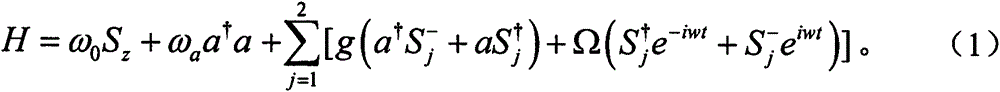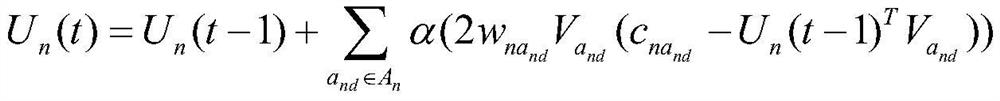Patents
Literature
32results about How to "Prevent knowing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
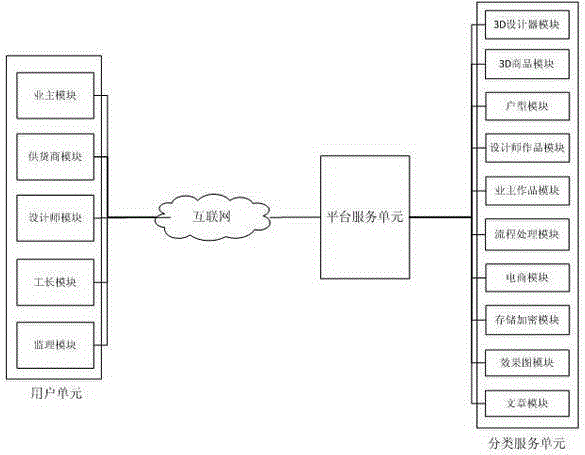
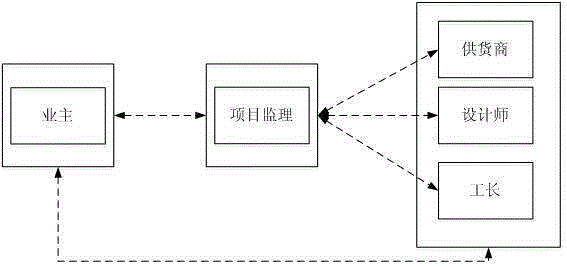
Home decoration network platform system and use method
The present invention relates to a safe and reliable home decoration network platform system and a use method. The safe and reliable home decoration network platform system comprises a platform service unit, a classification service unit and a user unit connected with the platform service unit by the internet; the platform service unit is used for input, output and processing of information between the user unit and the classification service unit; the user unit means a platform character relationship and comprises a home owner module, a supplier module, a designer module, a foreman module and a supervisor module; the classification service unit comprises a 3D designer module, a 3D commodity module, a house type module, a designer works module, a home owner works module, an E-commerce module and a flow processing module; online design on the home decoration platform system is implemented and a user carries out online design and previews a design effect in advance; a designer carries out online design and shows public works and the user directly enjoys and selects the works of the designer on a platform; and a total charge supervision function is provided for the integral home decoration project, the integral project can be orderly propelled to be successfully carried out and contract breakage or wrangle is avoided.
Owner:HENAN XINSHAN INFORMATION TECH
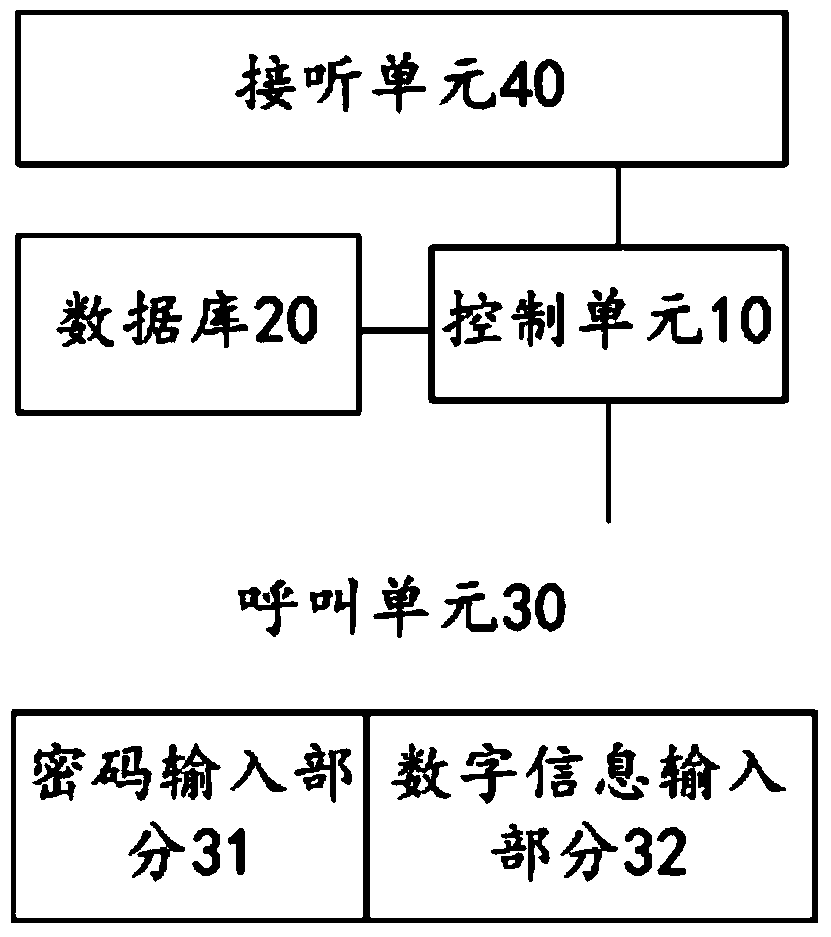
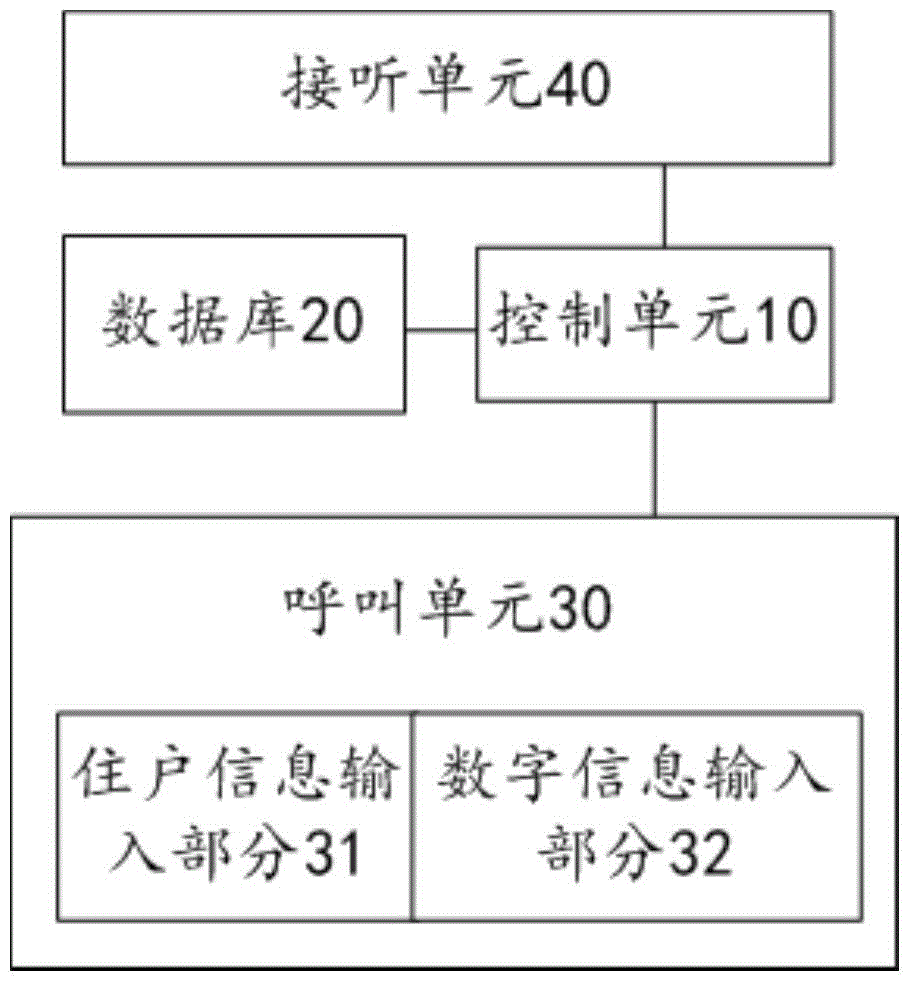
Electronic entrance guard system of residential area
The invention provides an electronic entrance guard system of a residential area. The electronic entrance guard system comprises a control unit, a calling unit and a plurality of answering units, wherein the calling unit is used for inputting calling information; the control unit is used for starting one of the answering units according to the calling information input by the calling unit and is also used for comparing a received input calling signal with a plurality of pieces of preset calling information after receiving the input calling signal from a password input part and a digit information input part; if the received input calling signal is consistent with one of the multiple pieces of the preset calling information, the control unit switches on the answering unit of the multiple answering units, which corresponds to one of the multiple pieces of the preset calling information consist with the received input calling signal; if the received input calling signal is not consistent with any piece of the preset calling information in the multiple pieces of the preset calling information, the control unit does not switch on any answering unit.
Owner:朱佩芬
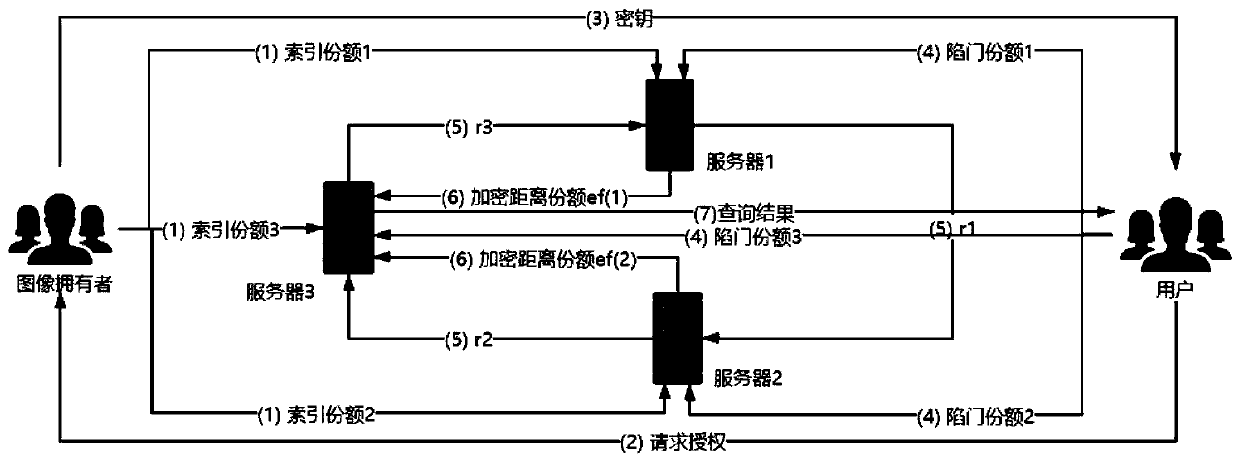
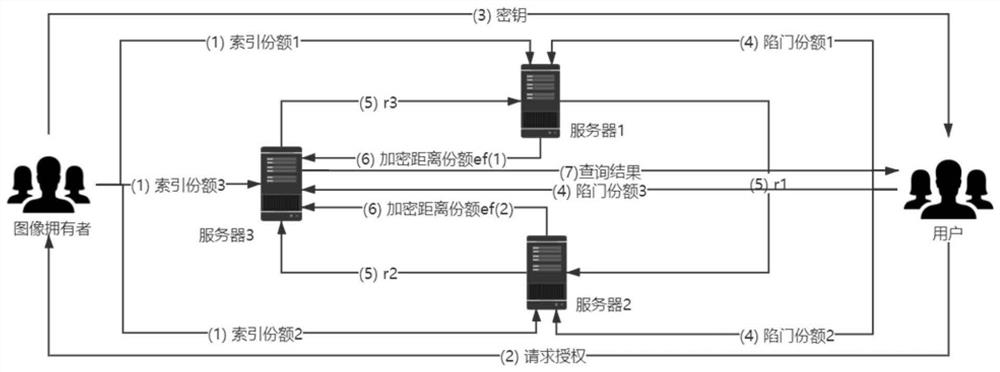
Image security retrieval method based on secret sharing in cloud environment
ActiveCN111541679AProtection securityIncrease the difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextEngineering
The invention aims to provide an image security retrieval scheme based on secret sharing in a cloud environment, which realizes security retrieval of a cloud image by constructing an index share and atrap door share. A data owner generates a ciphertext image and an index share and uploads the ciphertext image and the index share to a cloud, during query, a user generates a trap door share and sends the trap door share to the cloud, and the cloud can calculate a distance share and return the ciphertext image closest to the query image, so that the security problem caused by using a unified keyfor encryption in an existing scheme can be solved. In order to prevent an attacker from analyzing image similarity information according to an original Euclidean distance to speculate an image, a random number and a secure multi-party calculation method are used to encrypt a distance share. The security of the scheme depends on a secret sharing technology, the common precision loss problem in image security retrieval is solved, and the retrieval precision is almost consistent with that of plaintext domain image retrieval.
Owner:WUHAN UNIV
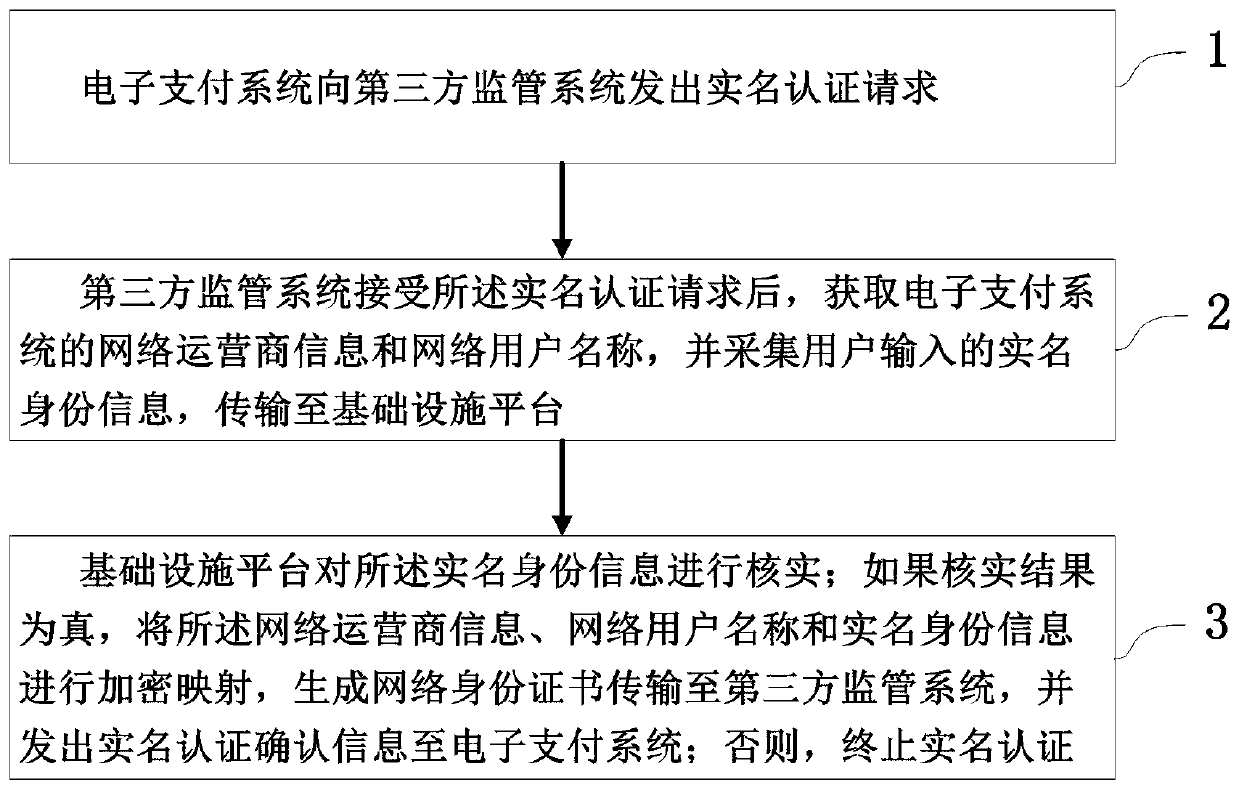
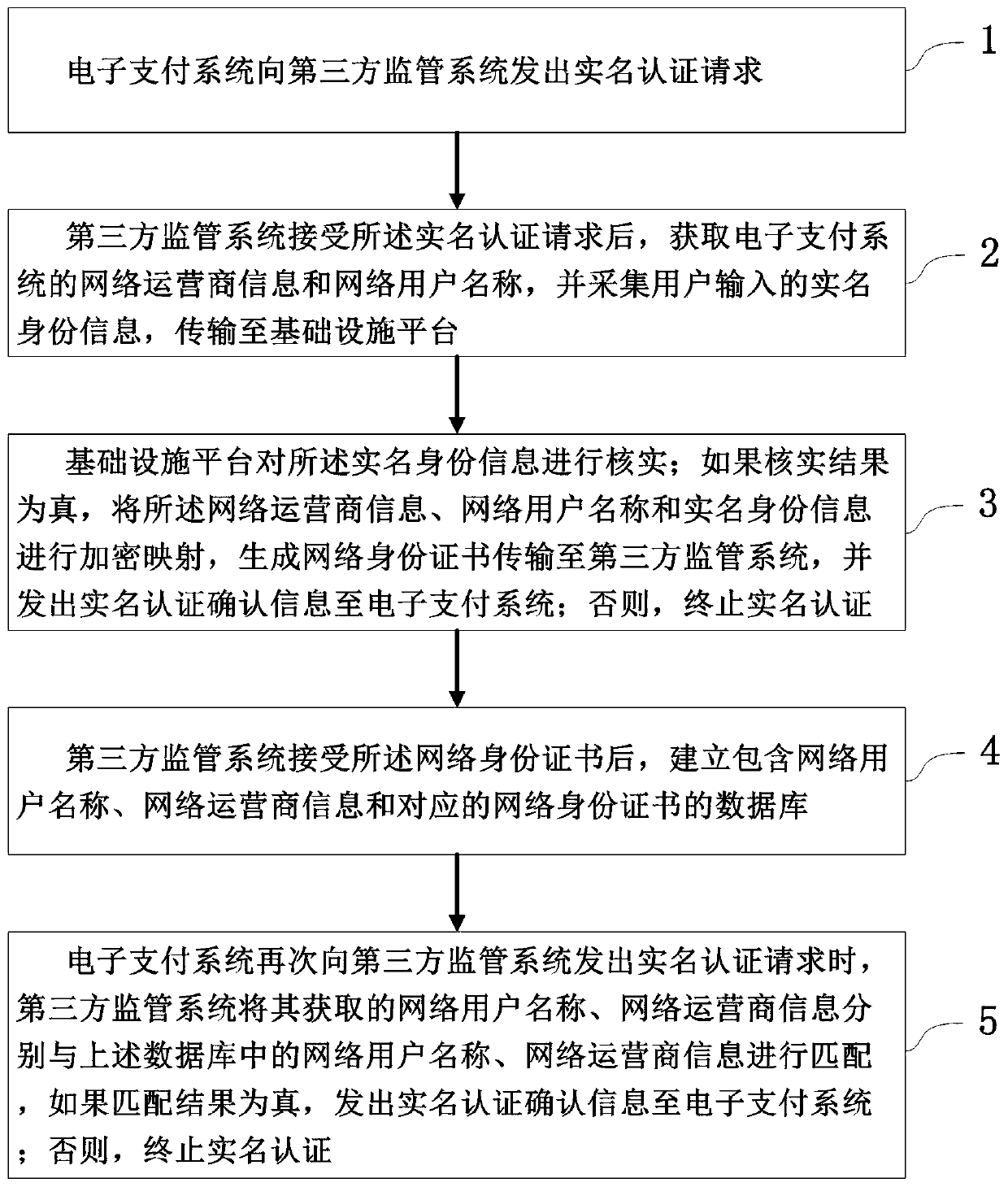
User identity real-name authentication method of an electronic payment system
ActiveCN109829722AGuaranteed operational safetyEffective protectionProtocol authorisationThird partyInformation security
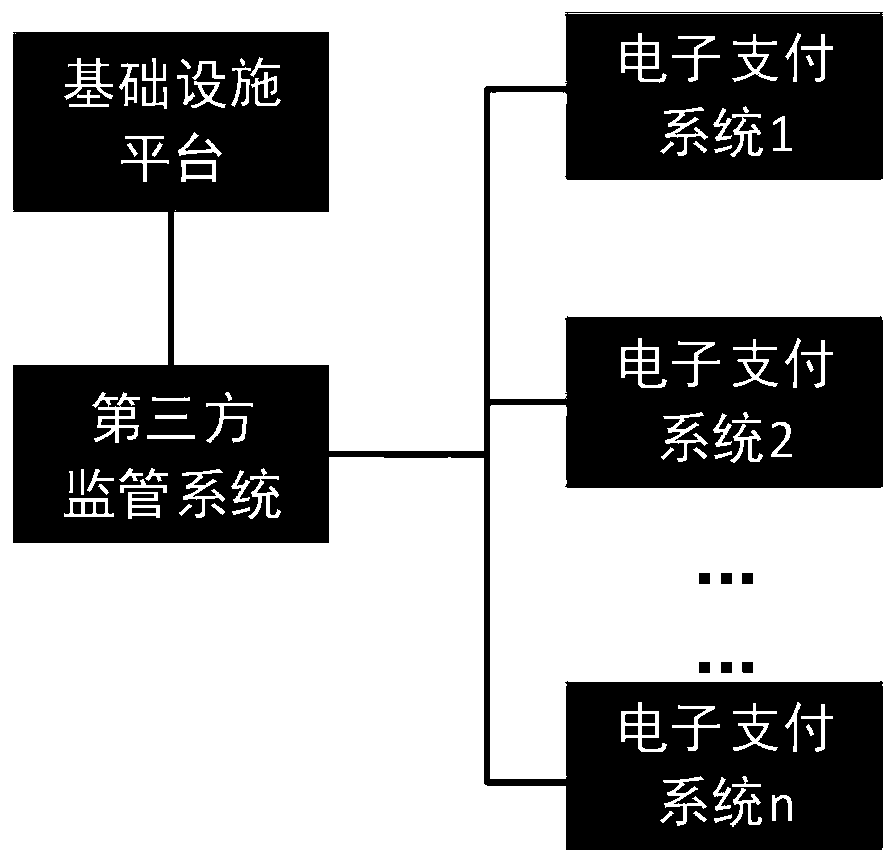
The invention relates to a user identity real-name authentication method of an electronic payment system, belongs to the technical field of network information security, and solves the problem that real-name authentication is unsafe and unreliable in the prior art. The method comprises the following steps that an electronic payment system sends a real-name authentication request to a third-party supervision system; After receiving the real-name authentication request, the third-party supervision system acquires network operator information and a network user name of the electronic payment system, acquires user real-name identity information and transmits the user real-name identity information to the infrastructure platform; The infrastructure platform verifies the real-name identity information; If the verification result is true, performing encryption mapping on the network operator information, the network user name and the real-name identity information, generating a network identity certificate, transmitting the network identity certificate to a third-party supervision system, and sending real-name authentication confirmation information to an electronic payment system; Otherwise, the real-name authentication is terminated. According to the method, a third-party supervision system is combined with a network identity certificate, so that the privacy of a user is protected,and the person and the certificate are the same.
Owner:XINGTANG TELECOMM TECH CO LTD +1
Semiconductor device, unique ID of semiconductor device and method for verifying unique ID
InactiveCN101086757AReduce laser trimming timesShorten production timeSemiconductor/solid-state device detailsSolid-state devicesValidation methodsOriginal data
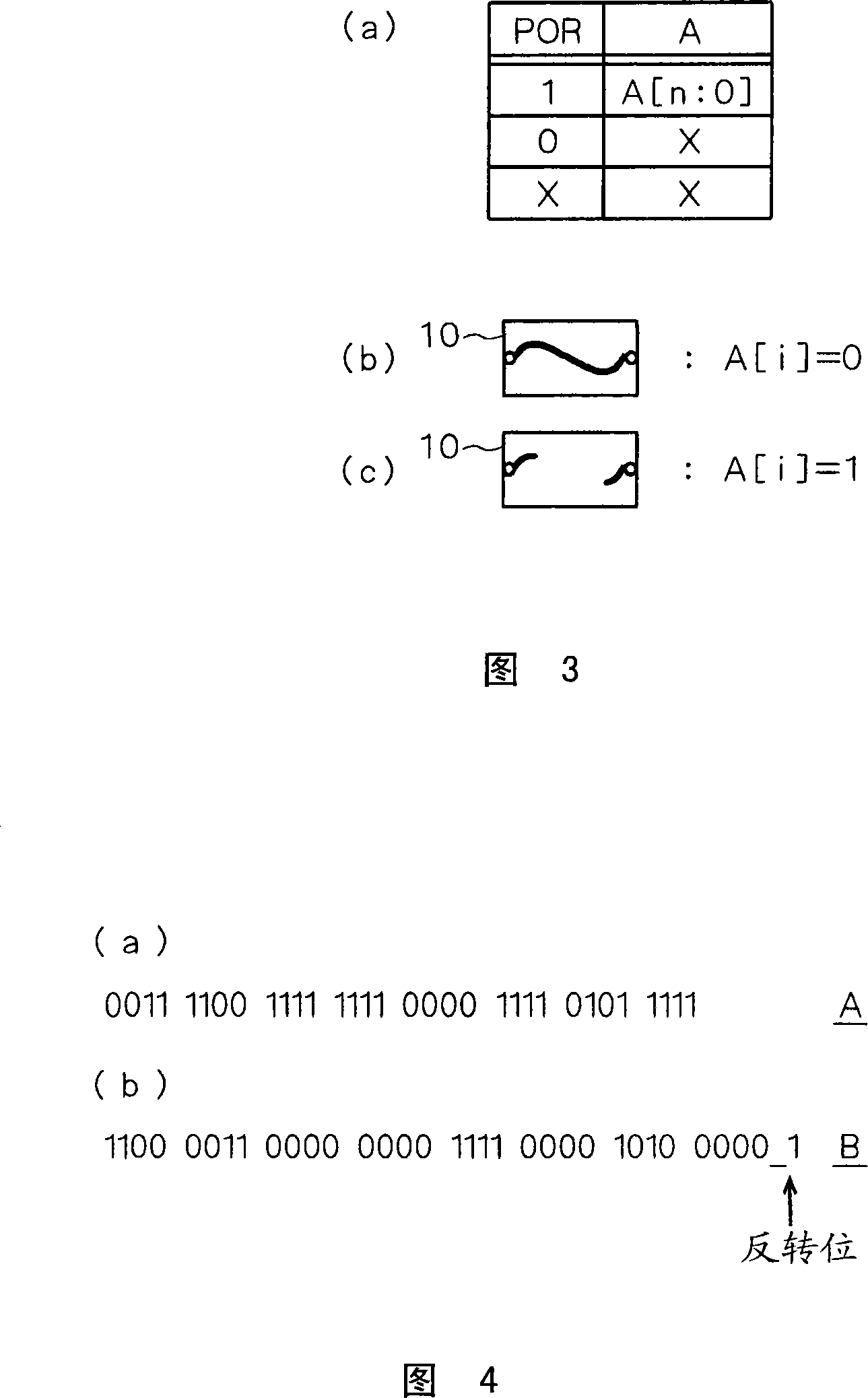
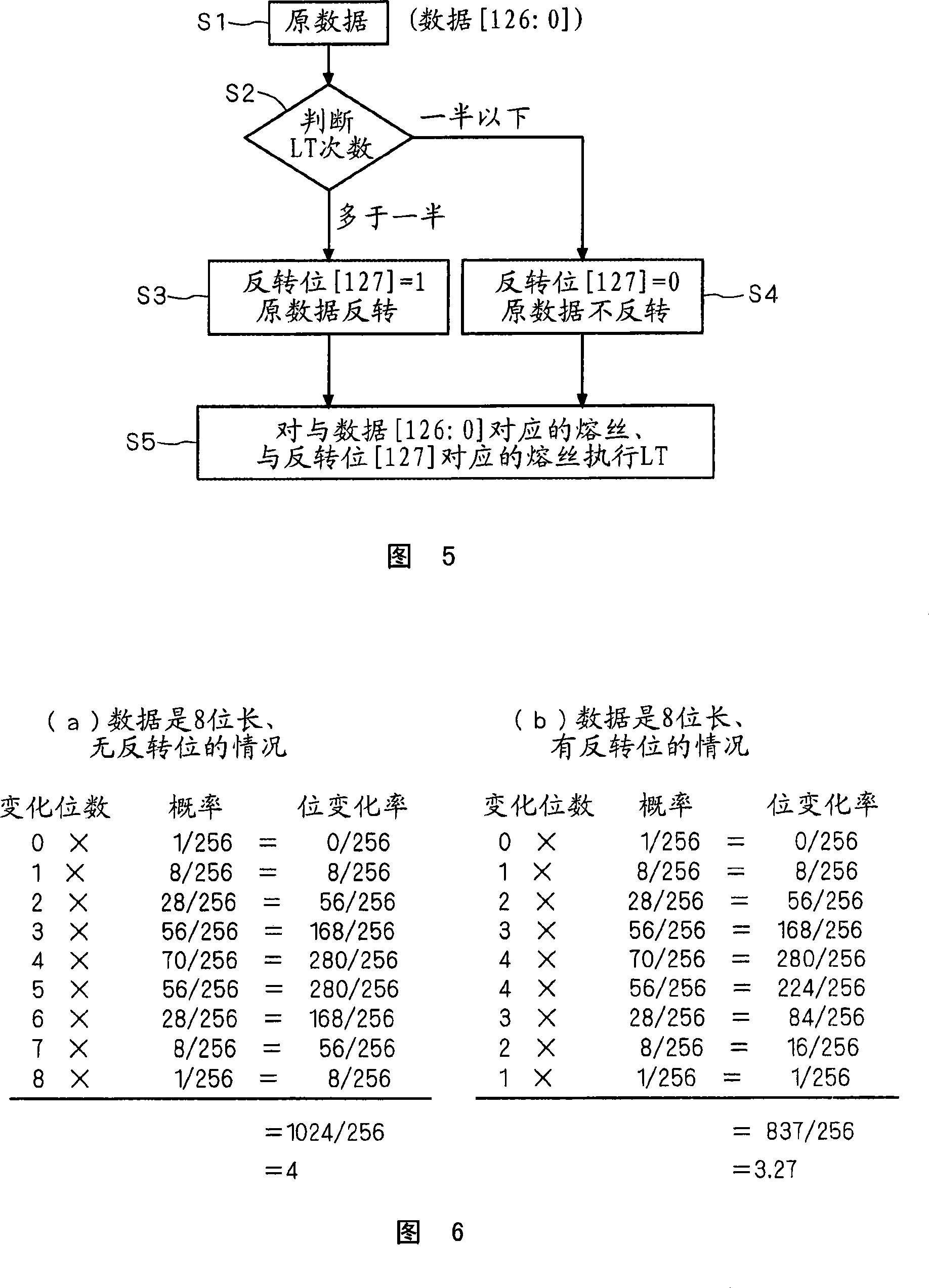
The present invention relates to a semiconductor device, a unique ID of the semiconductor device and a method for verifying the unique ID. Thus, original data (bit string) having 127-bit length [126:0] is inputted at step S1 . Then, it is determined whether the number of bits of ''1'' in the bit string [126:0] inputted at the step S 1 is more than the half of the bits of the bit string (that is, not less than 64) or not at step S2 . When the number is not less than 64, the process proceeds to step S3 . At the step S3 , the bit string [126:0] is inverted and an invert bit [127] is set to ''1''. Then, the process proceeds to step S5 . At the step S5 , the fuse corresponding to the bit string [126:0] and the bit [127] are cut by LT.
Owner:RENESAS TECH CORP
Safe query method, device and system of high-dimensional spatial data
ActiveCN105303121AAvoid gettingPrevent knowingDigital data protectionHigh dimensionalComputer science
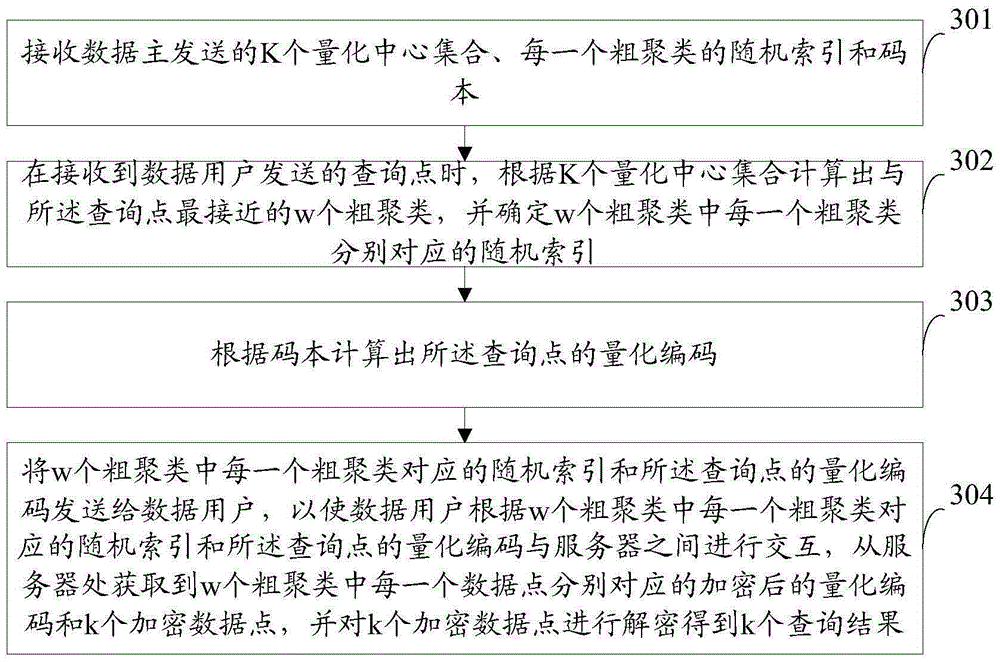
The invention provides a safe query method, device and system of high-dimensional spatial data. The method comprises the following steps: a data owner sends K quantization center sets, the random indexes of each coarse cluster and a codebook to private cloud, sends an encrypted outsourced database, the random indexes of each coarse cluster, the quantization code of each encrypted data point and a homomorphic private key to a server and sends a homomorphic encrypted distance table and an encryption key to a data user; and the data user obtains the random indexes independently corresponding to w coarse clusters and the quantization code of the query point form the private cloud, obtains the quantization code of each data point and k encrypted data points in the w coarse clusters, and carries out encryption to obtain k query results. According to the scheme, the data in the outsourced database and data user query contents can be effectively prevented from being pried by the server, and the user can be prevented from prying into data except the query content of the user.
