Quantum conference key negotiation method and system
A key negotiation and conference technology, which is applied in transmission systems, digital transmission systems, and key distribution, can solve the problems of high difficulty in experiment implementation, low coding rate, and short transmission distance, so as to increase the transmission distance and coding rate , high efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
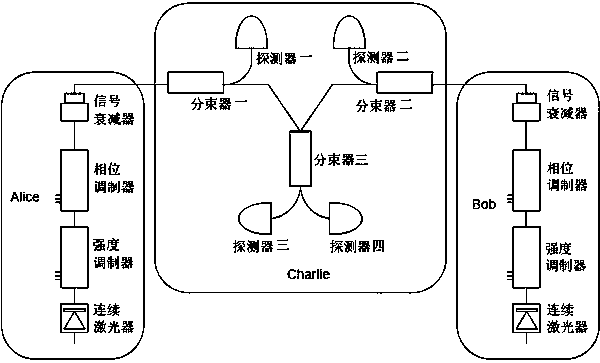
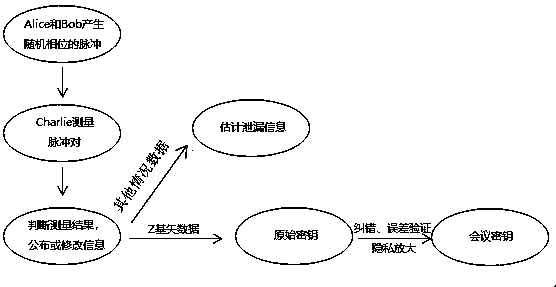
[0081] The three parties are Alice, Bob, and Charlie. Among them, Alice and Bob have the same equipment, which belongs to the symmetrical relationship in the system. Alice and Bob use CW lasers to generate all-phase stable light, and use intensity modulators, phase modulators, and signal attenuators for pulse preparation, decoy state modulation, phase randomization, phase encoding, and weak light modulation. In the decoy state protocol, Alice randomly prepares a variety of phase-randomized weakly coherent pulses with different light intensities, one of which is the signal state for key generation, and the rest are decoy states. Charlie uses detectors 1 and 2 to perform Z base down measurements, and detectors 3 and 4 to perform X base down measurements. Alice (Bob) sends the quantum state to Charlie, beam splitter one (two) splits the signal into two parts, one part is sent to detector one (two), and the other part is sent to beam splitter three (three). Alice (Bob) sends the...
Embodiment 2
[0112] This invention will also explore an ideal protocol.
[0113] In this embodiment, a single-photon source is used to replace the phase-randomized coherent light source corresponding to the logic bit value of the Z basis vector being 1, and the rest of the steps are the same as those in Embodiment 1.
[0114] The conference key encoding rate R can be calculated by the following formula:
[0115]
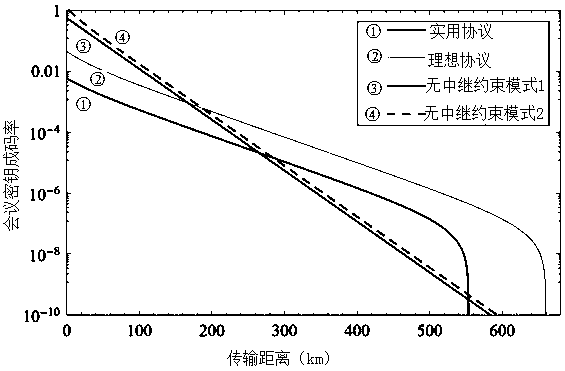
[0116] Compared with the previous protocol, the conference key encoding rate of the ideal protocol is faster and the transmission distance is longer. But an ideal single photon source is required.
[0117] No repeater constraints (repeaterless bound 1 and repeaterless bound 2) , . See references: arXiv:1912.03645, arXiv:1912.010658, and arXiv:1912.11355. In order to represent the linear attenuation of the rate with the distance in the original no-relay constraint and the linear attenuation of the system rate with the square root of the distance, let and , L is the t...
Embodiment 3
[0120] Compared with Embodiment 1, other parameters and operations remain unchanged, only the phase misalignment rate under the X base vector is changed .
[0121] Change the phase misalignment rate of 3.5% in Embodiment 1 to 7% and 13% respectively, and draw the relationship diagram of the conference key encoding rate and distance under the different misalignment rates of the X base vector. See Figure 4 . It can be found that the higher the phase misalignment rate, the shorter the transmission distance and the slower the rate. However, as long as the phase misalignment rate is lower than 7%, the transmission distance can exceed 500km, and if it is lower than 13%, the constraint of no relay can be broken. This system has extremely high practicability and operability.
[0122] To sum up, the present invention can obtain the relationship between the conference key coding rate and the distance through measurement and calculation. That is to change the situation that the ke...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap