Information processing method and device and storage medium
An information processing method and equipment technology, applied in the Internet field, can solve problems such as increasing the risk of private key leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
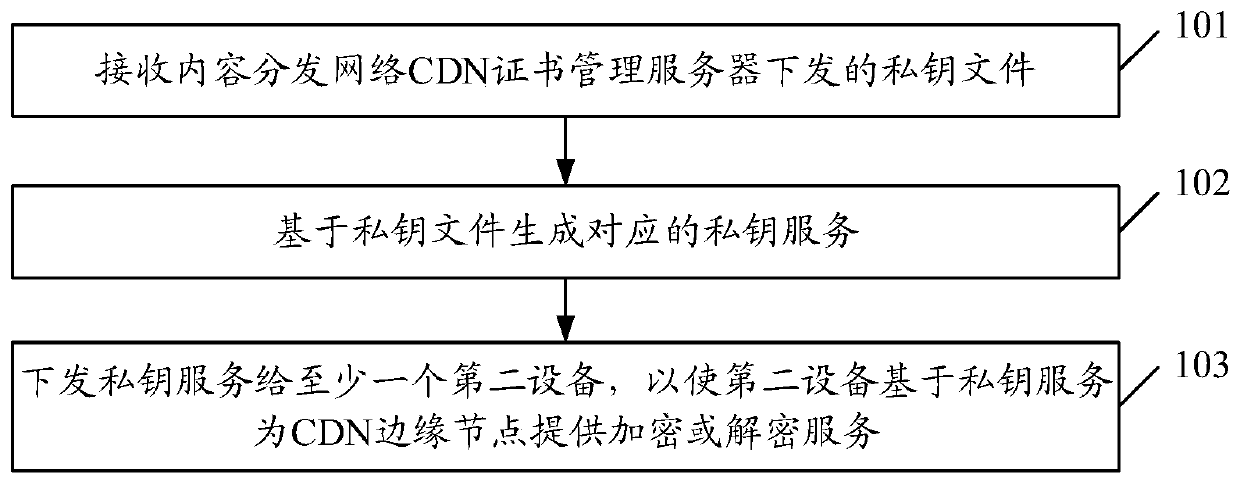
[0049] Such as figure 1 As shown, information processing methods include:
[0050] Step 101: Receive the private key file issued by the content distribution network CDN certificate management server;
[0051]Step 102: Generate a corresponding private key service based on the private key file;
[0052] Step 103: Issue the private key service to at least one second device, so that the second device provides encryption or decryption service for the CDN edge node based on the private key service.
[0053] Here, the subject of execution of steps 101 to 103 may be the processor of the first device. The first device is used to generate a private key service, and the second device is used to participate in implementing the SSL / TLS handshake request between the terminal device and the CDN edge node based on the private key service.
[0054] In practical applications, the method for obtaining the private key file corresponding to the domain name includes: sending a private key file r...
Embodiment 2
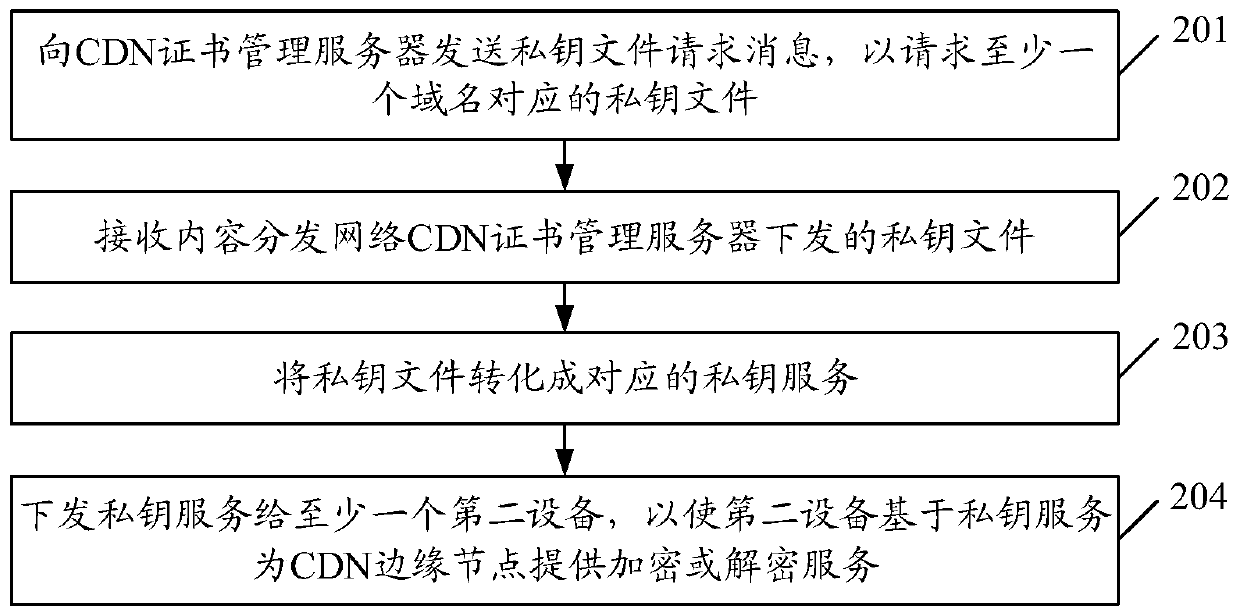
[0061] In order to better reflect the purpose of the present invention, on the basis of Embodiment 1 of the present invention, further illustrations are made, such as figure 2 As shown, the information processing methods specifically include:
[0062] Step 201: Send a private key file request message to the CDN certificate management server to request a private key file corresponding to at least one domain name.