Owner:XIDIAN UNIV
Customization method for computer starting process and computer
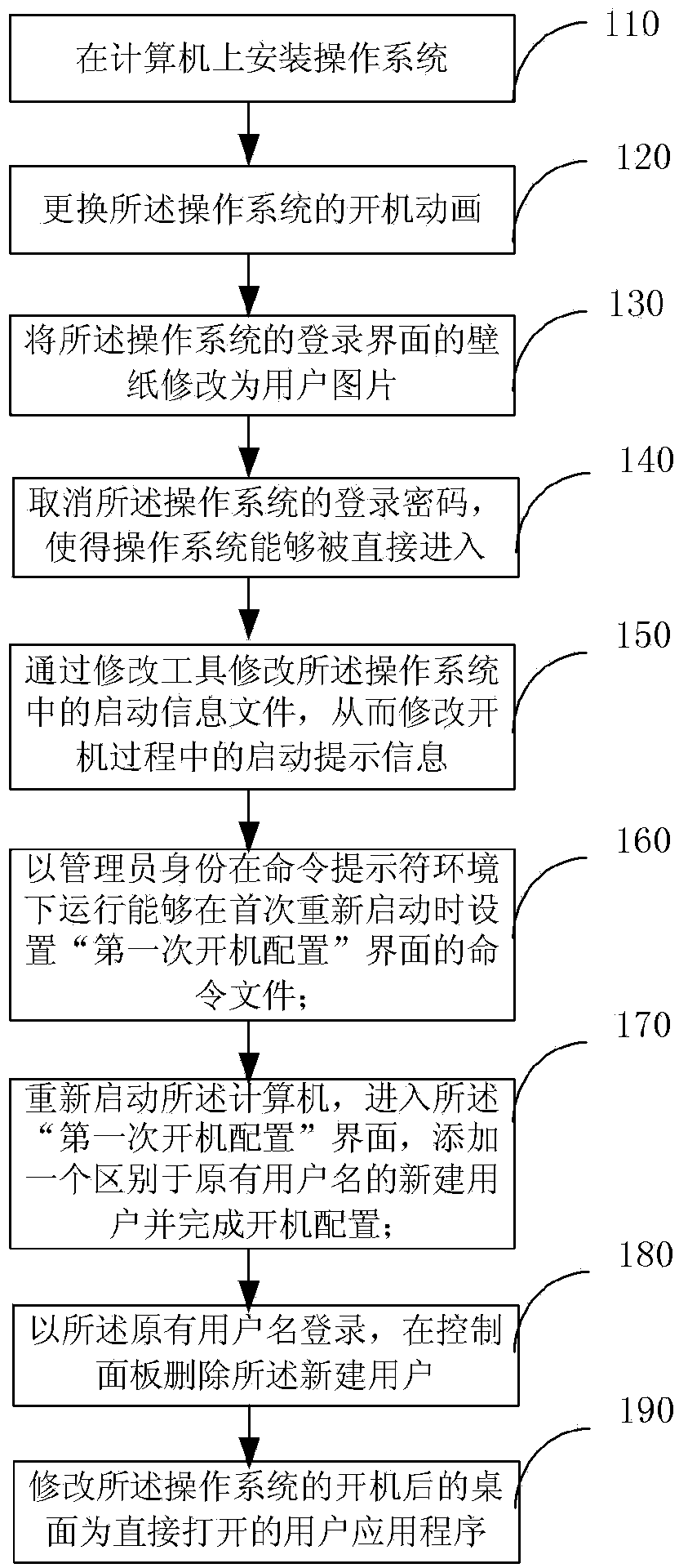
InactiveCN103559050AMaintain information securityUnify and enhance the imageDigital data protectionProgram loading/initiatingPersonalizationOperational system
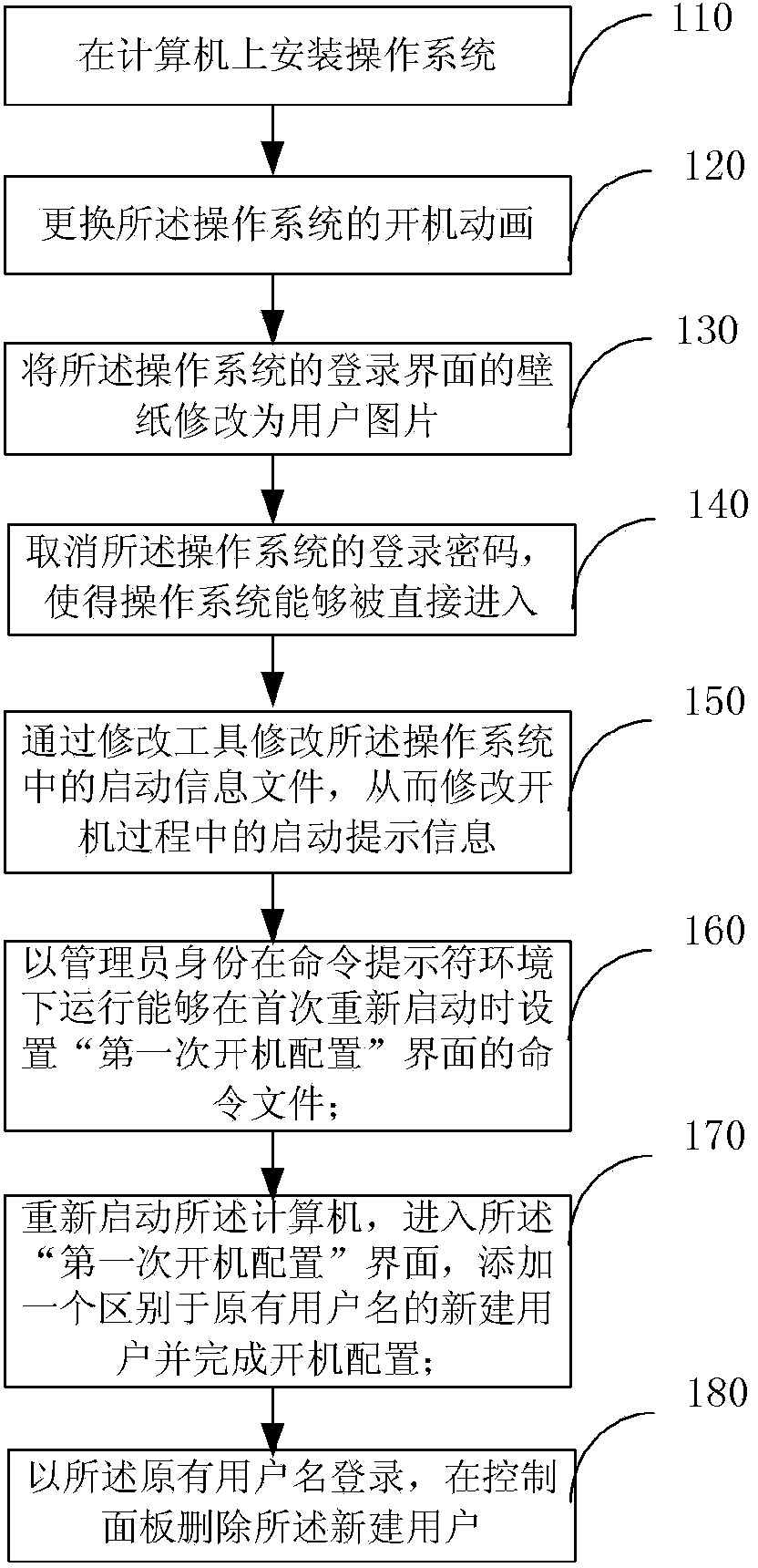
The invention provides a customization method for a computer starting process and a computer. The method includes A. installing an operation system on the computer; B. replacing starting animation of the operation system; C. changing wall paper of a login interface of the operation system into a user picture; D; canceling a login password; E. modifying a starting information file in the operation system to modify starting prompt information; F. operating a command file capable of setting a first-time starting configuration interface during first-time restarting under the command prompt environment in the identity of an administrator; G. restarting the computer, entering the first-time starting configuration interface, adding a newly-built user different from an original user name and finishing starting configuration; H. logging in the system through the original user name and deleting the newly-built user in a control panel. By means of the method, users can hide the operation system information of themselves, system safety and confidentiality are improved, a personalized starting process can be provided, and a user image is improved.
Owner:TVMINING BEIJING MEDIA TECH
Internet of vehicles anonymous security evidence obtaining method and system based on blockchain technology
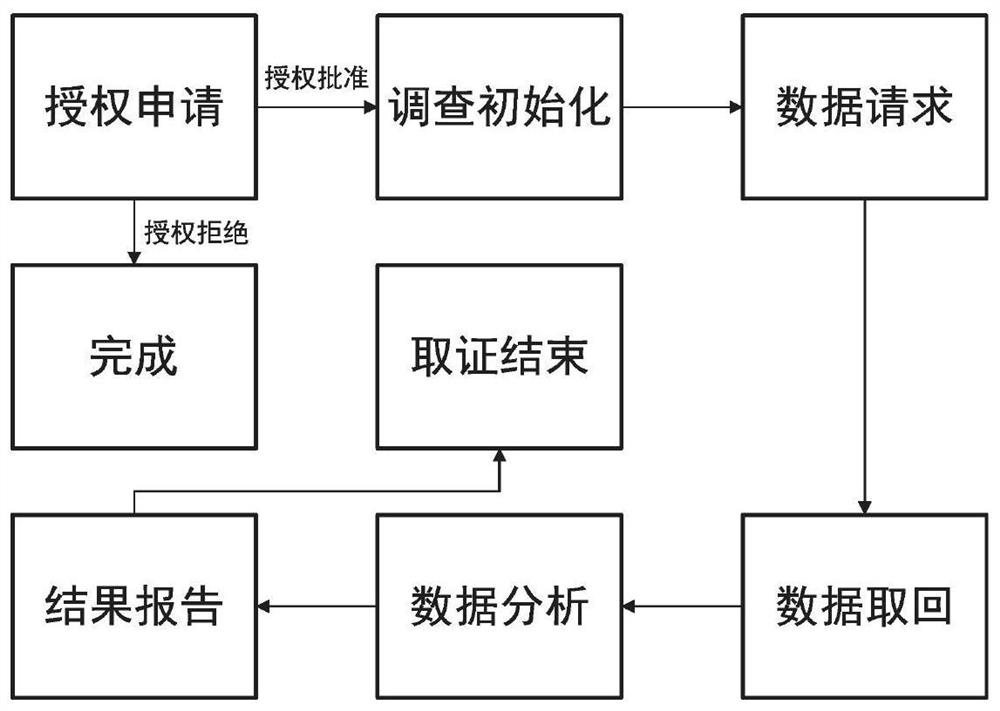
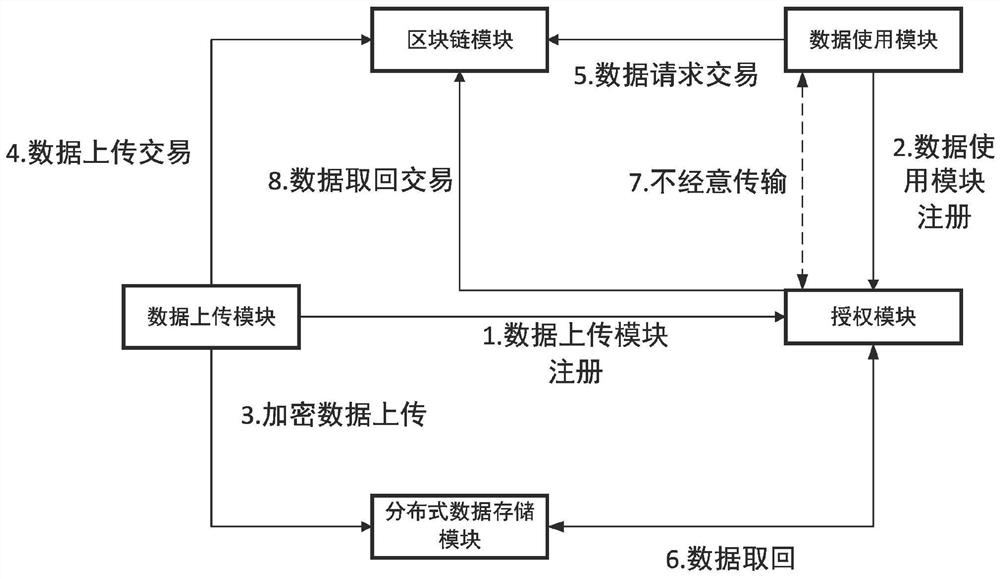
ActiveCN112906036APrevent knowingEnsure identity anonymityFinanceDatabase distribution/replicationBlockchainData Property
The invention discloses an Internet of Vehicles anonymous security evidence obtaining method and system based on a blockchain technology. The Internet of Vehicles anonymous security evidence obtaining method and system are applied to a network environment composed of a plurality of data uploading modules, a plurality of data using modules, a plurality of authorization modules, a blockchain module and a distributed data storage module. The data uploading module preprocesses and encrypts the data, uploads the data to the distributed data storage module, and sends a corresponding transaction to the blockchain module; the data use module sets required data attributes, generates a range proof and sends the range proof to the blockchain module; the authorization module is responsible for initialization of the whole evidence obtaining system, tracing of evidence obtaining data and authorization approval operation, and participates in maintenance of blockchain nodes; the blockchain module is composed of a plurality of nodes, so that the whole system can supervise the transparency and legality of evidence obtaining; and the distributed data storage module is used for storing the encrypted evidence obtaining data and generating a downloading link. According to the invention, the confidentiality and traceability of evidence obtaining data can be protected.
Owner:HEFEI UNIV OF TECH
An information processing method and an electronic apparatus
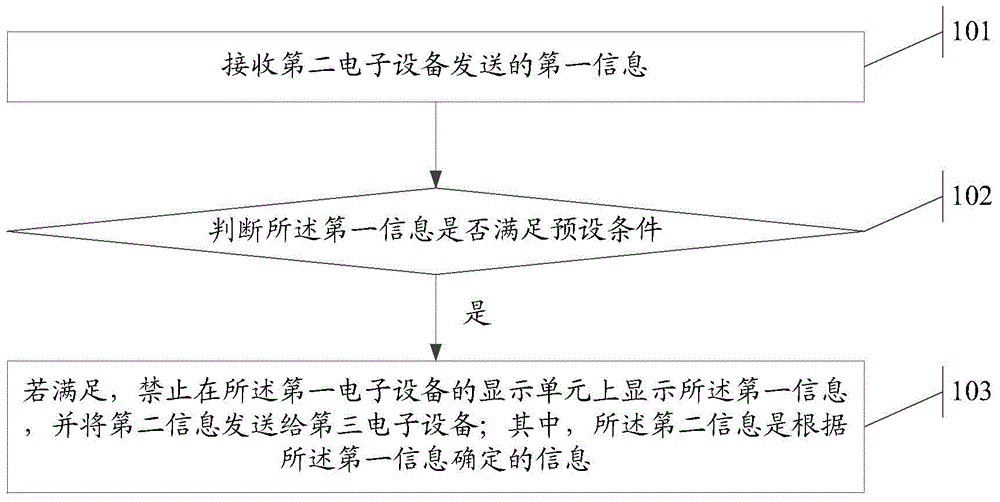
InactiveCN106033517ARealize instant forwardingRealize instant deliveryDigital data protectionInformation processingLibrary science
The invention provides an information processing method applied to a first electronic apparatus and aims to solve the technical problem in the prior art that information leak is caused by poor information processing capability of electronic apparatuses. The method comprises the steps of receiving first information sent by a second electronic apparatus; judging whether the first information meets preset conditions; if yes, forbidding the display of the first information on a display unit of the first electronic apparatus and sending second information to a third electronic apparatus, wherein the second information is information determined according to the first information. The invention also provides the corresponding electronic apparatus.
Owner:LENOVO (BEIJING) CO LTD
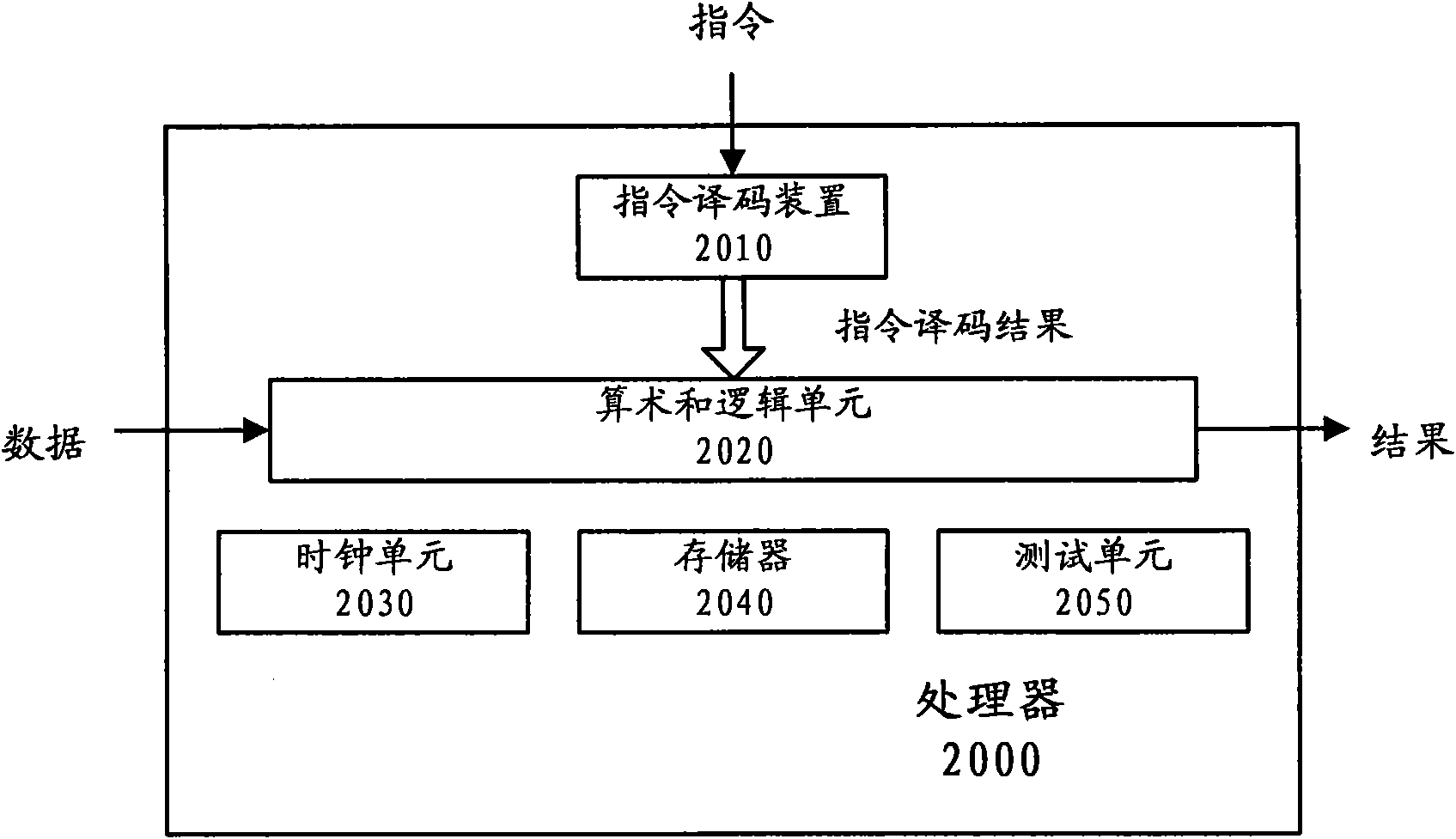
Command decoding device and method for disordered coded commands
ActiveCN101996066AImprove securityPrevent knowingConcurrent instruction executionComputer hardwareUnit of selection
Owner:北京多思技术服务有限公司
Cavity QED-based quantum privacy comparison method
ActiveCN106161014APrevent knowingHigh qubit efficiencyKey distribution for secure communicationThird partyQuantum entanglement
The invention discloses a cavity QED-based quantum privacy comparison method by virtue of adequate utilization of an evolution law of atoms in cavity QED. A third party is allowed to wrongly act according to his / her willing but cannot conspire with any one of two users. According to the method, a two-atom product state but not an entangled state is taken as an initial quantum resource which is only needed to be applied to single atom measurement of the two users; unitary operation and quantum entanglement quantum entanglement operation are unnecessary in the method of the invention; the equality of one bit of each user can be compared by virtue of one two-atom product state in each round of comparison; the external attack and the attack of a participant can be resisted; particularly, the secrets and even a comparison result of the two users cannot be known by the third party; and furthermore, the quantum comparison efficiency reaches up to 50%.
