Computer network identity verification system
A computer network and identity verification technology, applied in the field of computer network identity verification systems, can solve problems such as the inability of the verification system to meet the needs, and achieve the effects of preventing illegal acts, high security, and convenient use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
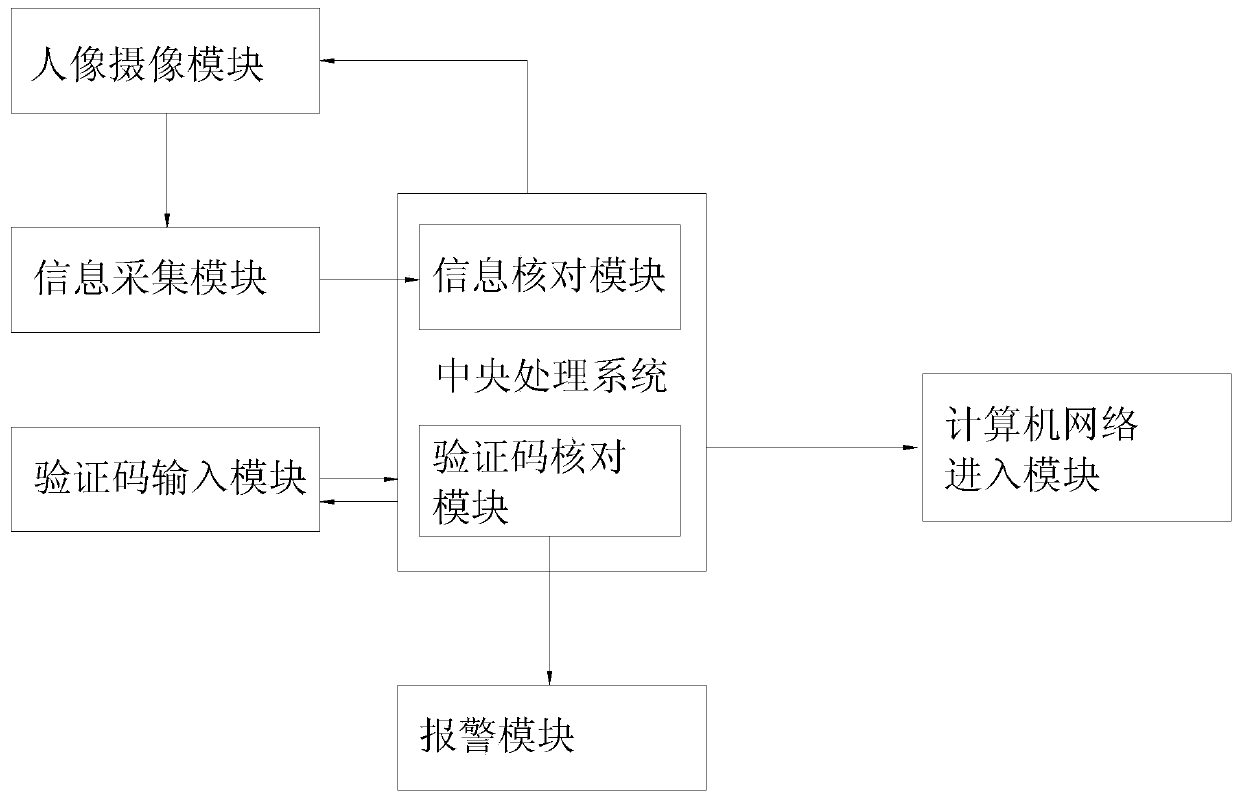
[0018] refer to figure 1 , a computer network identity verification system proposed by the present invention, including a central processing system, an information collection module, a portrait camera module, a verification code input module, a computer network entry module and an alarm module;
[0019] The central processing system is equipped with an information check module and a verification code check module; the portrait camera module is connected to the information collection module by communication; the information collection module is connected to the information check module by communication;
[0020] The verification code input module is in communication connection with the verification code checking module; the portrait camera module, the computer network entry module and the alarm module are all in communication connection with the central processing system.
Embodiment 2
[0022] refer to figure 1 , a computer network identity verification system proposed by the present invention, including a central processing system, an information collection module, a portrait camera module, a verification code input module, a computer network entry module and an alarm module;
[0023] The central processing system is equipped with an information check module and a verification code check module; the portrait camera module is connected to the information collection module by communication; the information collection module is connected to the information check module by communication;
[0024] The verification code input module is in communication connection with the verification code checking module; the portrait camera module, the computer network entry module and the alarm module are all in communication connection with the central processing system.
[0025] The use of computer network authentication system includes the following steps:
[0026] S1, inpu...
Embodiment 3
[0032] refer to figure 1 , a computer network identity verification system proposed by the present invention, including a central processing system, an information collection module, a portrait camera module, a verification code input module, a computer network entry module and an alarm module;
[0033] The central processing system is equipped with an information check module and a verification code check module; the portrait camera module is connected to the information collection module by communication; the information collection module is connected to the information check module by communication;
[0034] The verification code input module is in communication connection with the verification code checking module; the portrait camera module, the computer network entry module and the alarm module are all in communication connection with the central processing system.
[0035] The use of computer network authentication system includes the following steps:
[0036] S1, inpu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com