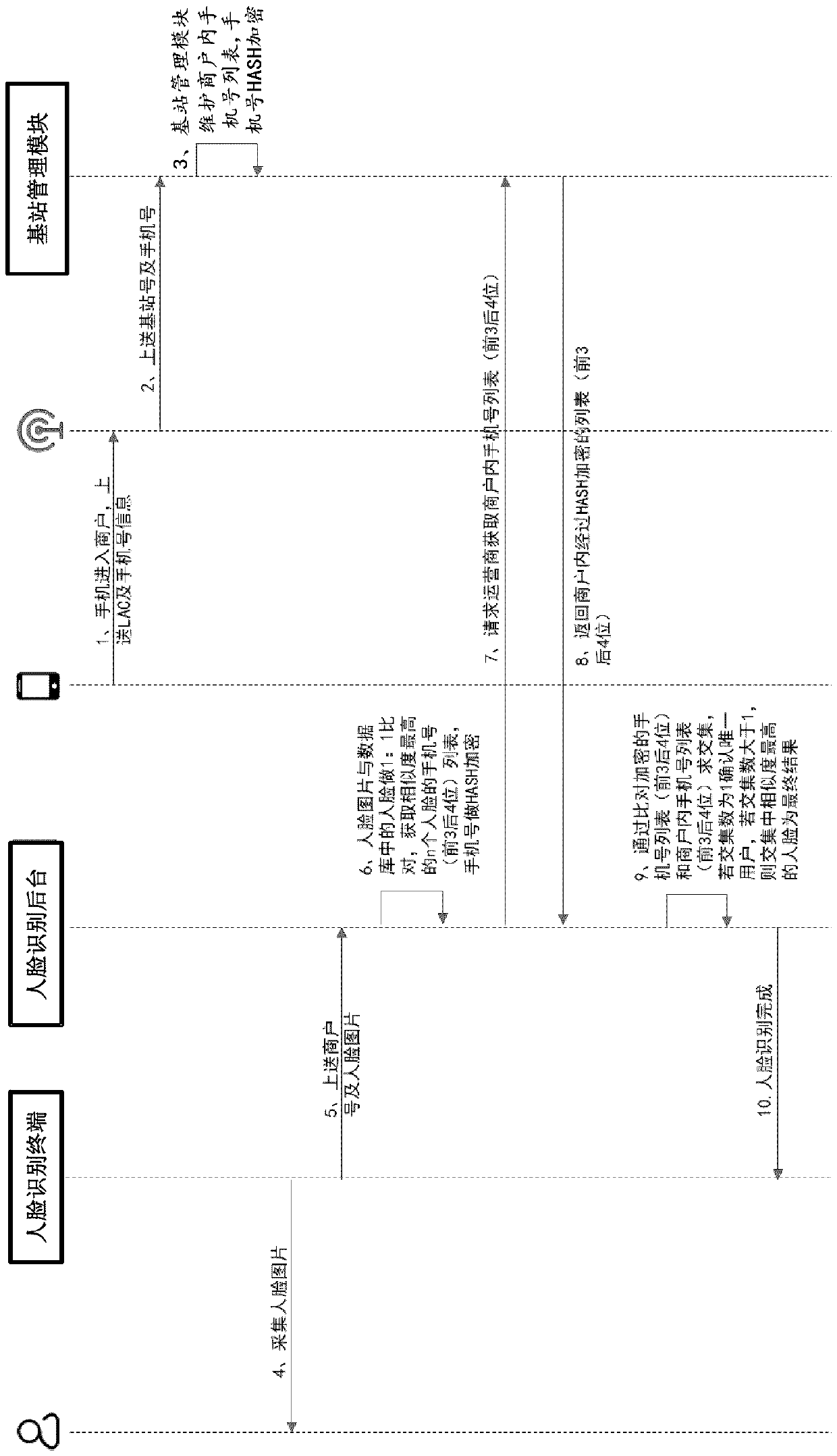
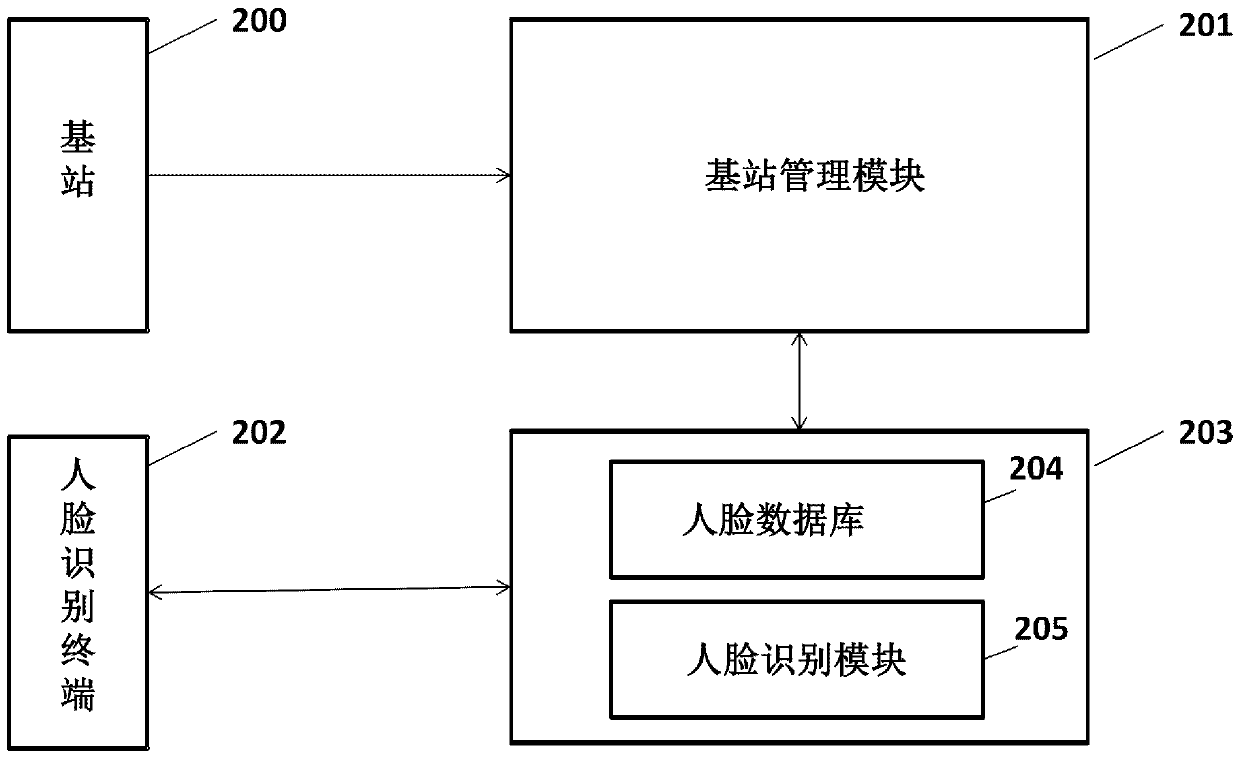
[0253] Such as Figure 11 As shown, the biometric-based identity authentication method of the first embodiment includes the following steps: 1. After the user enters the merchant, the mobile phone sends LAC and mobile phone number information to the base station, wherein LAC refers to geographic location update information, that is, when When the mobile phone receives the signal broadcast by the base station, and finds that the base station signal it originally received is different from the broadcast signal received now, it will upload the information;
[0254] 2. Base station (by Figure 11 The pattern representation between the mobile phone and the base station management module) sends the mobile phone number and the base station number to the base station ...
no. 2 approach
[0277] The second implementation mode (the second mode of the plaintext comparison mode)
[0278] Figure 13is a schematic flowchart showing the biometric-based identity authentication method of the second embodiment.
[0279] Such as Figure 13 As shown, the biometric-based identity authentication method of the second embodiment includes the following steps:
[0280] 1. After the user enters the merchant, the mobile phone will send the location update information and mobile phone number information to the base station;
[0281] 2. The base station sends the mobile phone number and base station number to the base station management module;
[0282] 3. The base station management module dynamically maintains the mobile phone number list in the merchant according to the base station number, and the mobile phone number is HASH encrypted;
[0283] 4. The face recognition terminal collects faces;
[0284] 5. The face recognition terminal uploads the merchant number and face to...