Owner:嘉兴市顺凯鹿科技有限公司
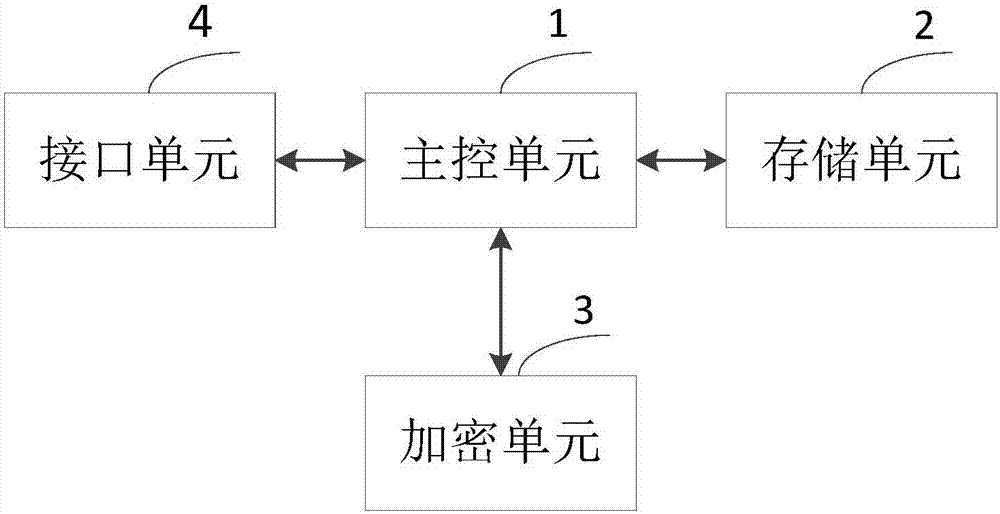
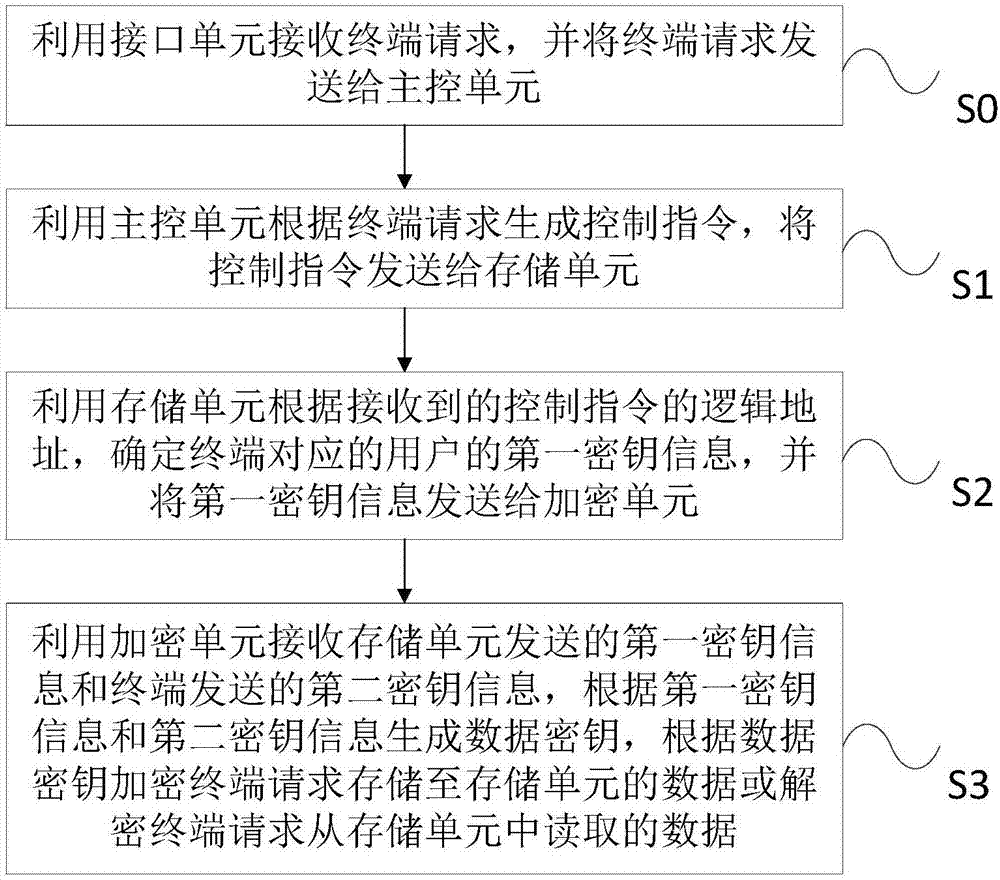
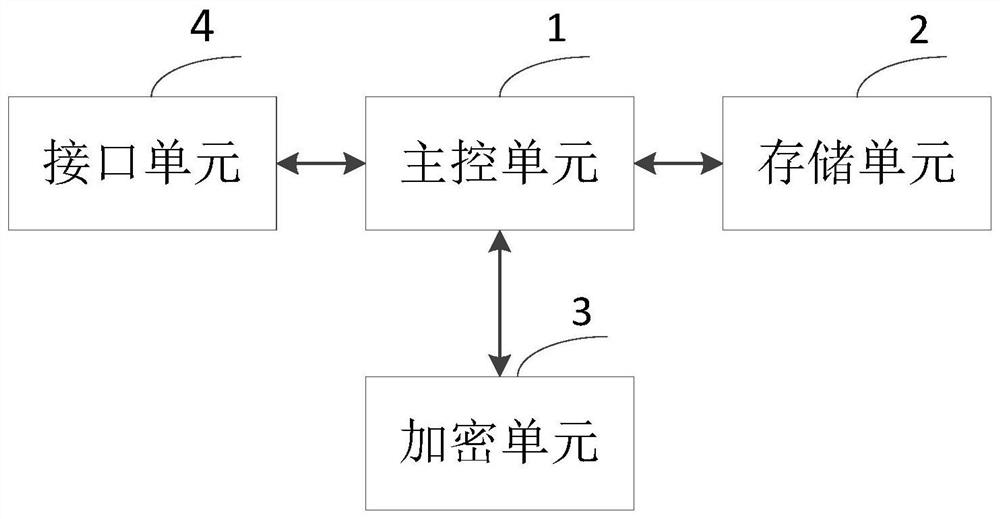
Safe storage device, system and method
ActiveCN107967432AImplement hardware encryption protectionImprove reliabilityInternal/peripheral component protectionDigital data authenticationComputer terminalSafe storage
The invention provides a safe storage device, system and method. The device comprises a main control unit, a storage unit and an encryption unit, wherein the main control unit is used for generating acontrol instruction according to a terminal request and sending the control instruction to the storage unit; the storage unit is used for determining first secret key information, corresponding to the control instruction, of a user according to the logic address of the received control instruction and sending the first secret key information to the encryption unit; the encryption unit is used forreceiving the first secret key information sent by the storage unit and second secret key information sent by a terminal, and generating a data secret key according to the first secret key information and the second secret key information. The invention provides the safe storage device, system and method. By additionally arranging the encryption unit, the secret key information is stored separately, a secret key can be effectively prevented from being known by an illegal user, the safety of the secret key is guaranteed, and the data safety is ensured.
Owner:爱国者安全科技(北京)有限公司
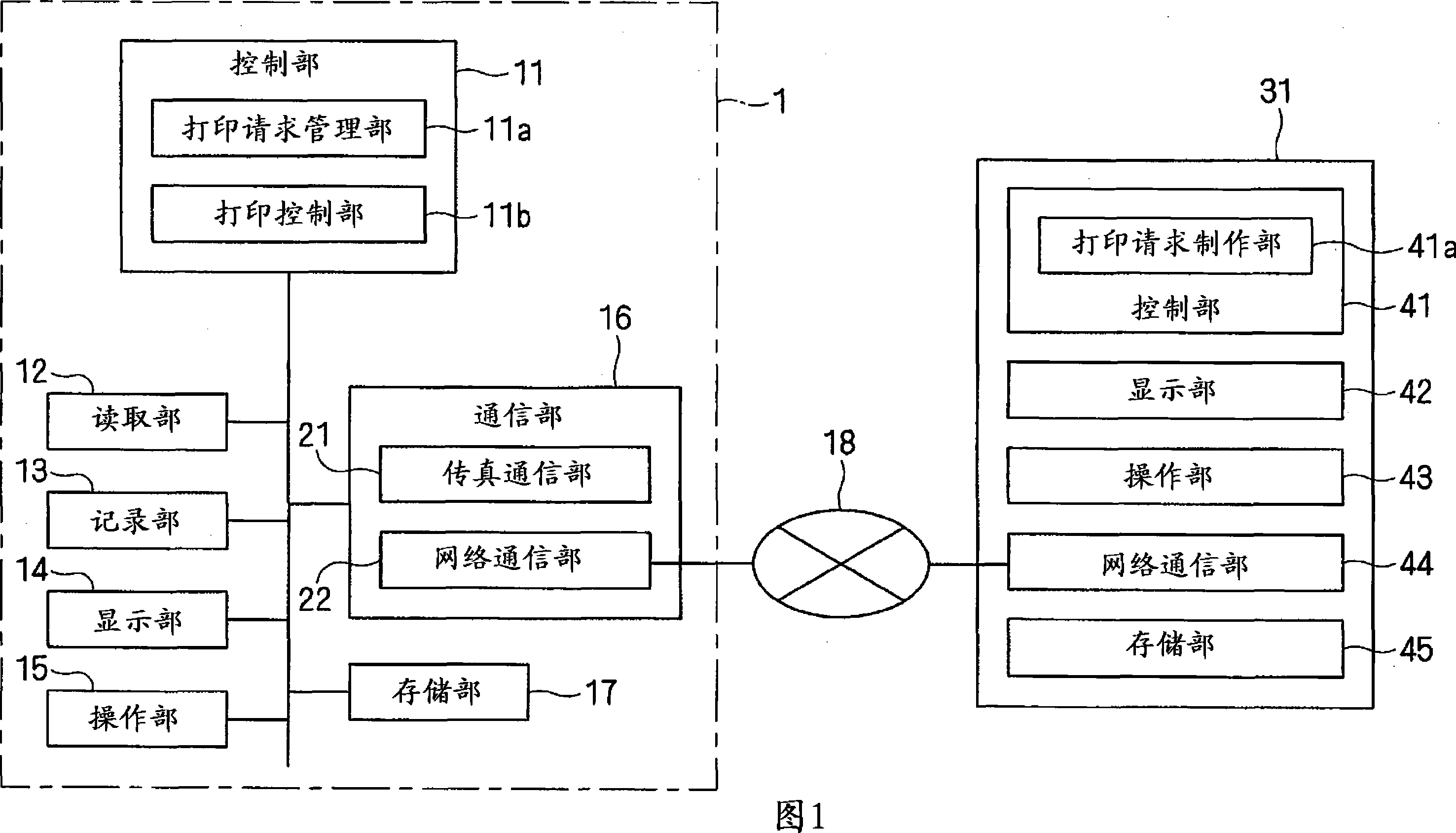
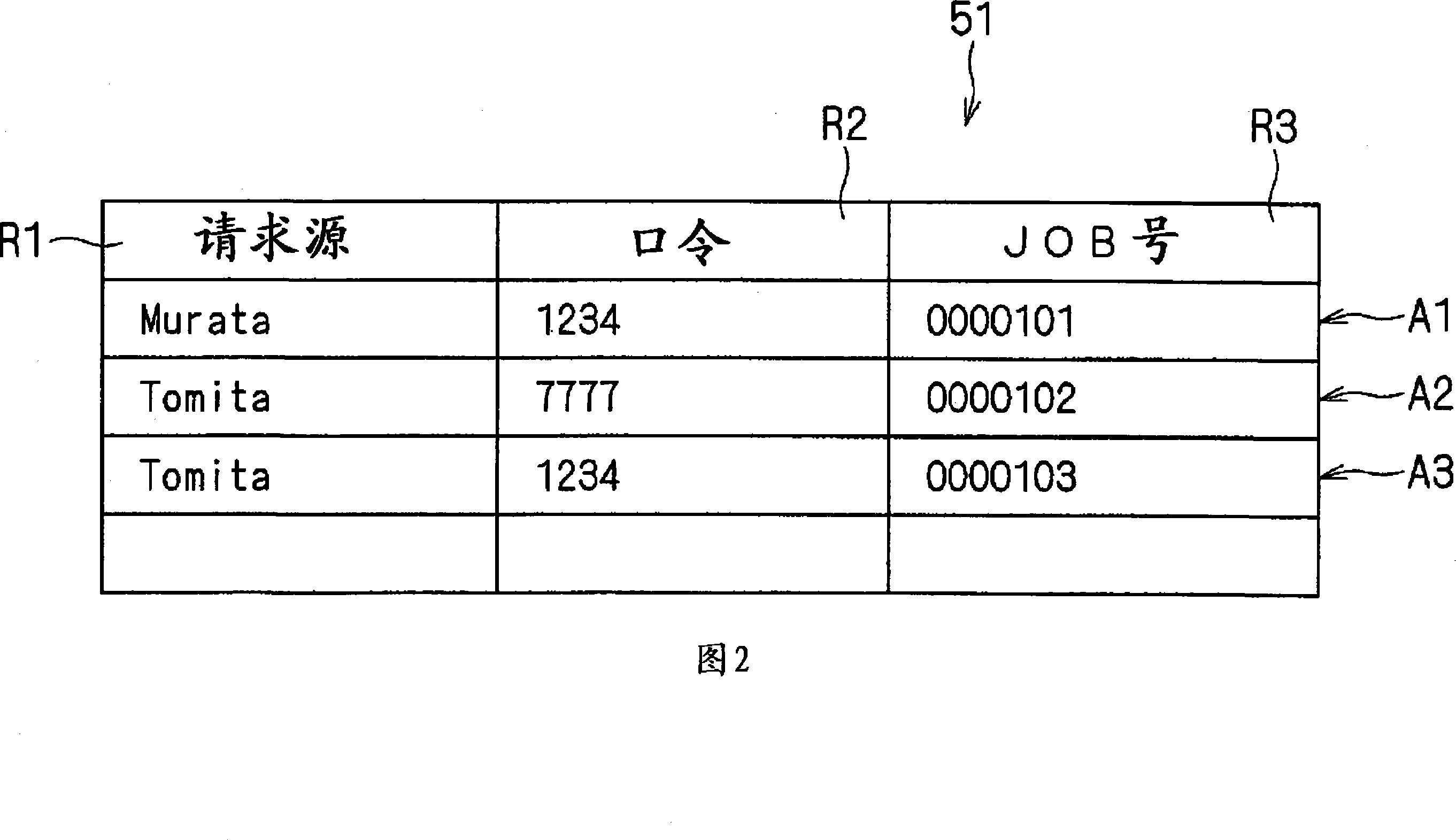
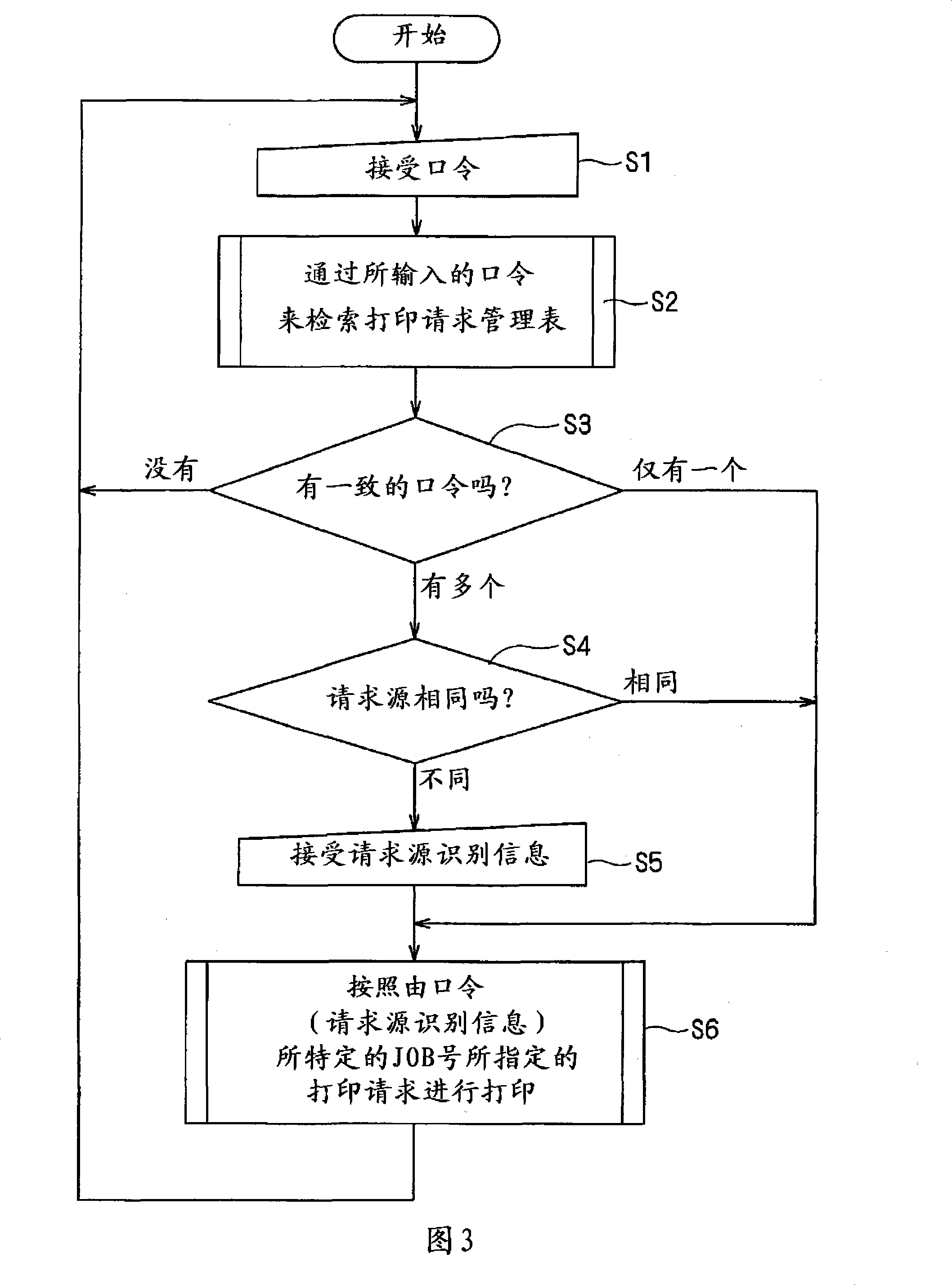
Printing device and information processing system using the same
InactiveCN101178641ASimplify typingPrevent MisprintingDigital data authenticationDigital output to print unitsInformation processingPassword
The invention provides a printing device and an information processing system using the same. The printing device includes a table storage unit that stores a print request management table in which a password, request source identification data for identifying the external processing apparatus which has transmitted the print request and a job code for specifying the print request are coordinated with each other; and a print control unit that requests entry of a password and, when the password is entered, searches the print request management table and, when there is only one password which matches the entered password, performs the printing job in accordance with the print request specified by the job code which is determined by the password and, when there are a plurality of the passwords which match the entered password, compares the request source identification data corresponding to the respective passwords and, when the request source identification data corresponding to the respective passwords are different from each other, requests entry of the request source identification data and, when the request source identification data is entered, performs the printing job in accordance with the print request specified by the job code determined by the entered password and the request source identification data.
