Multi-party joint feature evaluation method and device for protecting privacy security
A privacy-preserving, multi-party technology, used in computer security devices, digital data protection, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
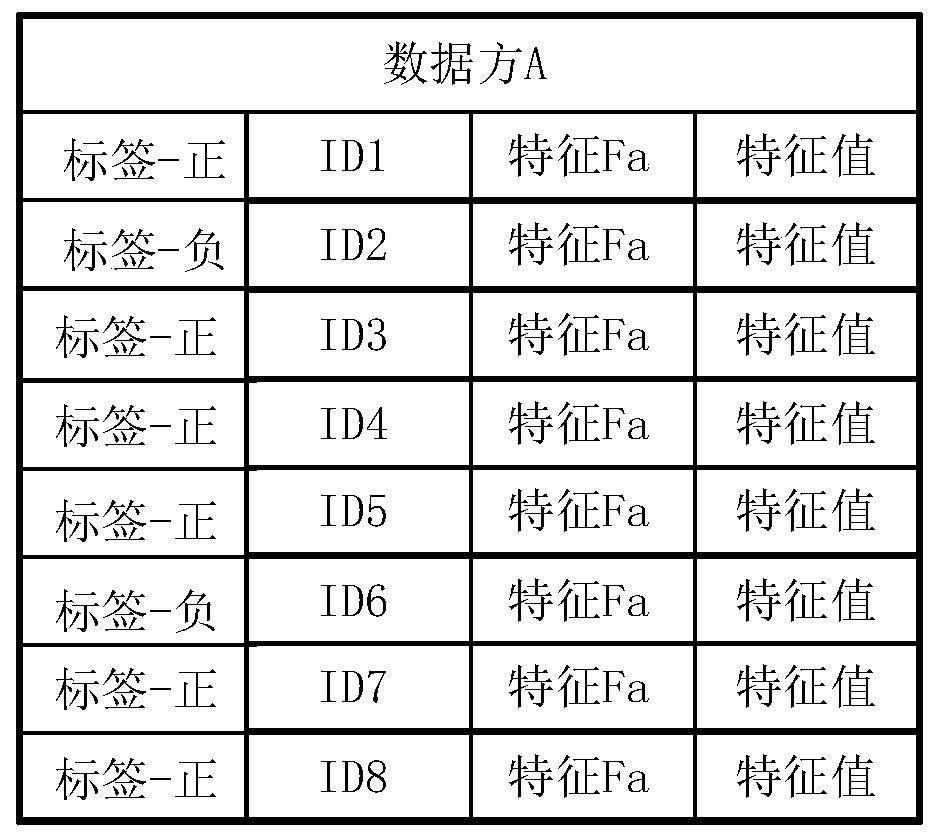
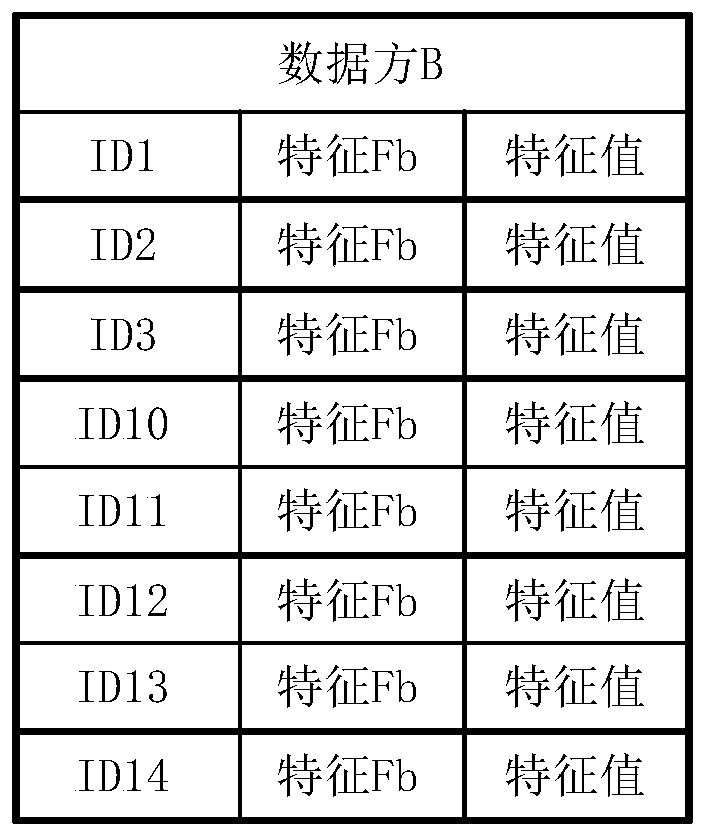
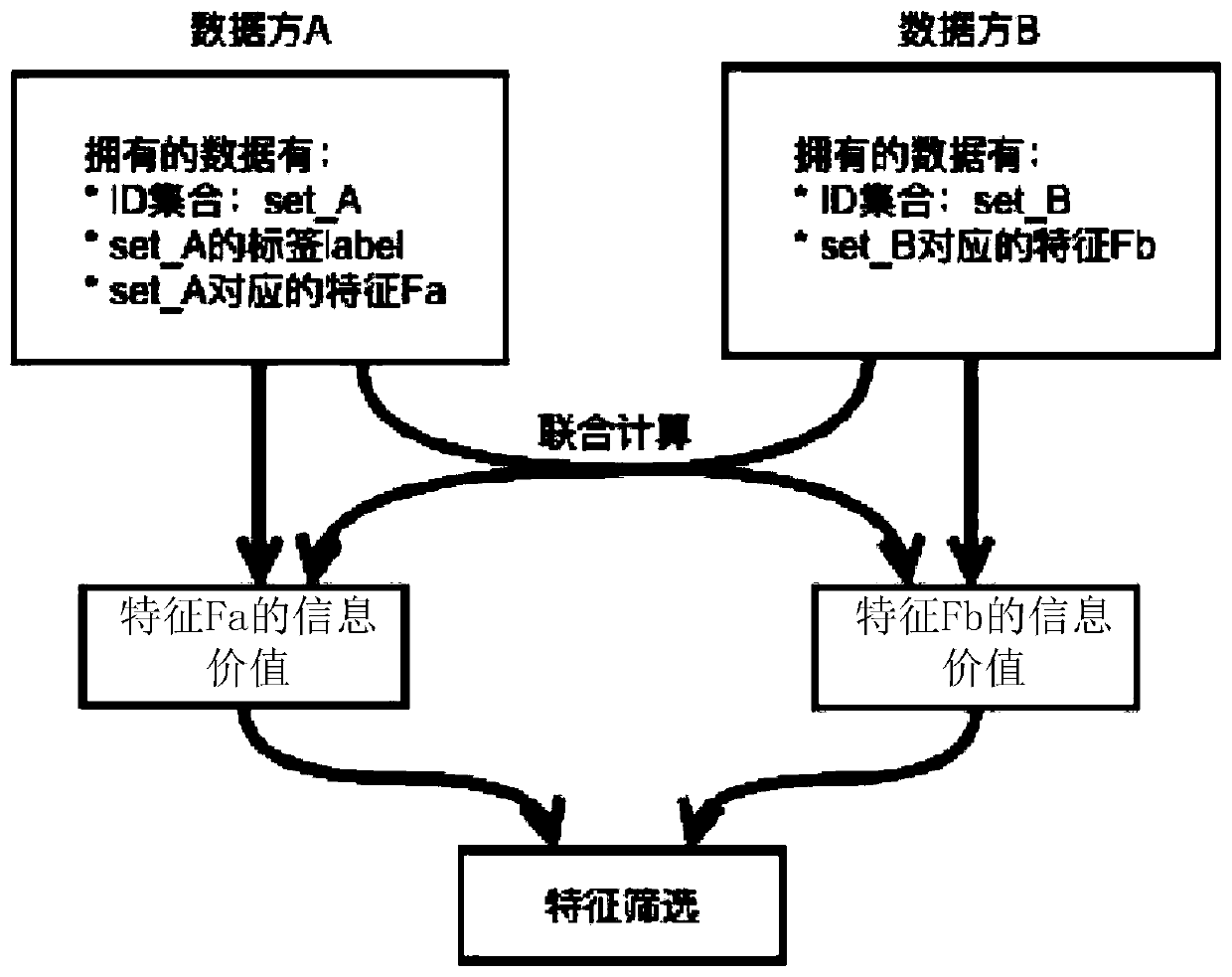
[0071] Figure 1A It shows the data owned by the data party A disclosed in the embodiment of this specification. Figure 1B It shows the data owned by the data party B disclosed in the embodiment of this specification. Figure 1A with Figure 1B Each ID (Identity Document, identity identification number) in can be a digital code that uniquely identifies a user, such as a mobile phone number. Such as Figure 1A with Figure 1B As shown, ID1, ID2, and ID3 are IDs shared by data party A and data party B. Figure 1A Each ID in has a label and a feature value of feature Fa. Exemplary, such as Figure 1A As shown, labels can be divided into positive labels and negative labels. Figure 1B Each ID in has the feature value of feature Fb.
[0072] In an exemplary scenario, the data party A may be an electronic payment platform (such as Alipay), and the tag may...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com