Cross-domain authorized access control system for secure interoperability between different domains
A technology of authorized access and interoperability, applied in the field of cross-domain authorized access control system, which can solve the problem that the grammatical expressions of access control rules cannot recognize each other and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
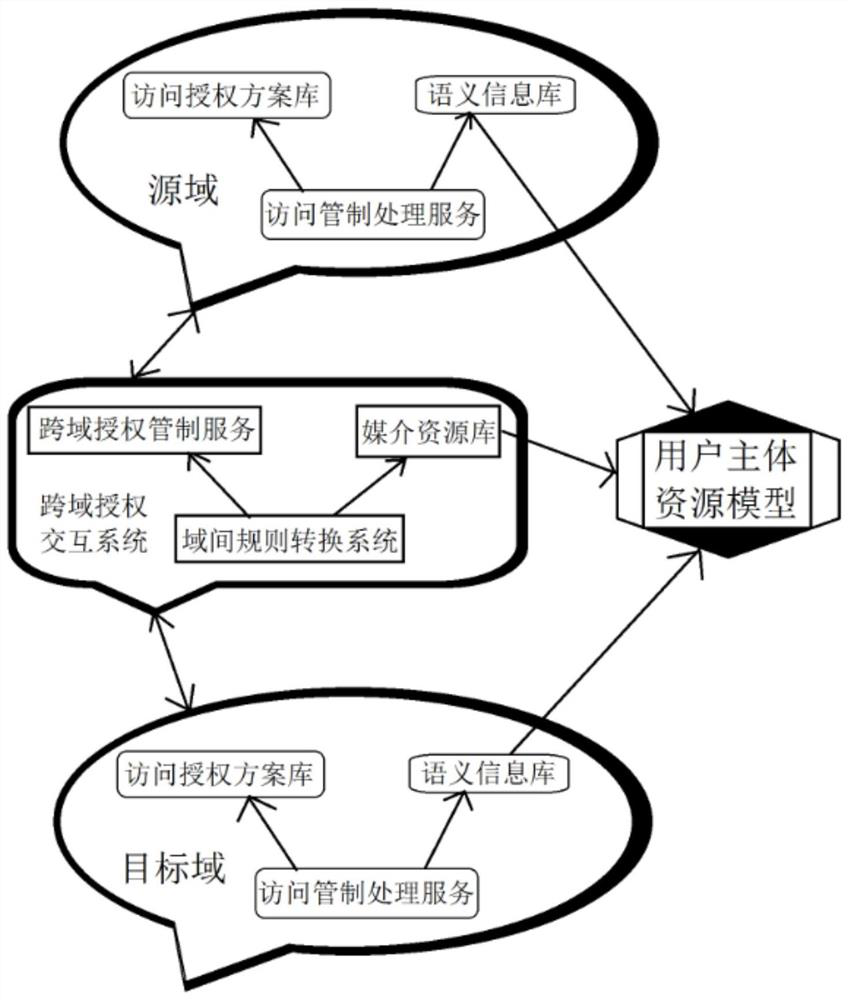
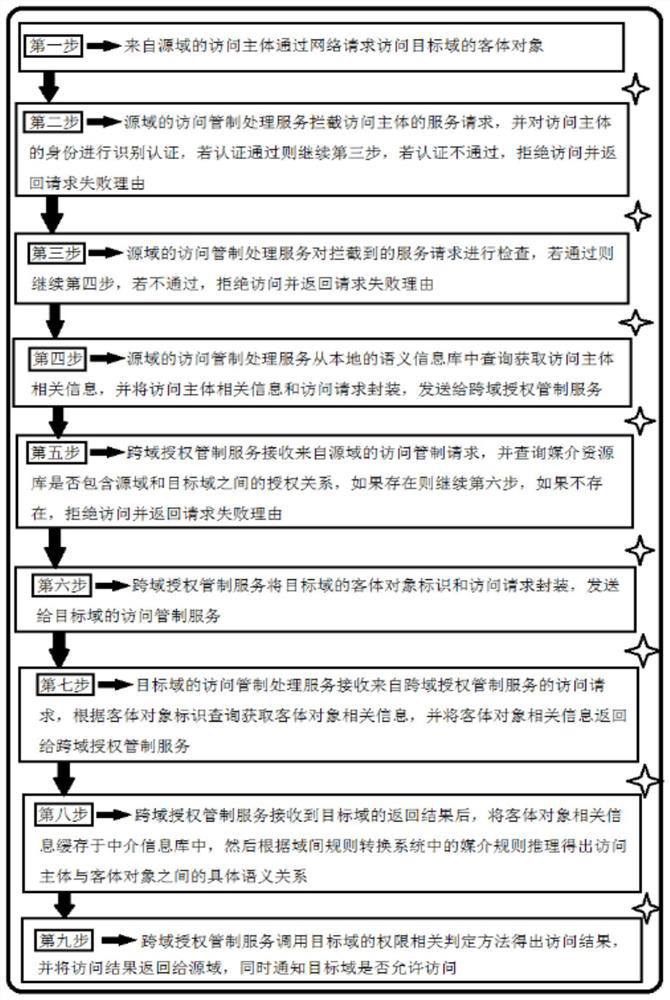
[0046] The technical solution of the cross-domain authorized access control system for inter-domain security interoperability provided by the present invention will be further described in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention and implement it.
[0047] With the rapid development of distributed computing systems, the interoperability between different system architectures is becoming more and more frequent. More and more transactions require the subject to authorize cross-domain access to object objects in other domains. Since the subject and object objects are often located in the In two or more different domains, the heterogeneity of authorization access control schemes within different domains may be very large, making it extremely difficult for subjects to authorize access across domains. There are two main methods to solve the above problems in the prior art. The first method realizes cross-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com