Owner:MURATA MASCH LTD
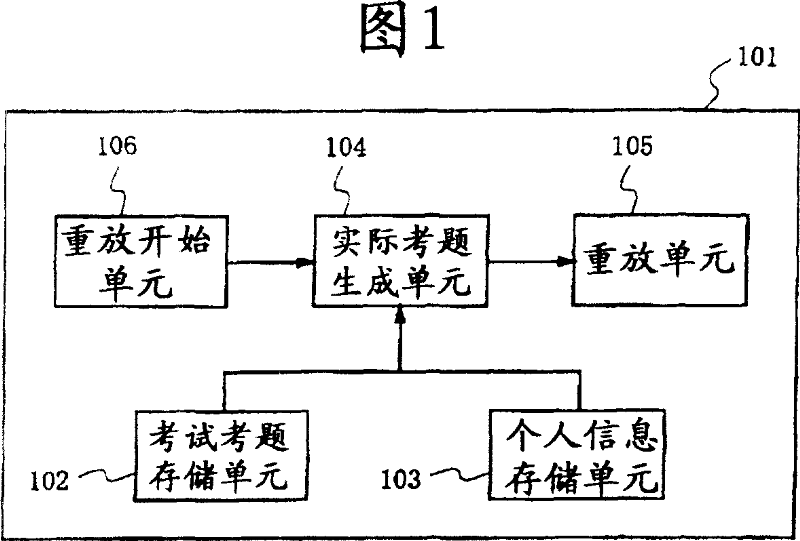
Individual test execution device
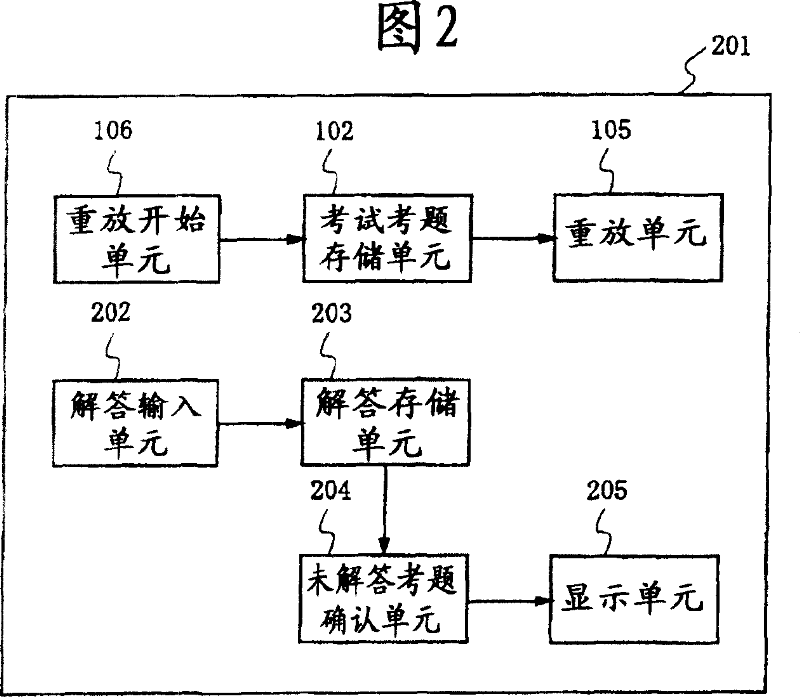
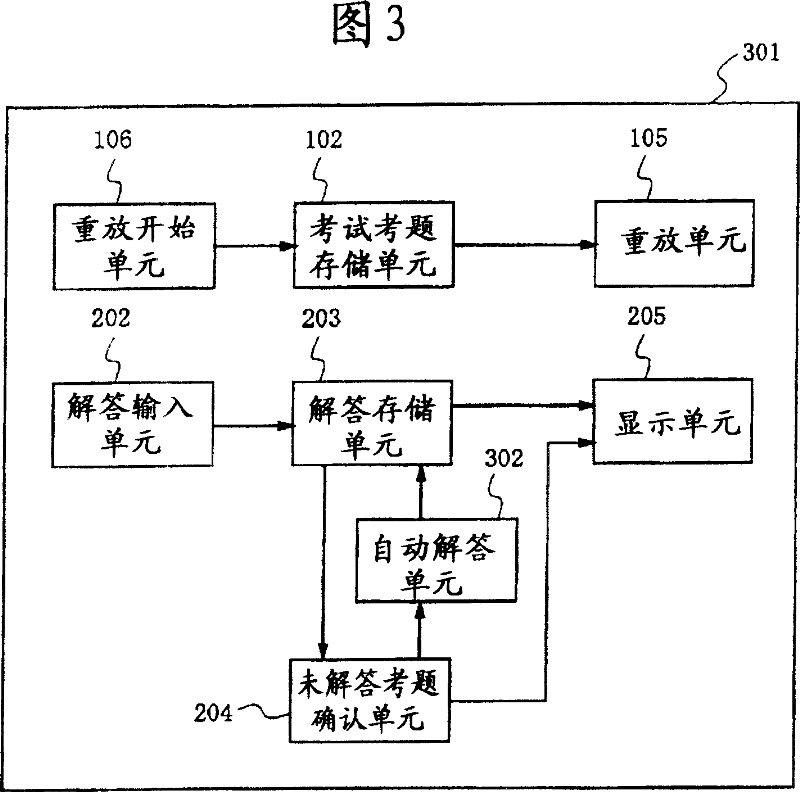
InactiveCN101044534AFree allocation of answer speedShorten the timeElectrical appliancesTest takerTest execution
In an listening test using an individual test execution device, it is possible to prevent an unfair act such as stealing a look at an answer of another test-taker. The individual test execution device (101) reads out test problem data and individual information from test problem storage means (102) containing test problems and individual information storage means (103) containing individual information. Reproduction means (105) reproduces an actual problem selected / generated according to the individual information and read out by actual problem generation means (104). Thus, it is possible to prevent an unfair act of each test-taker.
Owner:SOCIONEXT INC
Method for remote controller to obtain control authority of controller and remote controller
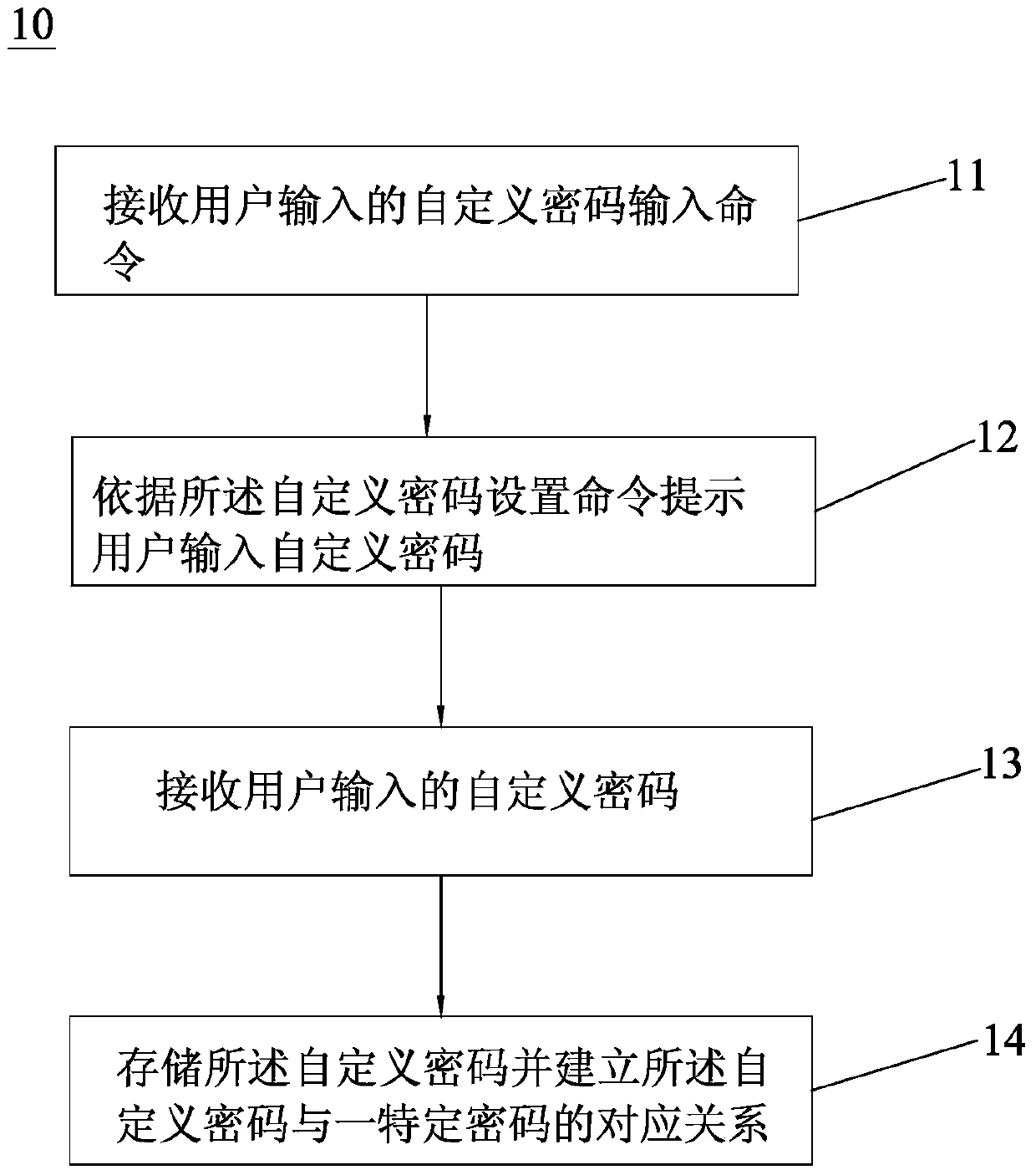
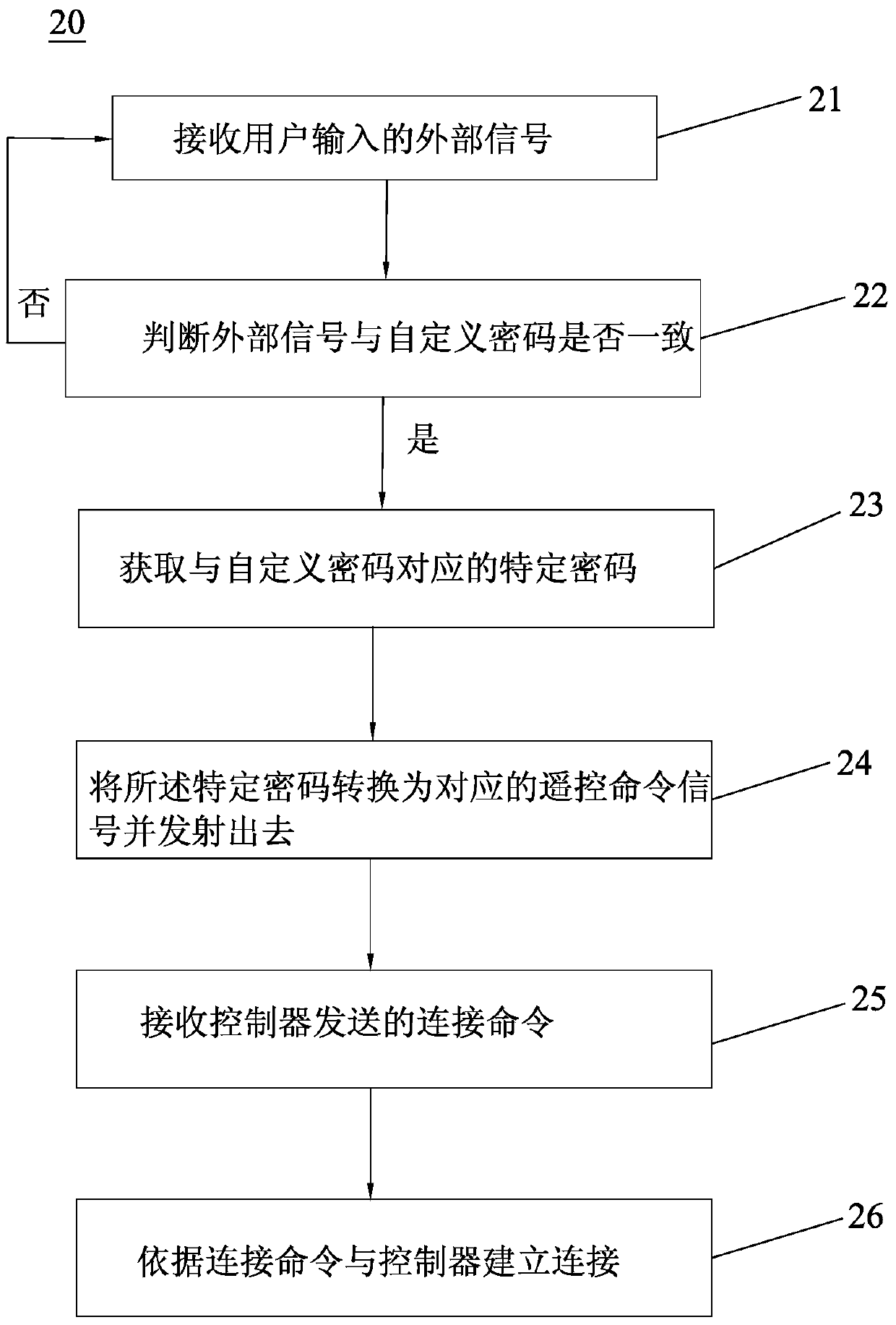
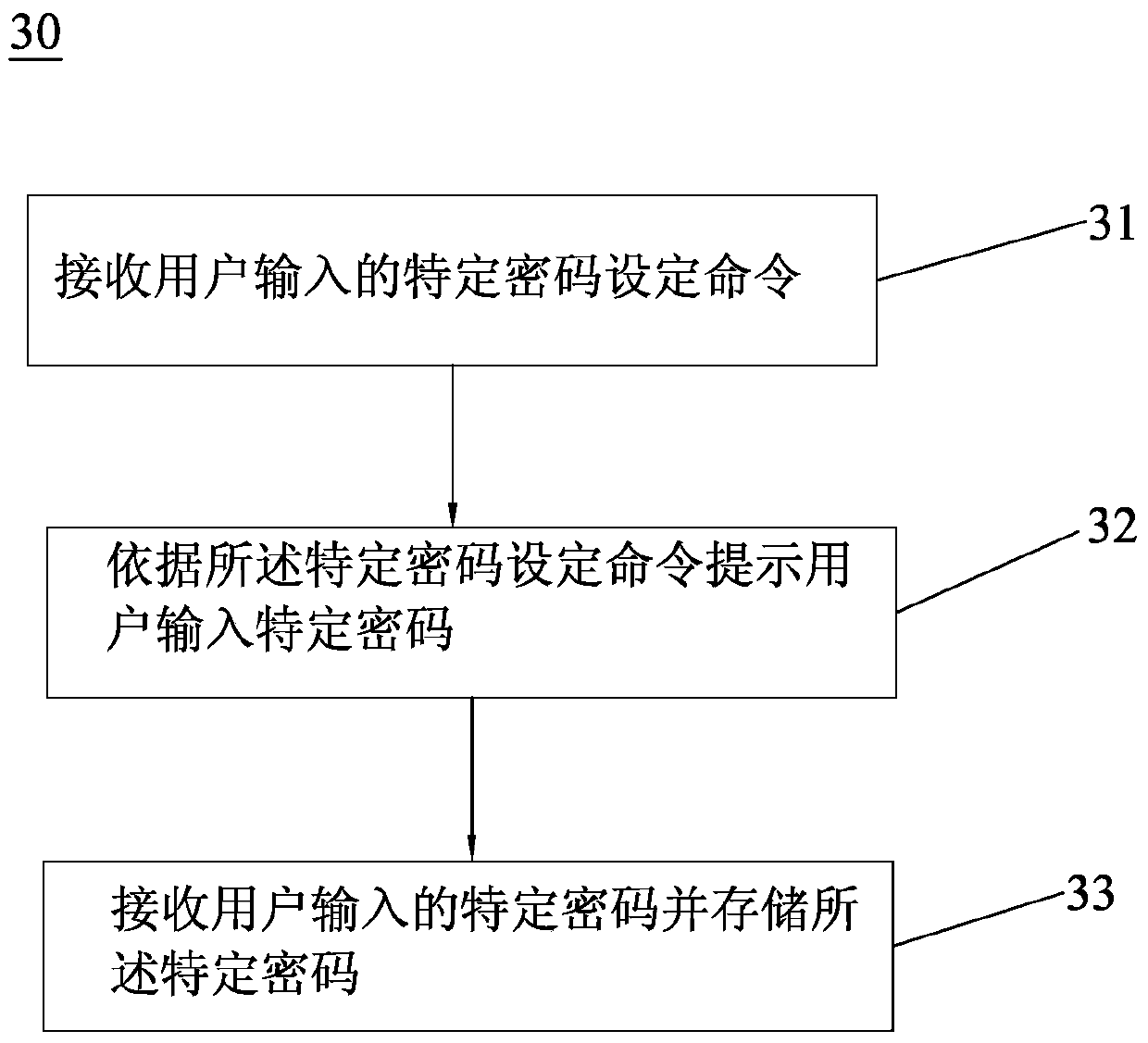
InactiveCN105279926BPrevent knowingEasy to traceTransmission systemsDigital data authenticationUser inputPassword
The invention discloses a method for acquiring controller control authority for a remote controller. The method comprises a step A for setting a customized password and a step B for acquiring the control authority. The step A comprises the following steps: (A1), receiving the customized password input by a user; (A2), storing the customized password and establishing a corresponding relation between the customized password and a specific password. The step B comprises the following steps: (B1), receiving external signals input by the user; (B2), determining whether the external signals are in accordance with the customized password, acquiring the specific password corresponding to the customized password if the external signals are in accordance with the customized password, converting the specific password into a corresponding remote control signal and emitting the remote control signal; (B3), receiving a connecting command sent by a controller, and establishing connection with the controller according to the connecting command. According to the method, the authority password of the remote controller is encrypted freely under the premise that the operation difficulty is not increased, and the use safety is improved. The invention further discloses the corresponding remote controller.