[0063] Step 202: Receive the private key file issued by the content distribution network CDN certificate management server;
[0064] Step 203: converting the private key file into a corresponding private key service;
[0065] Step 204: Issue the private key service to at least one second device, so that the second device provides encryption or decryption service for the CDN edge node based on the private key service.
[0066] Here, the subject of execution of steps 201 to 204 may be the processor of the first device. The first device is used to generate a private...
Embodiment 3
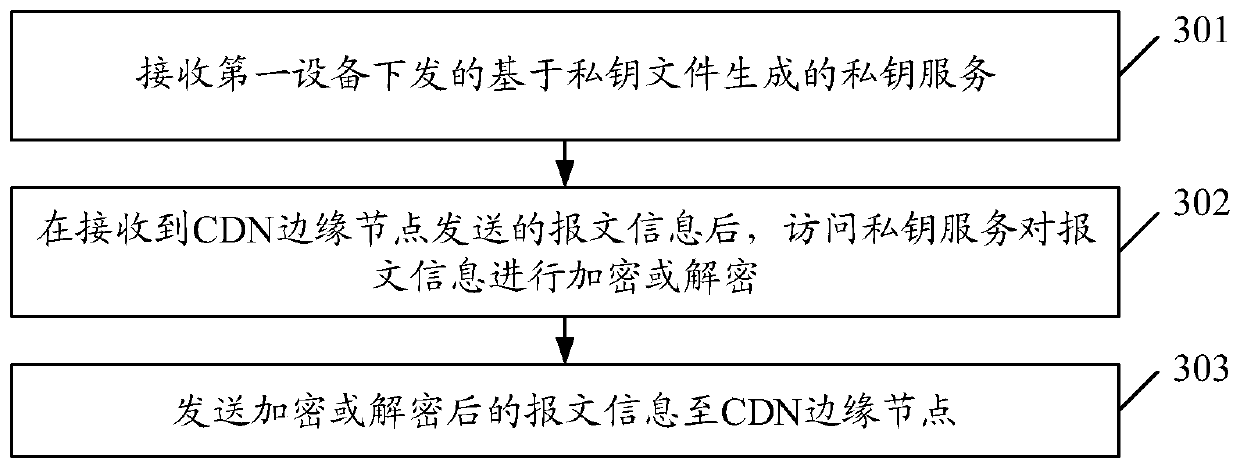
[0075] Based on the same inventive concept, another information processing method is provided in the embodiment of the present invention, which is applied to the second device, such as image 3 As shown, the information processing method includes:
[0076] Step 301: Receive the private key service generated based on the private key file issued by the first device;
[0077] Step 302: After receiving the message information sent by the CDN edge node, access the private key service to encrypt or decrypt the message information;
[0078] Step 303: Send the encrypted or decrypted message information to the CDN edge node.
[0079] Here, the subject of execution of steps 301 to 303 may be the processor of the second device. The first device is used to generate a private key service, and the second device is used to participate in implementing the SSL / TLS handshake request between the terminal device and the CDN edge node based on the private key service.
[0080] Here, the private...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com