Extensible network attack behavior classification method
A classification method and network attack technology, applied in the field of scalable network attack behavior classification, can solve the problems of low detection efficiency, low accuracy rate, high misjudgment rate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described according to the following examples, and the mode of the present invention includes but not limited to the following examples.
[0033] The present invention comprises the following steps:
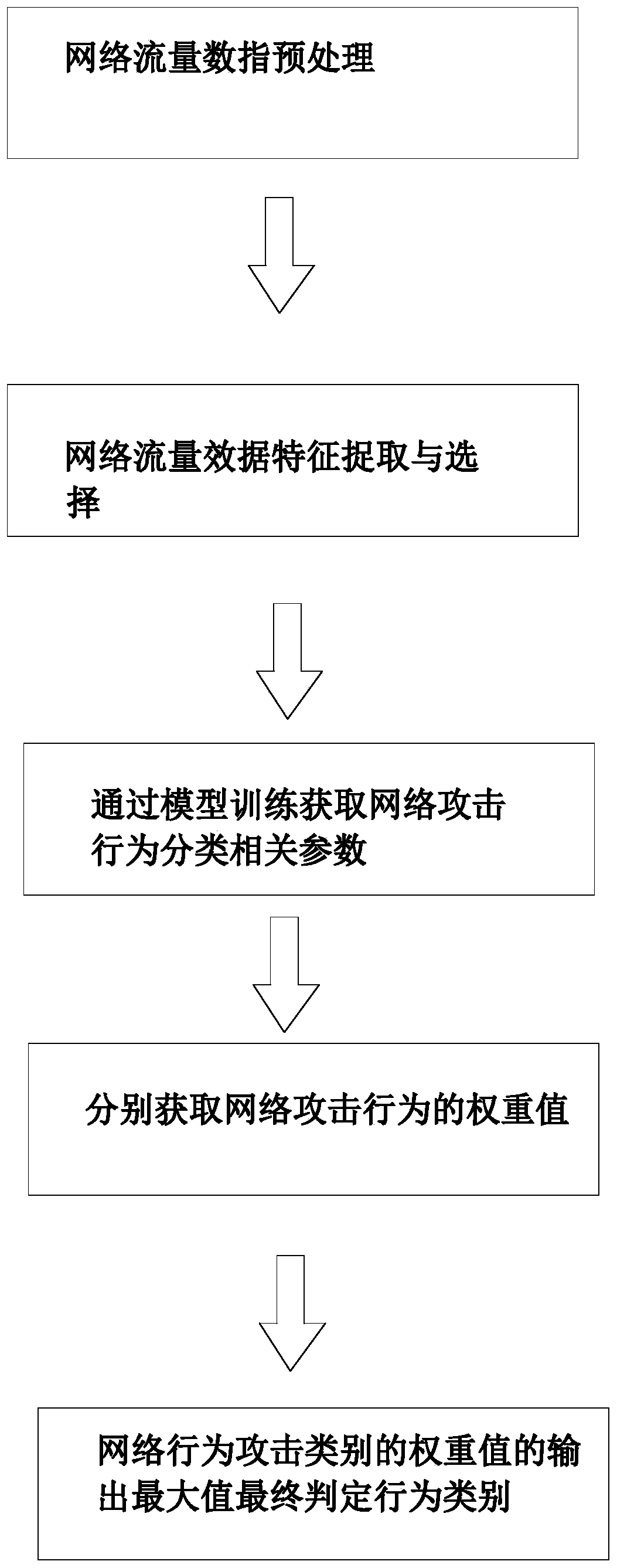
[0034] Such as figure 1 As shown, it is a flow chart suitable for the network attack behavior classification method. This method obtains the network traffic data through the network server log and performs preprocessing. Firstly, the relevant model training is used to obtain the network attack behavior judgment parameters, and then the network behavior is initially judged, respectively. Calculate the weight values of various network behavior categories including normal behavior, known attack categories, and unknown attack categories, and finally make a final judgment on the network attack type based on the weight values.
[0035] Step S10: Preprocessing of network traffic data
[0036] This step obtains network traffic data based o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com