Recommendation method based on privacy protection
A recommendation method and privacy protection technology, applied in the direction of digital data protection, data processing applications, sales/lease transactions, etc., can solve problems such as no solution, and achieve the effect of reducing computing costs and protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
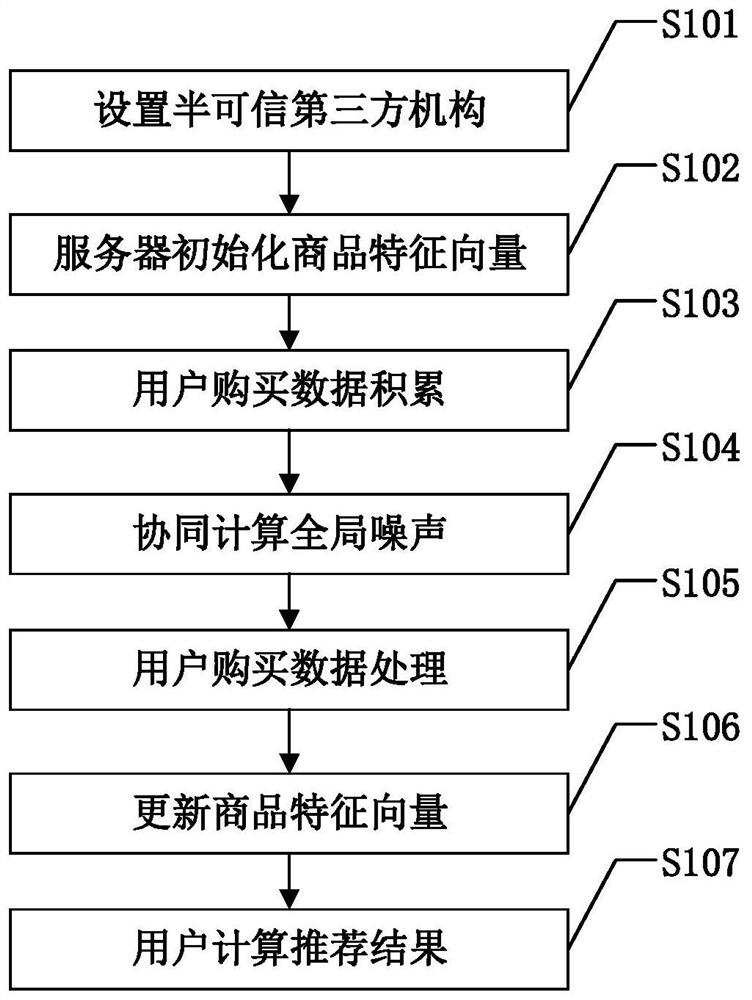
[0040] figure 1 This is a flow chart of the specific implementation of the privacy protection-based recommendation method of the present invention. like figure 1 As shown, the specific steps of the privacy protection-based recommendation method of the present invention include:
[0041] S101: Set up a semi-trusted third-party organization:
[0042] A semi-trusted third party is set up between the user and the e-commerce platform server. Semi-trusted third-party organizations have the following two characteristics:
[0043] 1) Honest: The institution will complete its own tasks in accordance with the agreed agreement, and will not tamper with the information sent by users;
[0044] 2) Curious: The agency will use the received information to find ways to make profits for itself; for example: use the intermediate calculation results sent by users to find ways to mine users' preferences and resell to other platforms.
[0045] In the field of e-commerce, semi-trusted third-par...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com