no. 3 approach
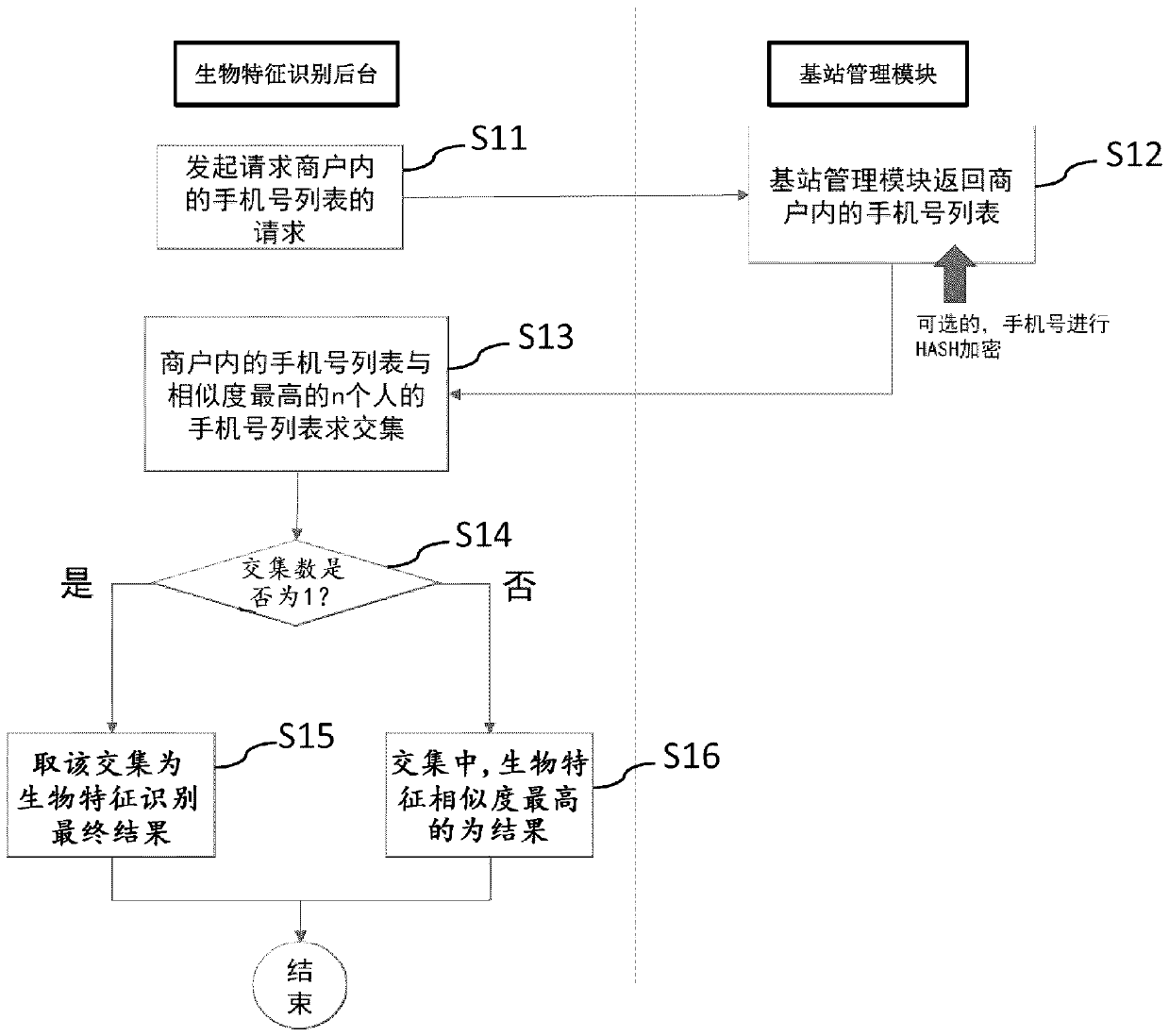
[0297] The third implementation mode (the first mode of the confusing comparison mode)
[0298] Figure 15 is a schematic flowchart showing the biometric-based identity authentication method of the third embodiment.
[0299] Such as Figure 15 As shown, the biometric-based identity authentication method of the third embodiment includes the following steps:
[0300] 1. After the user enters the merchant, the mobile phone will send the location update information and mobile phone number information to the base station;
[0301] 2. The base station sends the mobile phone number and base station number to the base station management module;
[0302] 3. The base station management module dynamically maintains the mobile phone number list in the merchant according to the base station number, and the mobile phone number is HASH encrypted;
[0303] 4. The face recognition terminal collects faces;
[0304] 5. The face recognition terminal uploads the merchant number and face to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com