Data storage, data reading method and device for private data
A privacy data, data storage technology, applied in the field of data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0107] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
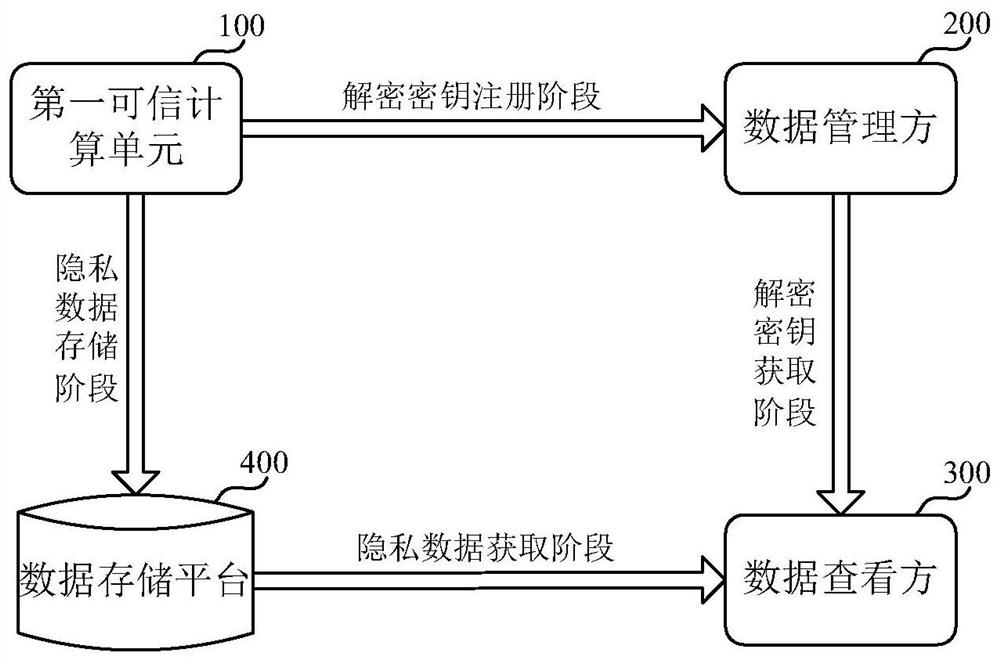
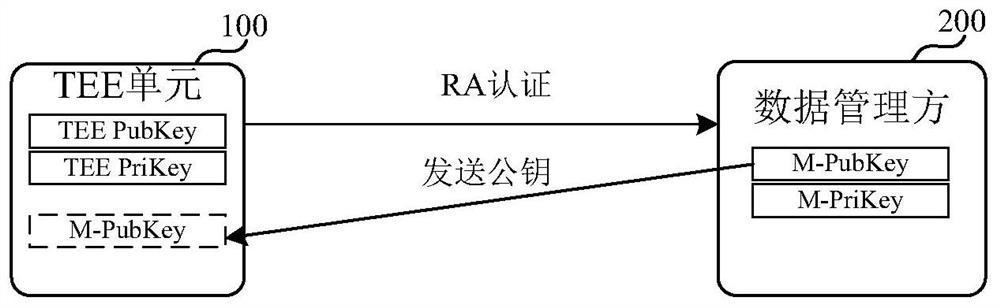
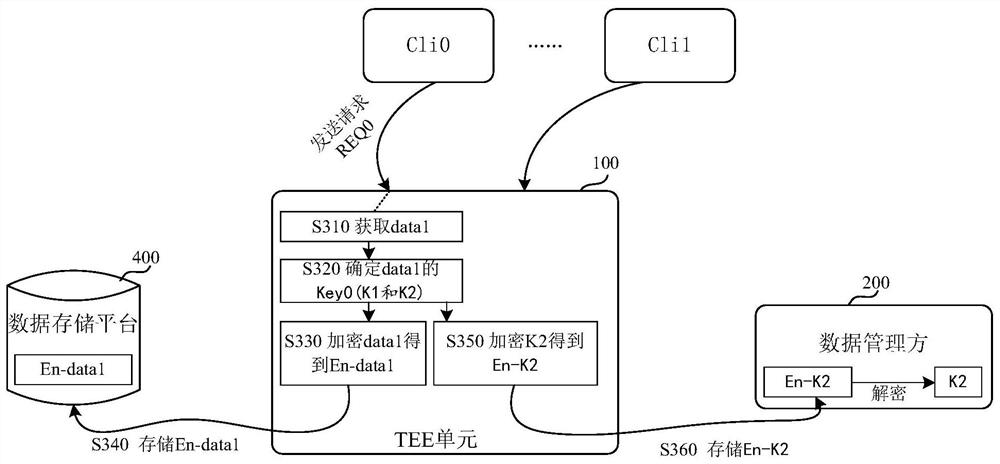
[0108] figure 1 It is a schematic diagram of an implementation scenario of an embodiment disclosed in this specification. It includes a first trusted computing unit 100 , a data manager 200 , a data viewer 300 and a data storage platform 400 . although figure 1 Only one trusted computing unit is shown in , but there are often multiple trusted computing units in actual scenarios. For data viewers, although figure 1 Only one data viewer is shown in , and there may be multiple data viewers in the actual scene.
[0109] The first trusted computing unit 100 can be used for data computing, wherein computing tasks can be executed. The hash value of the program code corresponding to the computing task running in the first trusted computing unit 100 may be called a code hash. The code hash can be used to identify computing tasks running in the trusted compu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com