Owner:GUANGDONG XUTIAN IND INVESTMENT CO LTD
Command decoding device and method for disordered coded commands
ActiveCN101996066BImprove securityPrevent knowingConcurrent instruction executionComputer hardwareUnit of selection
Owner:北京多思技术服务有限公司
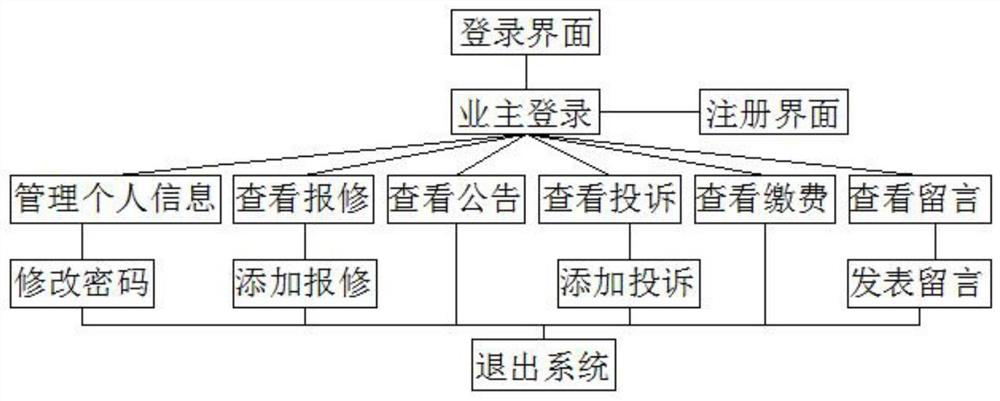
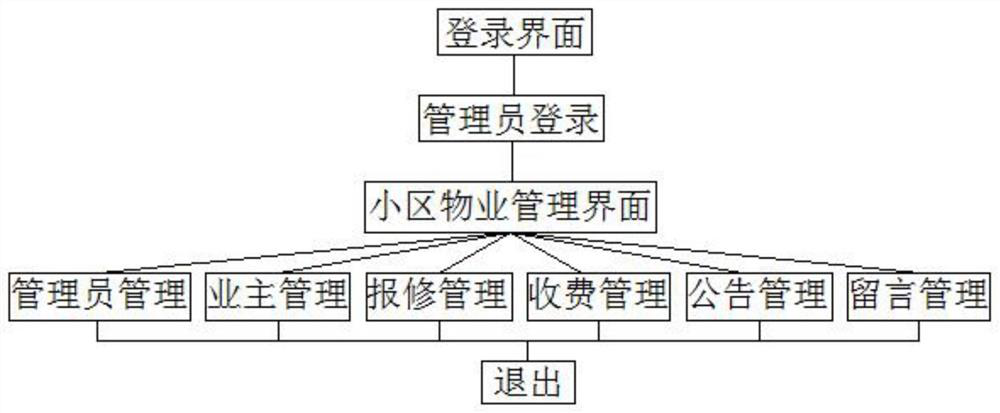
Residential district management system
The invention relates to the technical field of community management software, and in particular, relates to a residence community management system, wherein the system comprises a login interface, the login interface is connected with an owner login part and an administrator login part, the owner login part is connected with a management personal information part, a repair request check part, anannouncement check part, a complaint check part, a payment check part and a message check part, and the management personal information part is connected with a password modification part; the repairrequest check part is connected with a repair request adding part, the complaint check part is connected with a complaint adding part, the message check part is connected with a message publishing part, a password modification, the repair request adding part, the complaint adding part, a message publishing part, the announcement check part and the payment check part are all connected with an exitsystem, and the administrator login part is connected with a community property management interface. And the community property management interface is respectively connected with a administrator management part, an owner management part, a repair request management part, a charging management part, an announcement management part and a message management part. The system is simple in function module, contains basic business of property management, has high practicability, is simple and easy to operate, and is low in maintenance cost.
Owner:上海隽珑信息技术有限公司
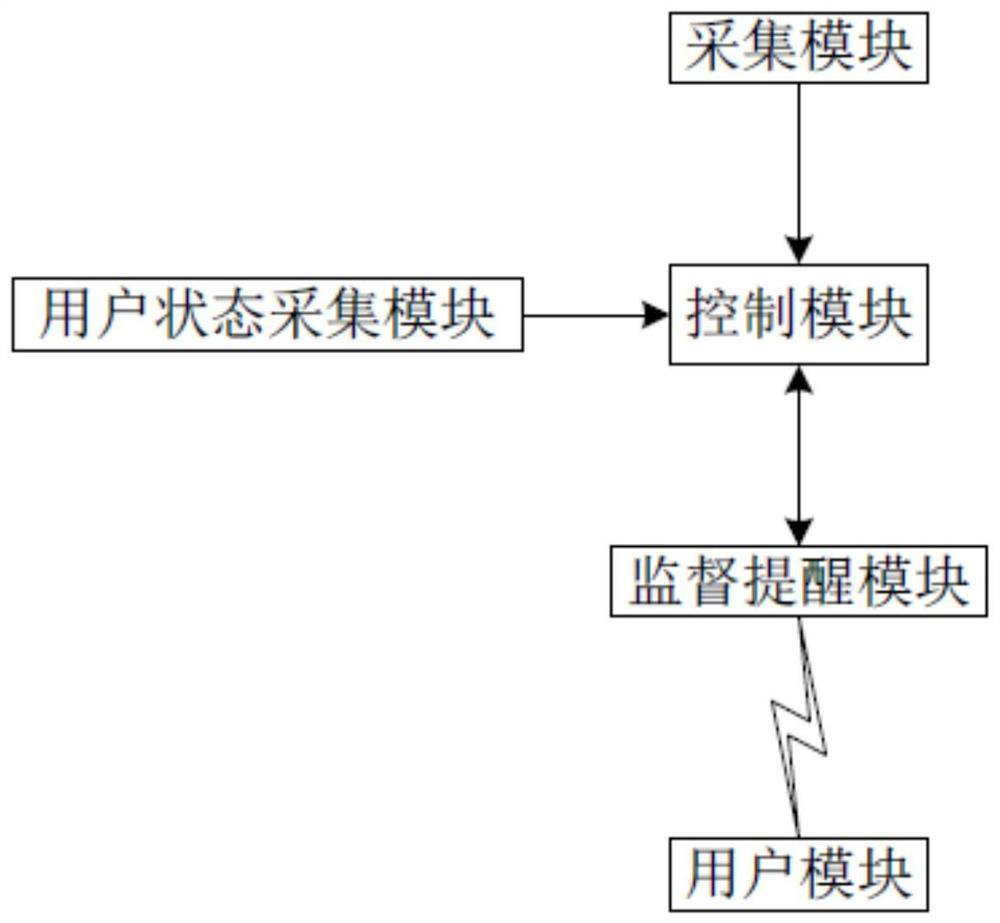
Medication supervising and reminding system and method
InactiveCN112842913AImprove acceptance rateGuaranteed Reminder StrengthOral administration deviceEngineeringHuman–computer interaction
The invention relates to the technical field of intelligent medicine boxes, in particular to a medication supervising and reminding system and method. The system comprises a supervising and reminding module which is used for acquiring a reminding signal and sending medication reminding to a user module according to a user preset rule, wherein the user preset rule comprises a preset reminding action interval and a preset reminding action difference, and the user module is used for receiving the medication reminding and displaying the medication reminding to a user. The invention aims to provide the medication supervising and reminding system with an enhanced reminding function.
Owner:重庆未来健康管理有限公司 +1
A secure image retrieval method based on secret sharing in cloud environment
ActiveCN111541679BSolve the problem of privacy protectionIncrease the difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextImage retrieval
The present invention aims to propose an image security retrieval scheme based on secret sharing in a cloud environment, and realize secure retrieval of cloud images by constructing index shares and trapdoor shares. The data owner generates a ciphertext image and an index share and uploads them to the cloud. When querying, the user generates a trapdoor share and sends it to the cloud. The cloud can calculate the distance share and return the ciphertext image closest to the query image, which can solve the existing The scheme encryption uses the security problem of the unified key; in order to prevent the attacker from inferring the image based on the original Euclidean distance analysis image similarity information, the distance share is encrypted using random numbers and secure multi-party computing methods. The security of this scheme relies on the secret sharing technology, which overcomes the common precision loss problem in image security retrieval, and the retrieval precision is almost the same as that of plaintext domain image retrieval.
Owner:WUHAN UNIV
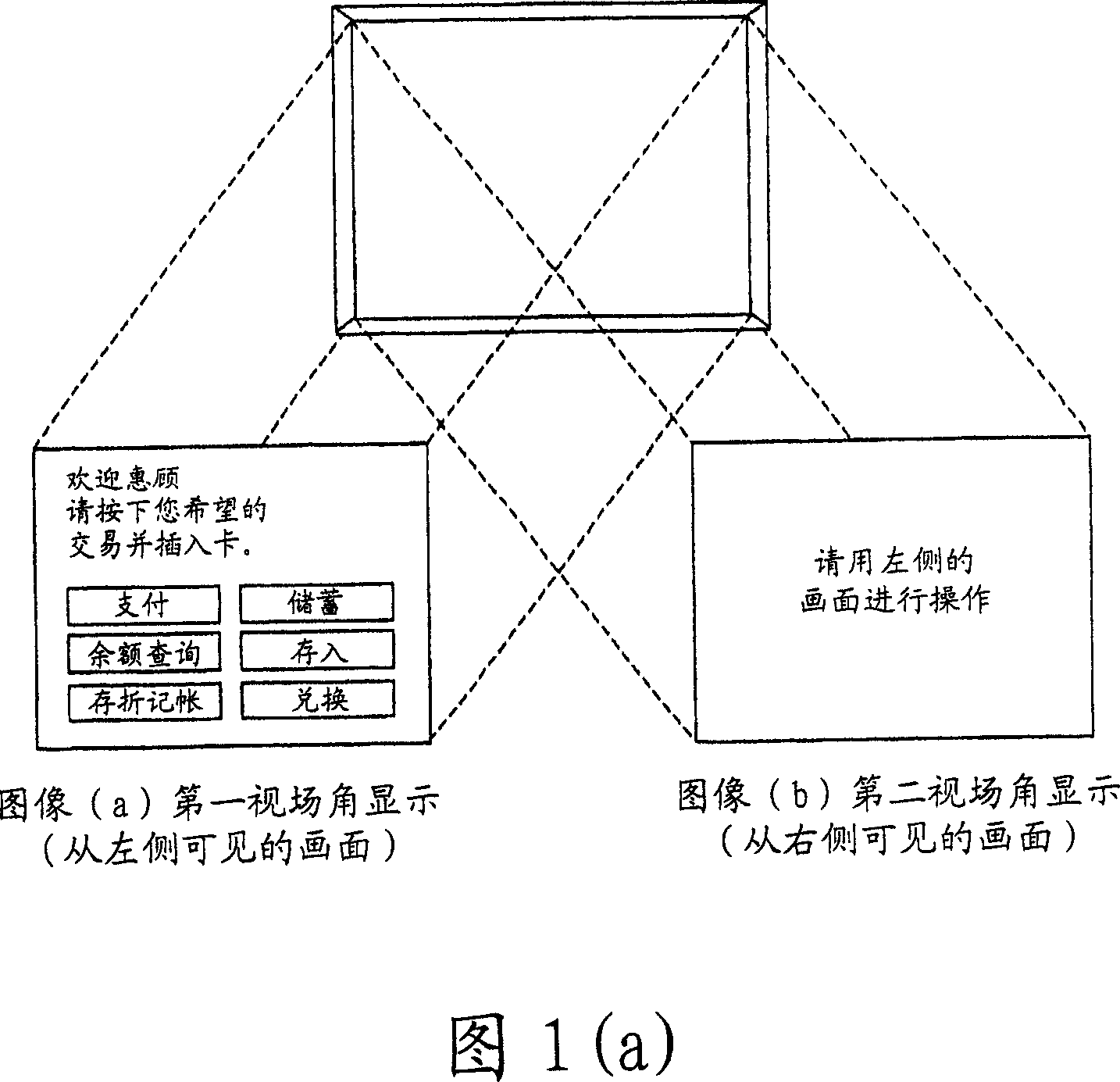
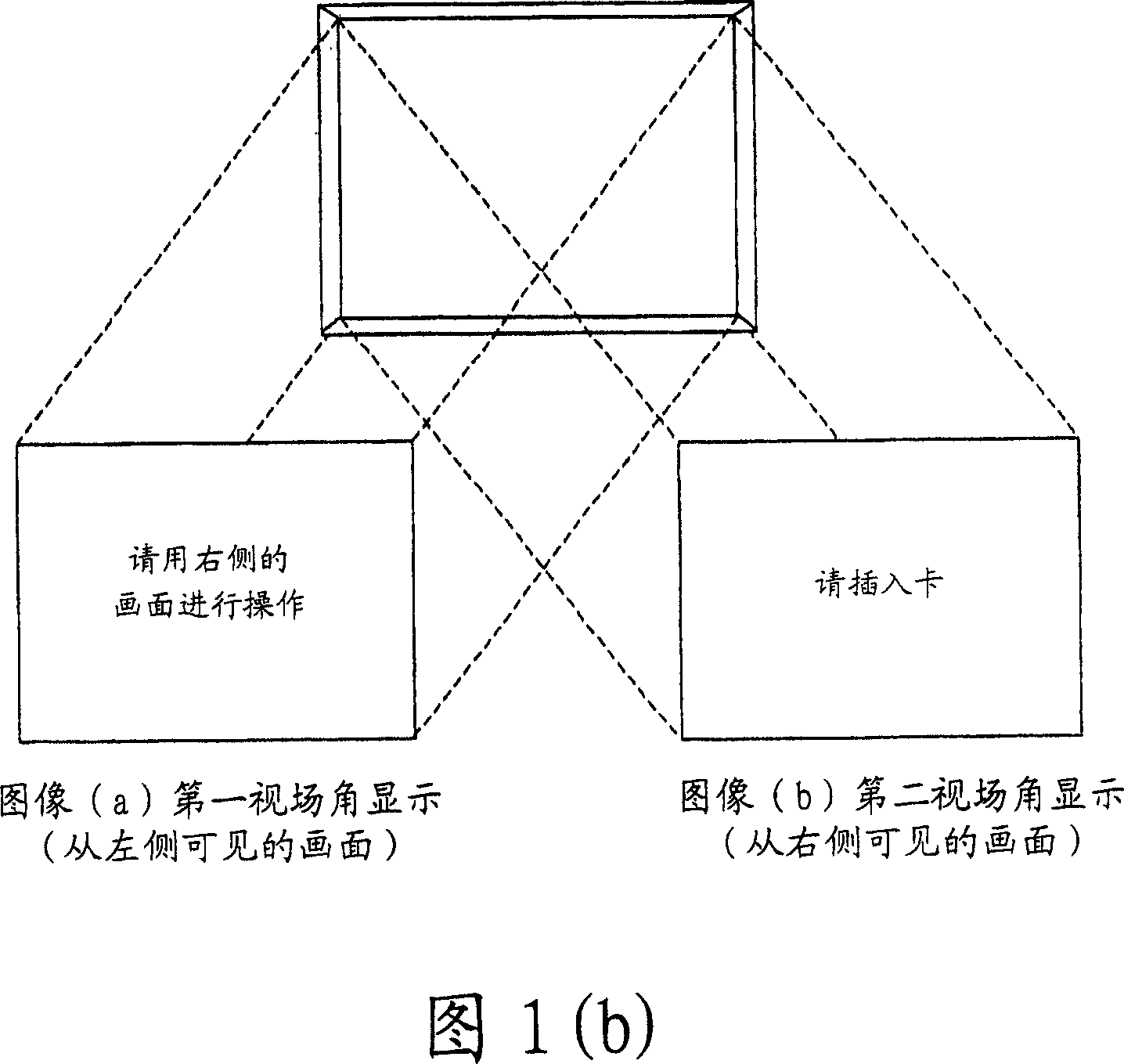
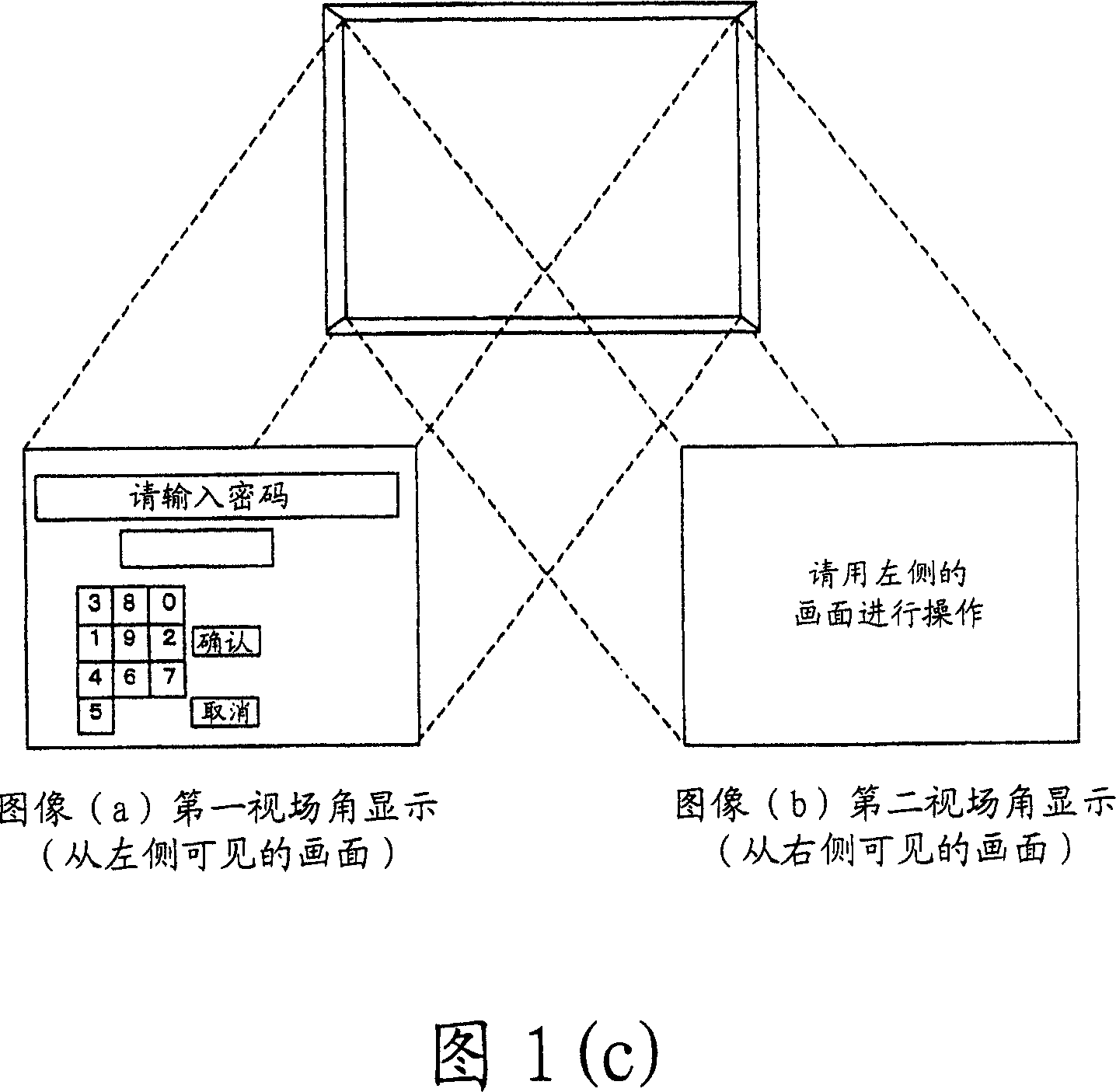
Automatic transaction device
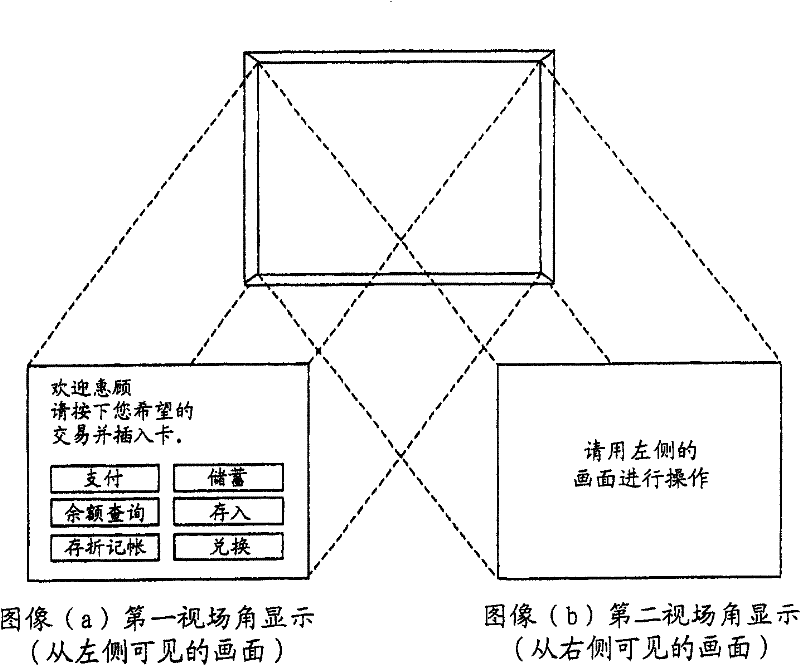
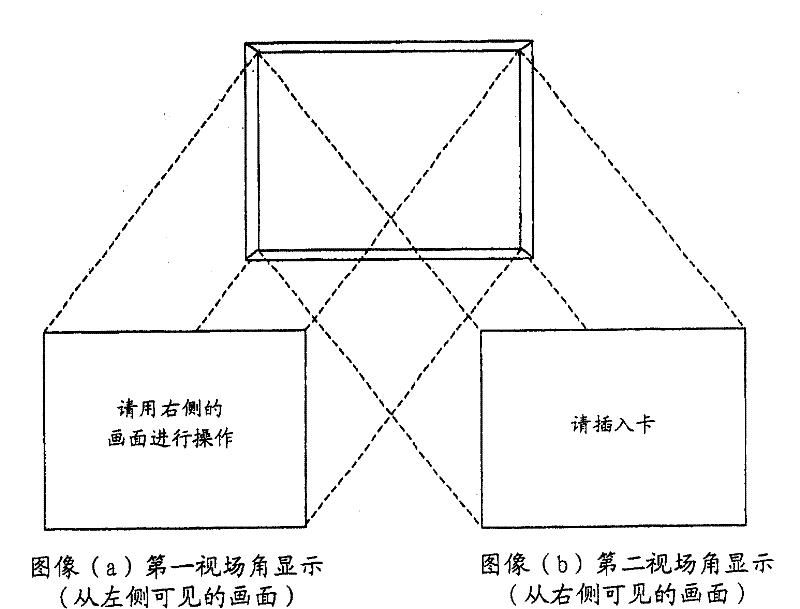
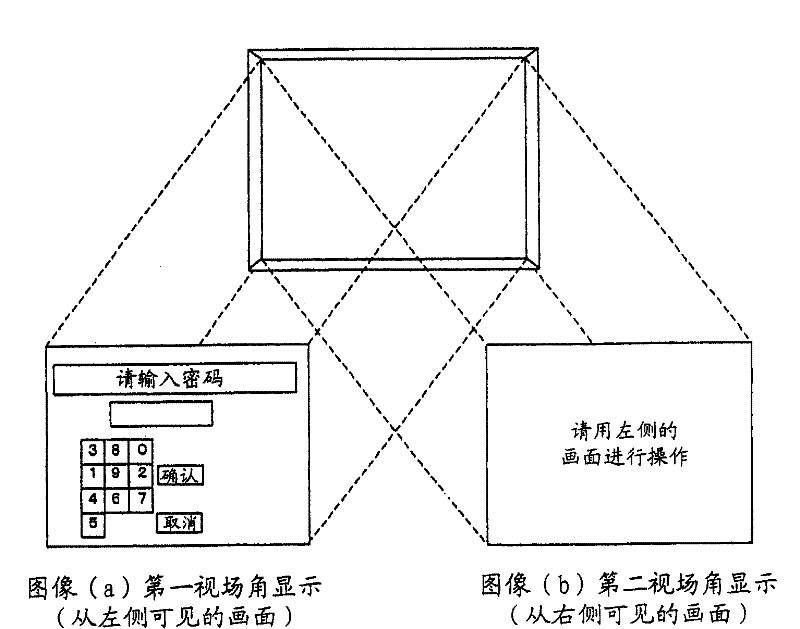
InactiveCN101000704APrevent knowingPrevent knowing the passwordInput/output for user-computer interactionComplete banking machinesField of viewVisual perception
