Data security transmission system and method
A technology of data security and transmission method, which is applied in the field of data security transmission system, can solve problems such as inability to restore data, inability to trace data traces, etc., and achieve the effect of high verification reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
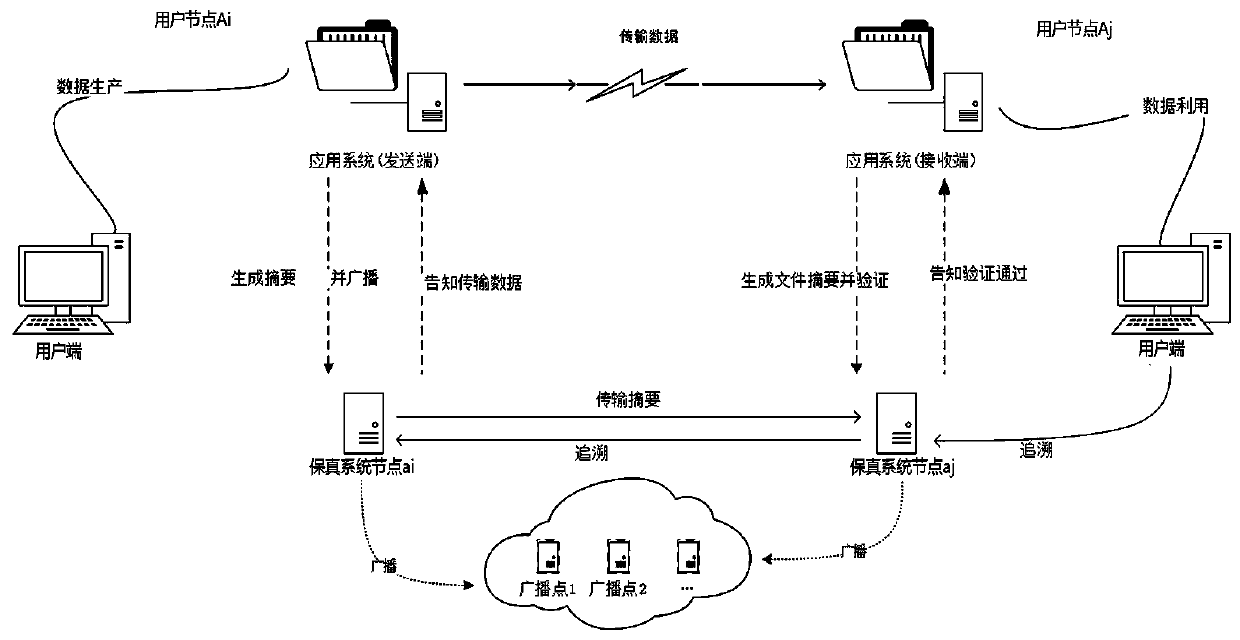
[0041] according to figure 1 As shown, a data security transmission system includes user nodes A1, A2, ... An, fidelity system nodes a1, a2, ... an corresponding to each of the user nodes, and several broadcast points; any one of the The user node Ai includes a user end and an application system, and the application system includes a sending end and a receiving end; the objects directly transmitted by any fidelity system node ai are limited to: the corresponding user node Ai and any other fidelity Data is not directly transmitted between the system node aj; the non-corresponding fidelity system node ai and the user node Aj.
Embodiment 2
[0043] A data security transmission method, comprising the following steps:
[0044] S1. Data generation:
[0045] In the user node Ai, the data generated in the user terminal is formed into the data Data in the application system;
[0046] S2. Data processing and broadcasting:
[0047] ①The sending end of the application system transmits the data Data to the node ai of the corresponding fidelity system, and generates a summary file n_Data;
[0048] ② Fidelity system node ai encrypts the abstract file n_Data to form ciphertext data (n_Data) AES, and broadcasts the ciphertext data (n_Data) AES to all broadcast points, and at the same time, the ciphertext in fidelity system node ai Two copies of data (n_Data) AES backup;
[0049] S3, data transmission:
[0050]①The fidelity system node ai transmits the ciphertext data (n_Data) AES to the fidelity system node aj, and informs the user node Ai after completion; the fidelity system node aj stores the received ciphertext data as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com