Threat intelligence analysis method and system based on ant colony algorithm
An ant colony algorithm and analysis method technology, applied in the field of network security, can solve the problems of high time cost, waste of manpower and material resources, different judgment results of the same traffic information, etc., to achieve the effect of simple calculation operation, reduction of analysis time, and saving of manpower and material resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
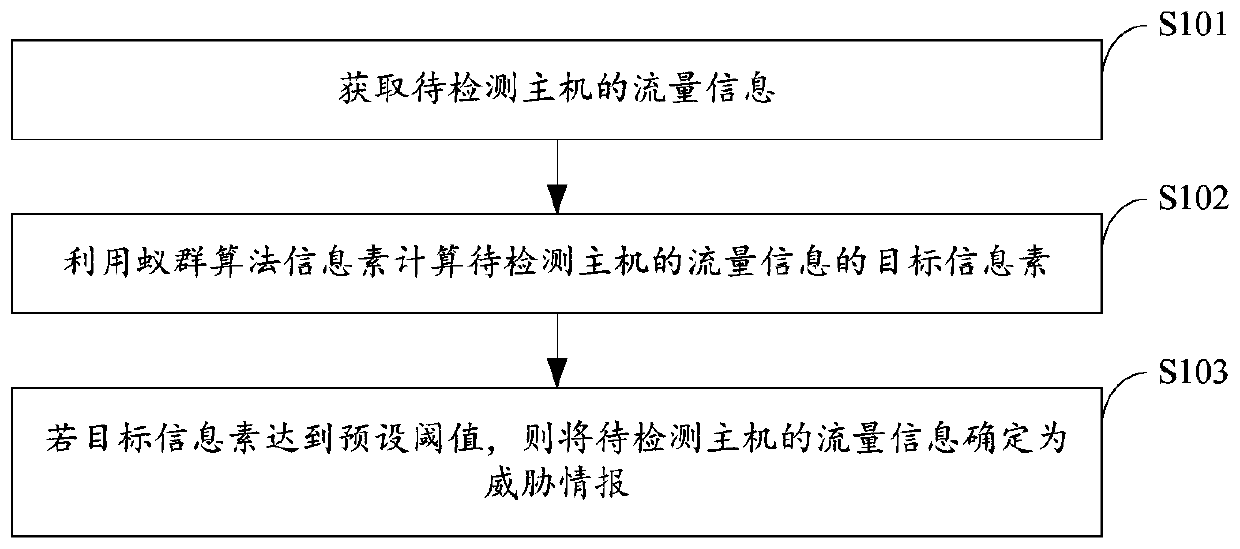
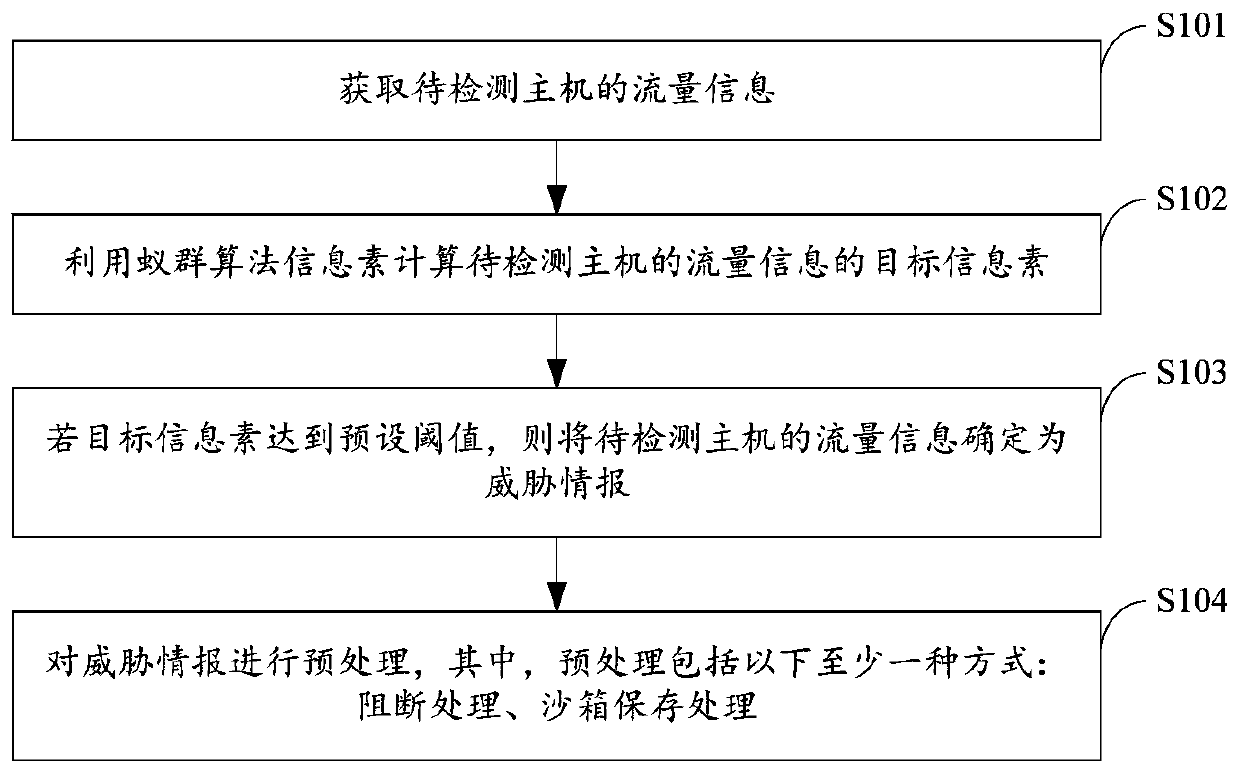
[0030] refer to figure 1 An ant colony algorithm-based threat intelligence analysis method provided in an embodiment of the present invention may include the following steps:
[0031] Step S101, acquiring traffic information of a host to be detected.
