A node vulnerability estimation method and system based on heterogeneous information network
A heterogeneous information network, vulnerability technology, applied in transmission systems, electrical components, etc., can solve problems such as inability to analyze network attacks well, unfavorable analysis of a large number of nodes, and difficulties in dynamic network analysis.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
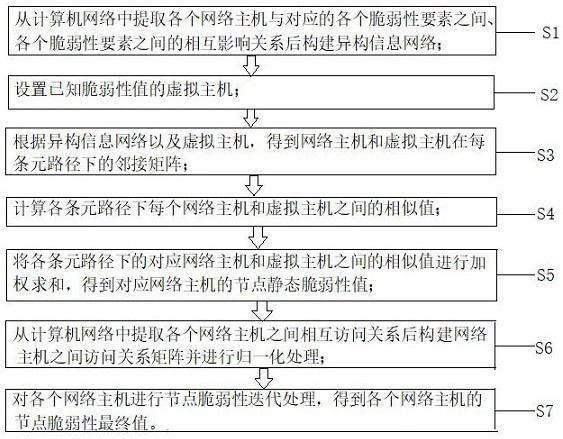
[0061] This embodiment provides a node vulnerability estimation method based on heterogeneous information network, refer to figure 1 , the node vulnerability estimation method includes the following steps:
[0062] Step 1, extracting from the computer network the mutual influence relationship between each network host and each corresponding vulnerability element, and each vulnerability element, and constructing a heterogeneous information network.
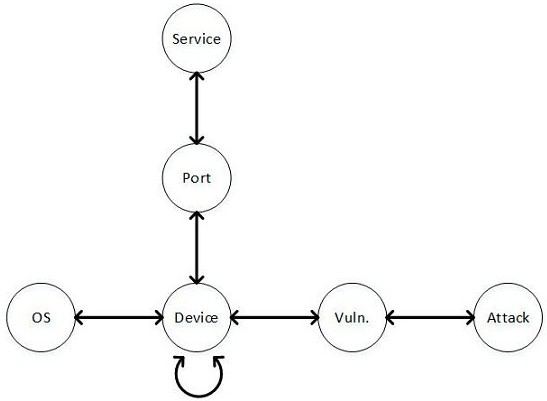
[0063] The vulnerability elements in this embodiment include host H, operating system O, port P, service S, vulnerability V, and attack type A. In this embodiment, the host H, the operating system O, the port P, the service S, the vulnerability V, and the attack type A (attack caused by the vulnerability) are used as the node types, and through 11 different mutual influence relatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com