The objective of the invention is provided with an automatic transaction device, which will not reveal the accounting number and the code even if the other person can observe the action of the client or record it using a camera, the card of the client is not able to be abused. A transacted guiding image, as a solving means, is showed by arbitrarily switching the image identified by the vision from the first angle of field of view and the image identified by the vision from the second angle of field of view in the automatic transaction device, or is showed by dividing a guiding image into a image of each direction in the first field of view and a a image of each direction in the second field of view.
Owner:DIGITAL CHINA JINXIN TECH
Electronic entrance guide system for residential areas
The invention provides an entrance guide system for residential areas. The system comprises a control unit, a calling unit and a plurality of answering units, wherein the calling unit is used for inputting calling information; the control unit is used for starting one of the answering units according to the calling information input by the calling unit. After the input calling signals are received by a resident information input part and the digital information input part, the control unit is used for comparing the received input calling signals with a plurality of pieces of predetermined calling information. If the received input calling signals are consistent with one of the predetermined calling information, one answering unit corresponding to one piece of predetermined calling information consistent with the received input calling signals is opened; if the received input calling signals are not consistent with any one of the predetermined calling information in the plurality of pieces of the predetermined calling information, any answering unit is not opened by the control unit.
Owner:杨伟
A secure storage device, system and method
ActiveCN107967432BImplement hardware encryption protectionImprove reliabilityInternal/peripheral component protectionDigital data authenticationEngineeringSafe storage
The invention provides a safe storage device, system and method. The device comprises a main control unit, a storage unit and an encryption unit, wherein the main control unit is used for generating acontrol instruction according to a terminal request and sending the control instruction to the storage unit; the storage unit is used for determining first secret key information, corresponding to the control instruction, of a user according to the logic address of the received control instruction and sending the first secret key information to the encryption unit; the encryption unit is used forreceiving the first secret key information sent by the storage unit and second secret key information sent by a terminal, and generating a data secret key according to the first secret key information and the second secret key information. The invention provides the safe storage device, system and method. By additionally arranging the encryption unit, the secret key information is stored separately, a secret key can be effectively prevented from being known by an illegal user, the safety of the secret key is guaranteed, and the data safety is ensured.
Owner:爱国者安全科技(北京)有限公司
A secure query method, device and system for high-dimensional spatial data
ActiveCN105303121BAvoid gettingPrevent knowingDigital data protectionHigh dimensionalRandom indexing
Owner:XIDIAN UNIV
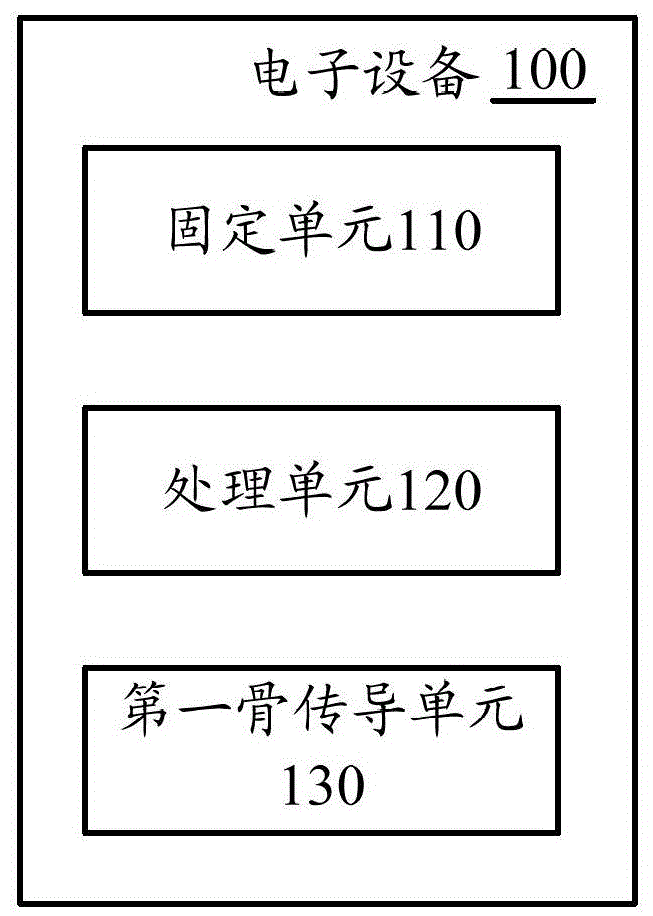
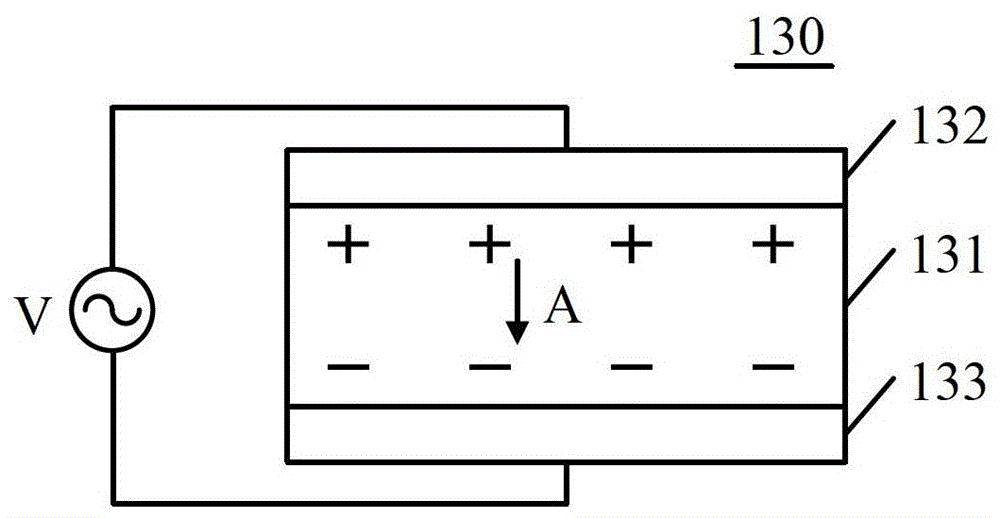
Head mounted electronic device and audio processing method
ActiveCN103852890BSmall footprintImprove output qualityInput/output for user-computer interactionTransmissionBone conduction hearingComputer science
Embodiments of the present invention provide a head-mounted electronic device and an audio processing method. A head-mounted electronic device according to an embodiment of the present invention includes: a fixing unit through which the head-mounted electronic device can be worn on a user's head; a processing unit disposed in the fixing unit and configured to perform audio processing and Output the first audio signal; the first bone conduction unit is disposed inside the fixed unit and is configured to generate vibration according to the first audio signal so that the user listens to the first audio through the generated vibration, wherein the inside of the fixed unit is used when the headset is worn When the head-mounted electronic device is worn on the user's head, the fixing unit is close to a side of the user's head, and when the head-mounted electronic device is worn on the user's head, the first bone conduction unit contacts the user's head , enabling the user to sense the vibration generated by the first bone conduction unit.
