A method and device for constructing a file derivative graph
A construction method and a technology of derived graphs, applied in the field of information security, can solve the problem of time-consuming and labor-intensive, unable to locate the equipment or employees that leak sensitive files, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
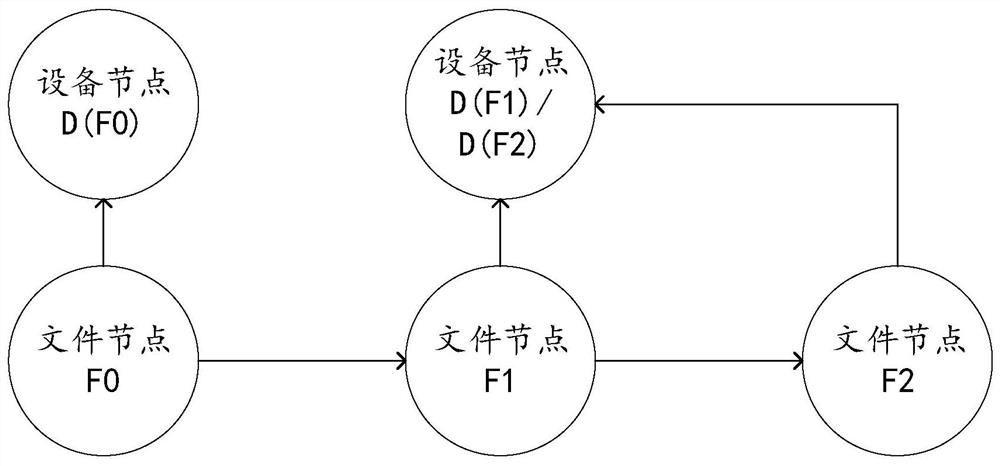
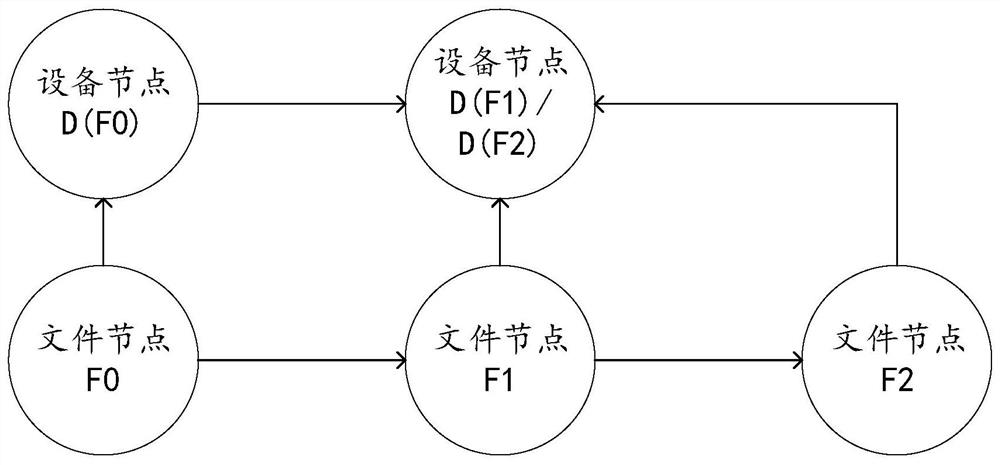
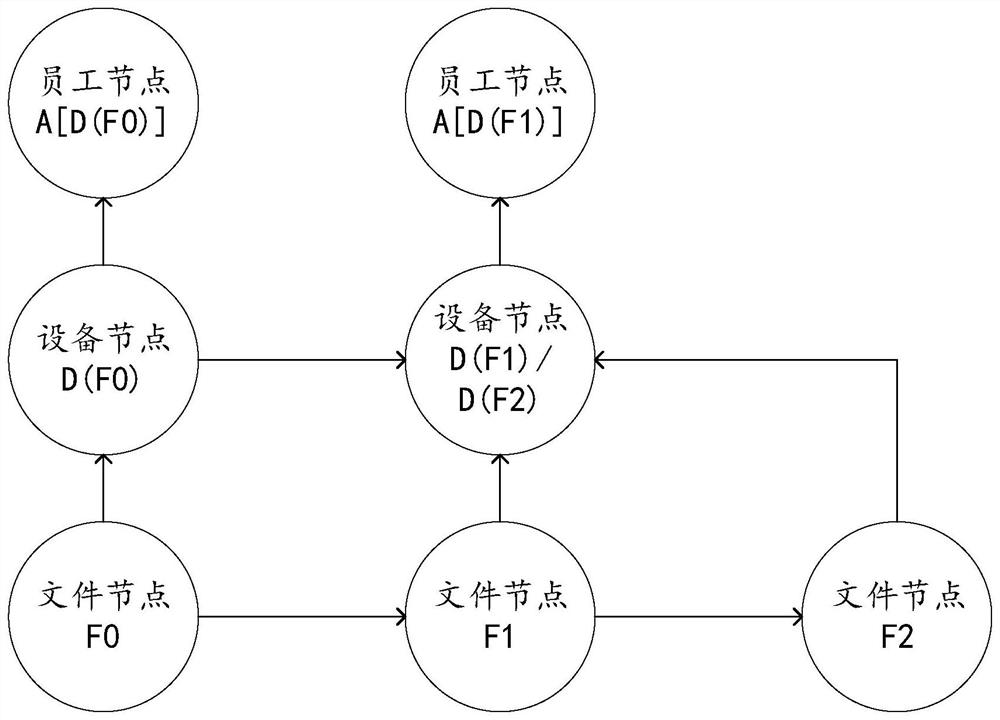
[0039] Many devices in an enterprise contain private data, i.e. sensitive files, such as trade secret files or employee privacy files, that businesses do not want to leak and that need to be transferred between devices within the enterprise for use in performing business operations. As a result, enterprises have a leak-proof security requirement for these sensitive files, so that these sensitive files can be transferred between internal devices without leaking to the outside world.
[0040] In order for these sensitive files not to be leaked, there are many imperfect leak prevention strategies, for example, there are anti-leak programs installed on every device in the enterprise, and the anti-leakage program records a numerical summary of the contents of all sensitive files. When an employee copies or sends a file on an internal device, the leak prevention program calculates a numeric summary of the file's contents, verifies that the digital summary of the content is the same as t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com