Switch linkage firewall protection improving method
A switch and firewall technology, which is applied in the field of switch linkage firewall protection improvement, to achieve the effect of improving retrieval efficiency and reducing local area network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
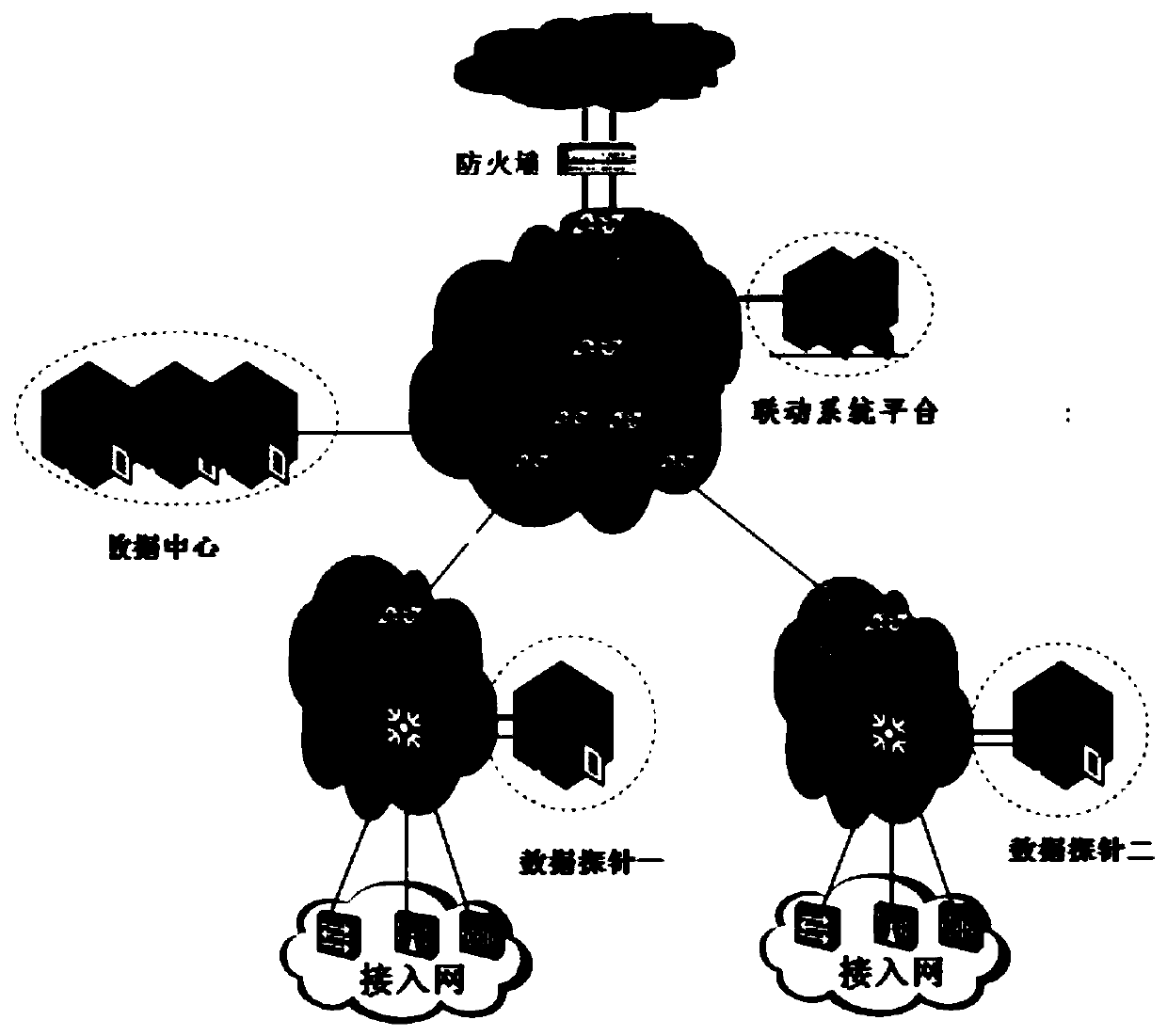
[0021] Example: see figure 1 .
[0022] The method of improving the protection of the switch linkage firewall, realizes the network monitoring through the packet capture tool, cooperates with the port mirroring technology to use the static IP to bind the MAC and the IP in two directions without changing the IPV4 protocol, and at the same time uses VLAN to reduce the local area network and improve the retrieval efficiency , find the source of threat events, link with the switch, block the path of threat events, make up for the shortcomings of traditional firewalls, and provide in-depth protection for network security.
[0023] The application will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0024] Step 1. Set up bypass monitoring on the switch on the same network segment as the network security protection server; the switch supports port mirroring, and uses the port mirroring of the switch to copy all data passing through the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com