[0032] In the embodiment of the present invention, the device for obtaining the flow information of the host to be detected includes, but is not limited to: a network probe. Wherein, the network probe can access the host to be detected, capture data packets on the host to be detected, filter and analyze the data packets, and obtain traffic information. The flow information may include at least one of the following keywords: access port behavior, attack frequency, and attack importance. Wherein, the attack importance may refer to the importance of pheromone in the ant colony algorithm.
[0033] Step S102, using the ant colony algorithm pheromone to calculate the target pheromone of the traffic information of the host to be det...
Embodiment 2
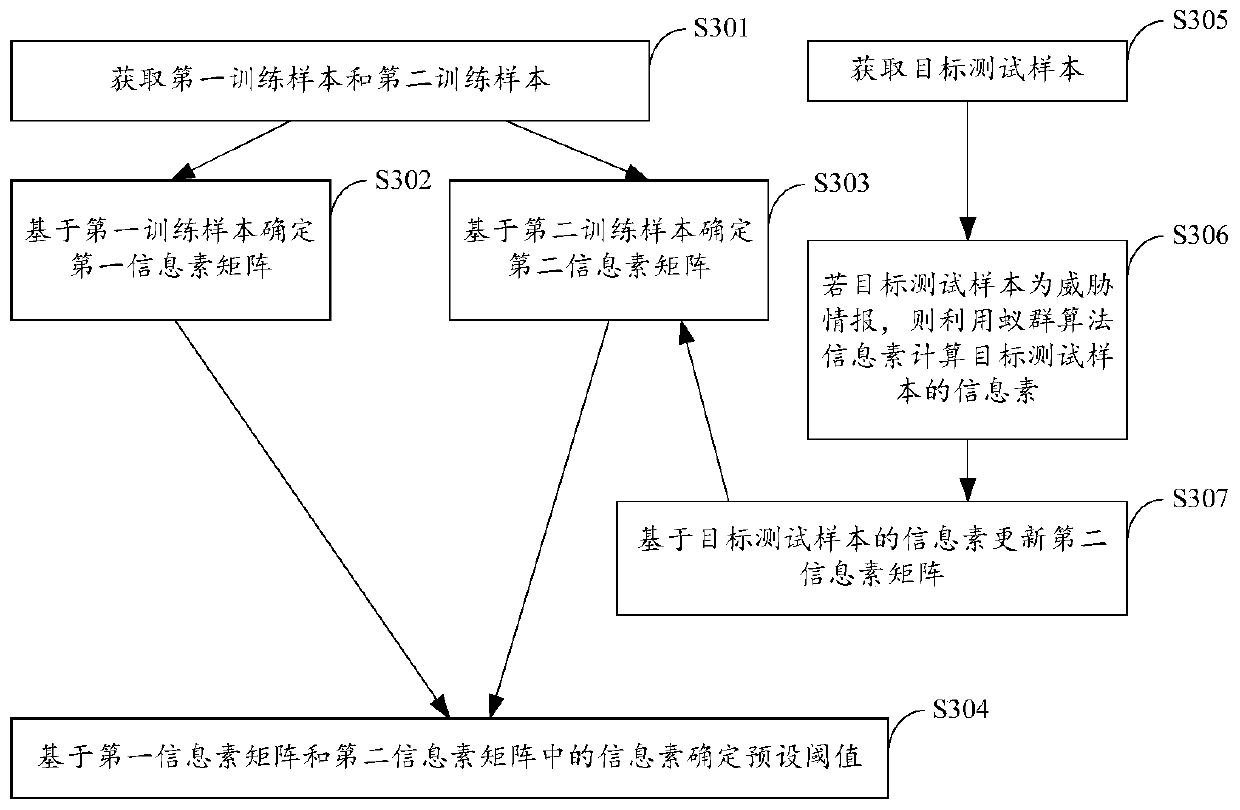
[0070] refer to Figure 4 , a threat intelligence analysis system based on an ant colony algorithm provided by an embodiment of the present invention may include the following modules:
[0071] Obtaining module 11, is used for obtaining the flow information of host computer to be detected;
[0072] Calculation module 12, for utilizing the ant colony algorithm pheromone to calculate the target pheromone of the traffic information of the host to be detected;
[0073] The first determination module 13 is configured to determine the flow information of the host to be detected as threat intelligence if the target pheromone reaches a preset threshold.
[0074] An ant colony algorithm-based threat intelligence analysis system provided by an embodiment of the present invention includes: first using the acquisition module to obtain the traffic information of the host to be detected, and then using the ant colony algorithm pheromone calculation formula and the calculation module to cal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com