Malicious picture interception method, device and equipment and storage medium
A technology of malicious pictures and pictures, applied in the field of information security, can solve the problems of limited interception of malicious pictures and inability to carry out accurate and effective interception, and achieve the effect of reducing audit costs, quickly judging and intercepting, and ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the objectives, technical solutions and advantages of the present application clearer, the embodiments of the present application will be further described in detail below with reference to the accompanying drawings.
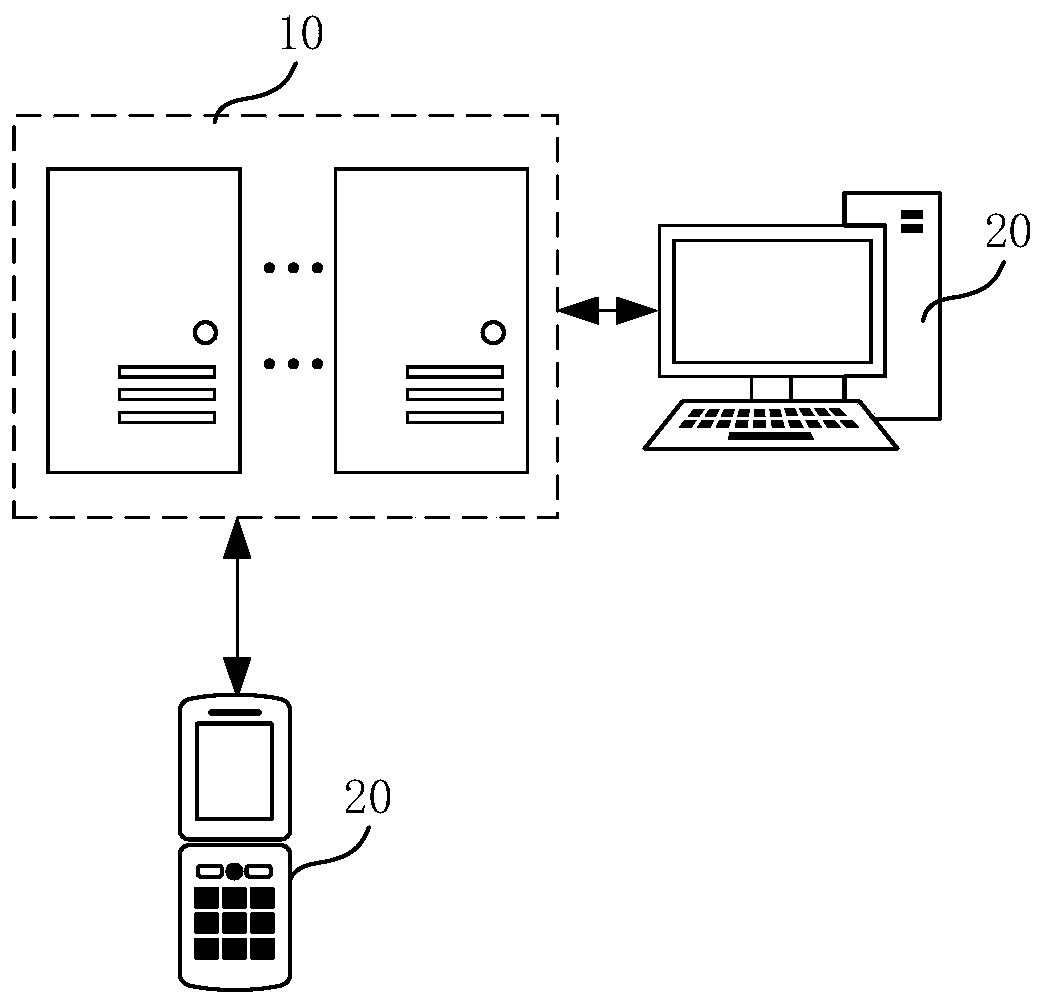
[0034] figure 1 This is a schematic diagram of the system structure of an exemplary embodiment of the present application. see figure 1 , the system is a data transmission network, and the data transmission network includes a server cluster 10, and the server cluster 10 includes one or more interception servers.
[0035] The system also includes a terminal 20, and the terminal 20 is installed with applications such as Weibo, WeChat, Weiyun, etc. that can send pictures (post Weibo, Moments, chat, etc.), store pictures in the cloud, or use pictures as avatars.
[0036] When the terminal 20 performs actions such as sending a picture, storing a picture in the cloud, or using a picture as an avatar, the interception server 10 will obtain the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com