Owner:LENOVO (BEIJING) LTD
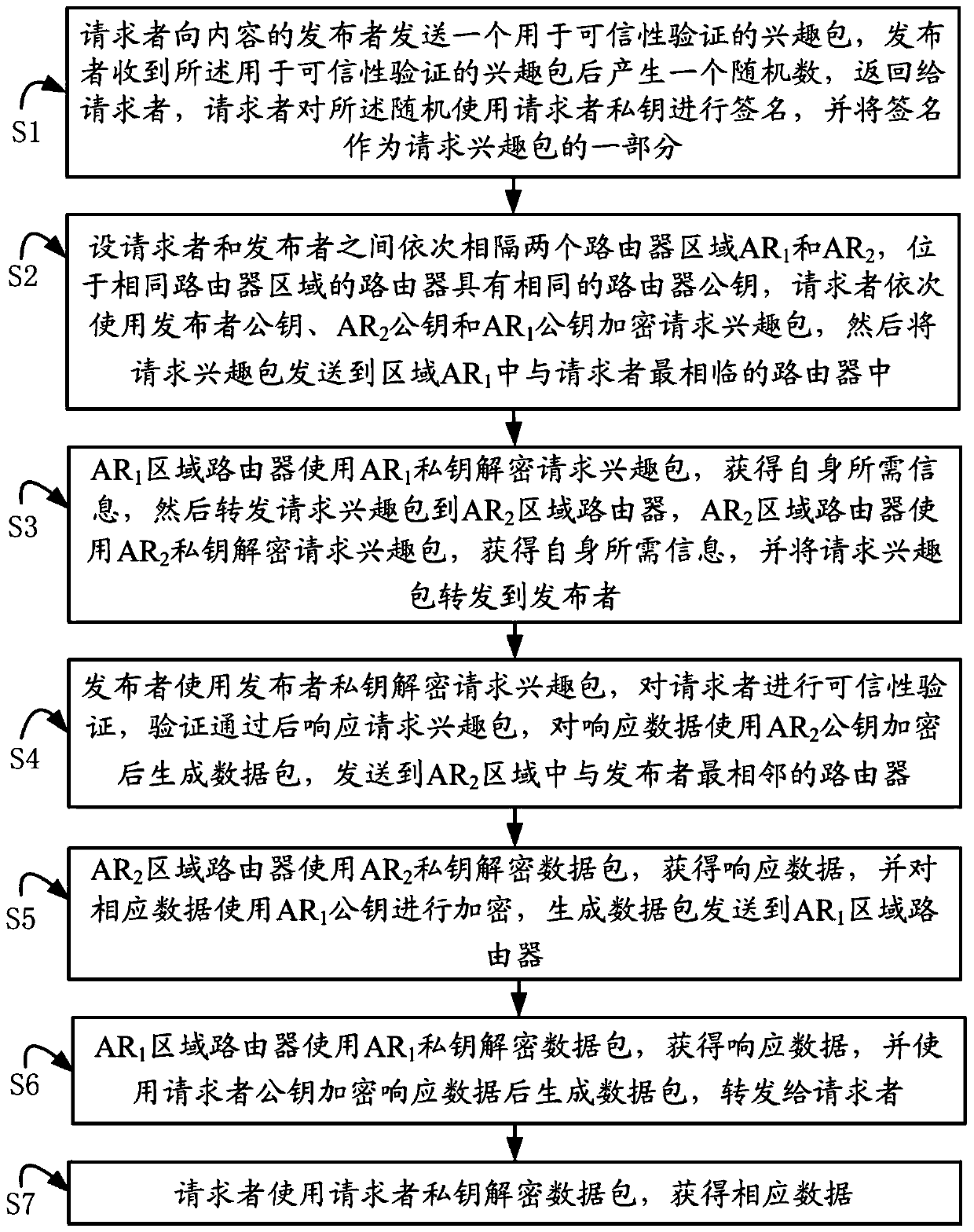
Multi-layer encryption privacy protection method for content-centric network
InactiveCN106254069BPrivacy protectionResistance to snoopingKey distribution for secure communicationPublic key for secure communicationPrivacy protectionEncryption
The invention discloses a multi-layer encryption privacy protection method used for content-centric networking. The multi-layer encryption privacy protection method comprises the steps that: a requester sends an interest package used for creditability validation to a publisher of content, and the publisher responds to the requestor; the requestor sequentially uses a publisher public key and a router public key for encrypting the requested interest packet, and sends the requested interest packet to a router; the router decrypts the requested interest packet by using a private key to obtain information it needs, and then forwards the requested interest packet to the next-layer router until the requested interest packet is sent to the publisher; the publisher decrypts the requested interest packet by using a publisher private key, validates the creditability of the requester, responds to the requested interest packet when the validation passes, and sends data to the router; and the router decrypts a data packet by using a private key to obtain response data, and forwards the response data to the next-level router until the response data is forwarded to the requester. The multi-layer encryption privacy protection method adopts the public keys for encryption, is relatively high in security, and can protect the privacy of the requestor and the publisher to a greater extent.
Owner:GUANGDONG UNIV OF TECH
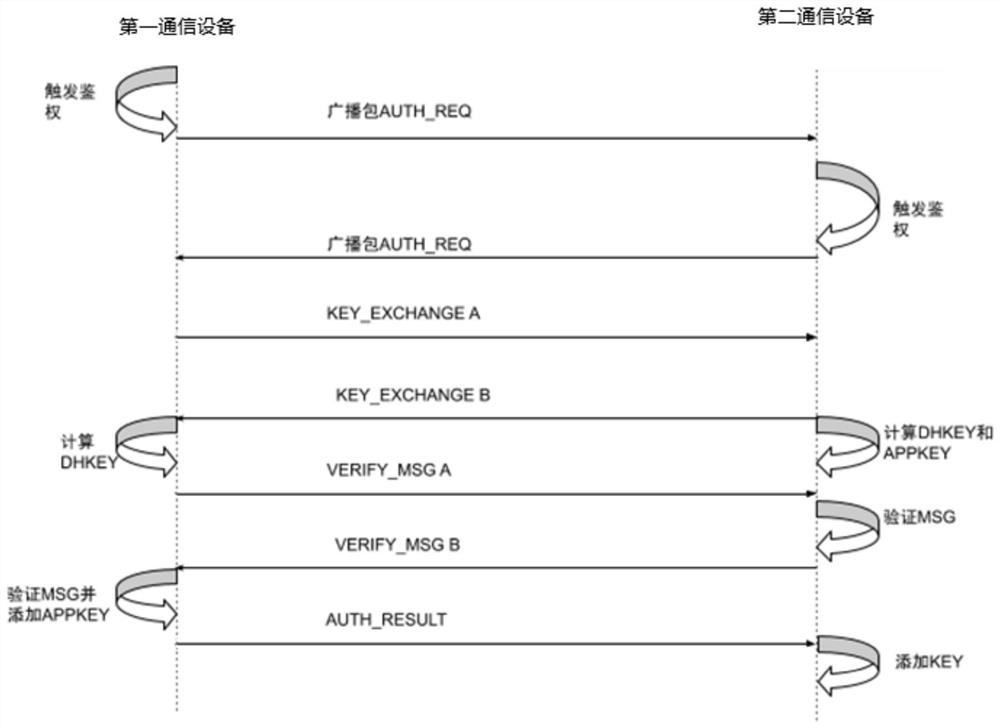
Distributed key generation and authentication method and communication device for executing method
PendingCN111787537AReduce complexityImprove the authentication success rateKey distribution for secure communicationSecurity arrangementDistributed key generationEngineering
The invention discloses a distributed key generation and authentication method of a wireless network. The method is used for generating and authenticating an application key between two communicationdevices in the same wireless network for subsequent encrypted data transmission between the two communication devices. Both communication devices have a trigger switch, and the two communication devices are triggered to generate an application key and authenticate the application key by externally operating the trigger switch. The invention also provides a communication device for performing the distributed key generation and authentication method of the wireless network. A user operates a trigger key from the outside to enable communication device to enter an authentication interaction state,and the transmitting power of broadcasting and transmitting information is additionally limited when the communication device executes the distributed key generation and authentication method of thewireless network, the invention provides a high-security-level data transmission system, and the leakage risk of data transmission in the wireless network is effectively avoided.
Owner:ESPRESSIF SYST SHANGHAI
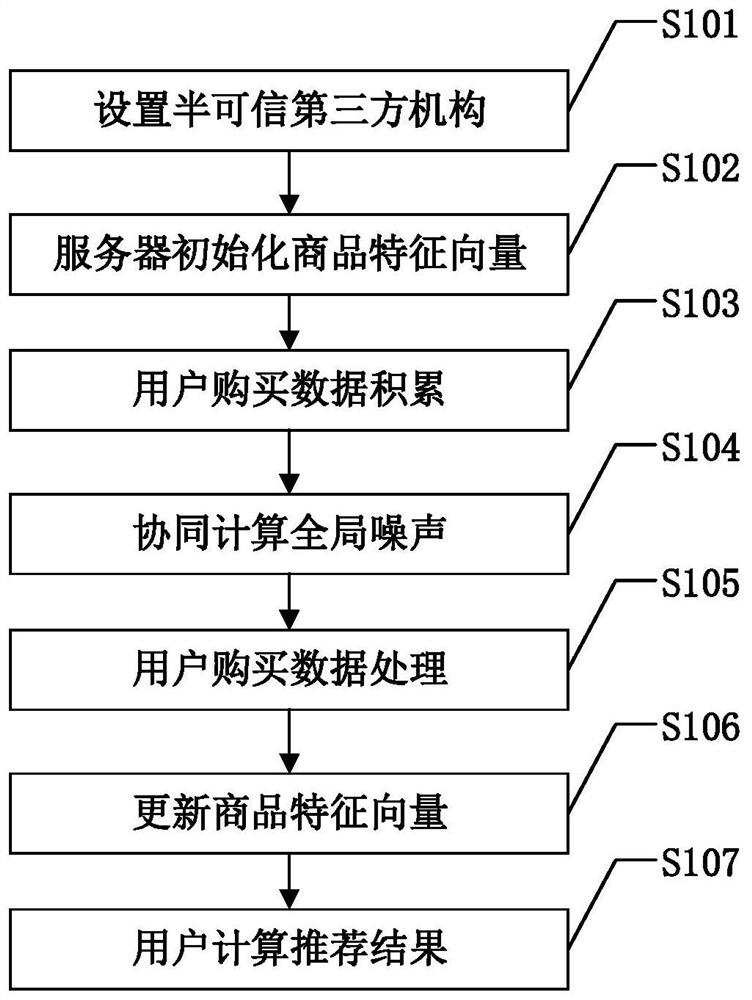
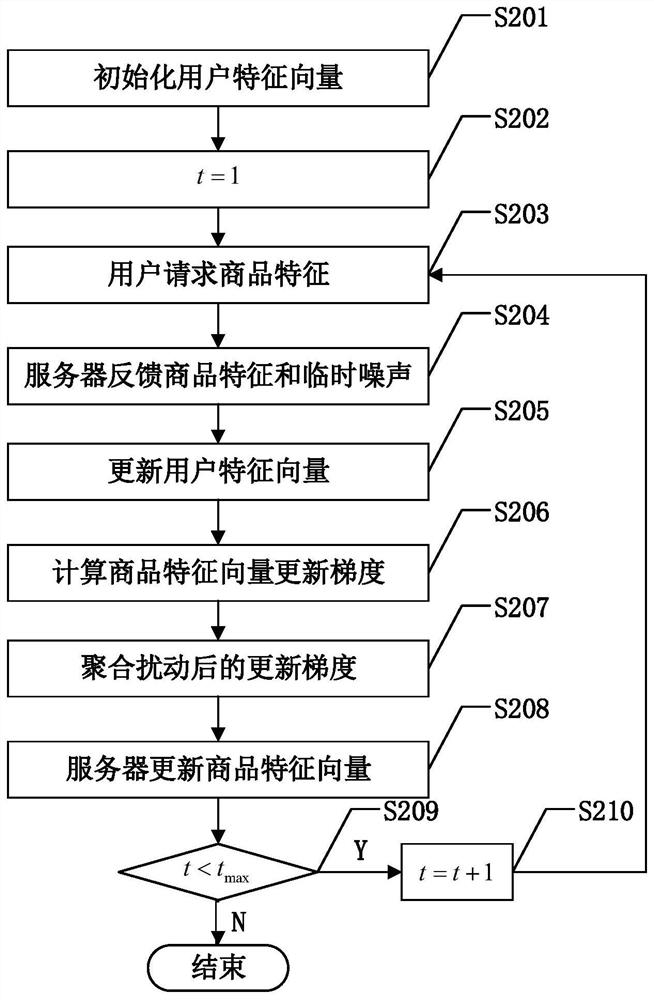
Recommendation method based on privacy protection
ActiveCN111563789BAchieve protectionProtection Preference InformationDigital data protectionBuying/selling/leasing transactionsThird partyPrivacy protection
Owner:EAST CHINA NORMAL UNIV
Display interface adjustment method and terminal
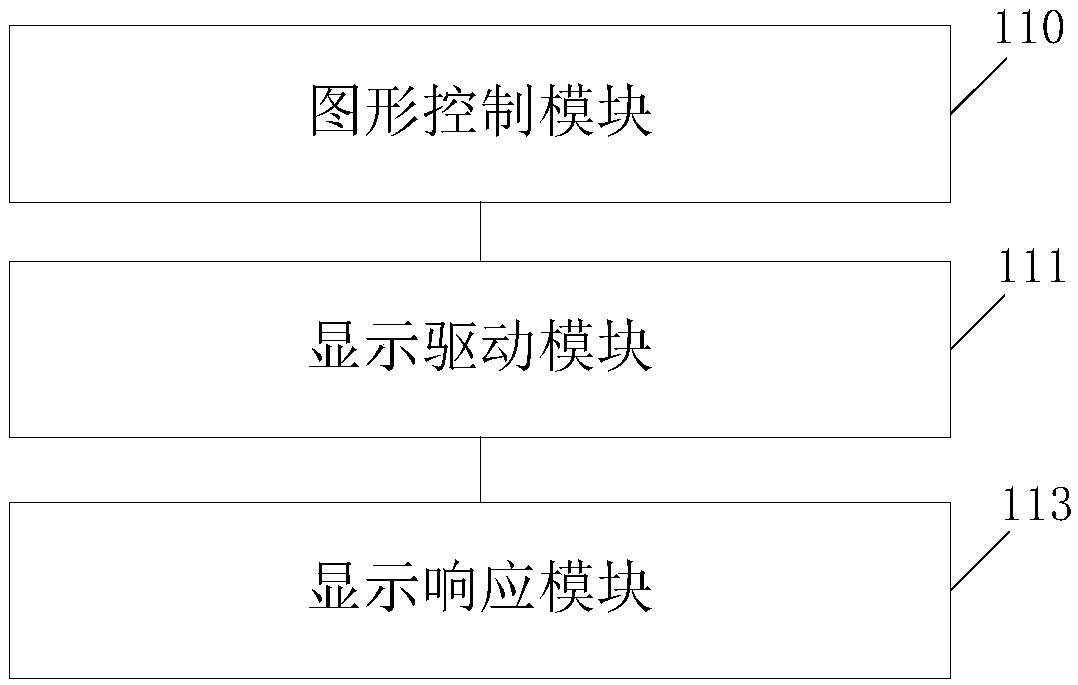
ActiveCN108073836AReduce display sharpnessPrevent knowingInternal/peripheral component protectionDigital data authenticationGraphicsDisplay response
The invention discloses a display interface adjustment method and a terminal, and aims at effectively solving the problem that terminal display interfaces cannot protect display contents on the interfaces under an open state in the prior art. The terminal comprises a graph control module, a display driving module and a display response module, wherein the graph control module is used for calling an appointed contour line to a screen display interface; the display driving module is used for adjusting at least one display parameter of an area between the contour line and a screen edge and / or anarea in the contour line according to a preset manner; and the display response module is used for displaying a graph formed by the contour line and the screen edge and / or an appointed graph on the display interface according to the adjusted display parameter.
Owner:ZTE CORP
Automatic transaction device
InactiveCN101000704BPrevent knowingPrevent knowing the passwordComplete banking machinesInput/output for user-computer interactionComputer graphics (images)Engineering
Owner:DIGITAL CHINA JINXIN TECH
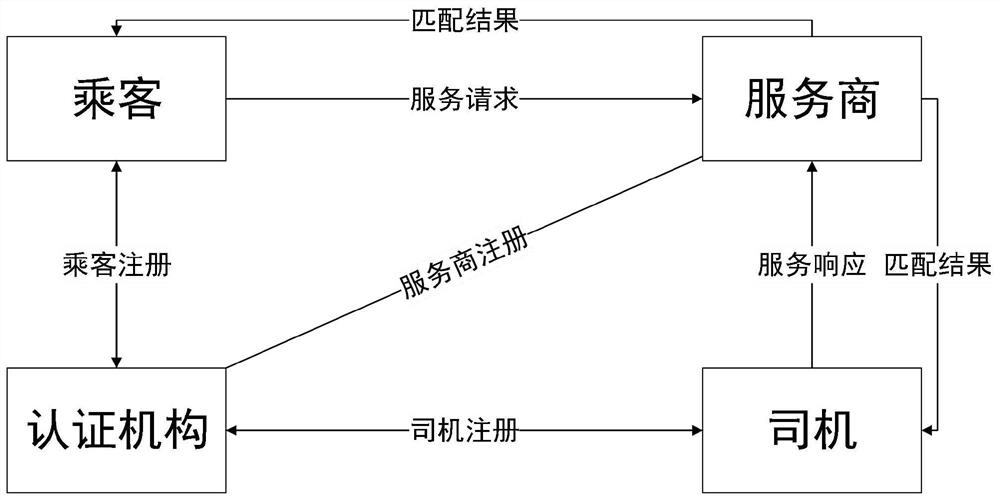
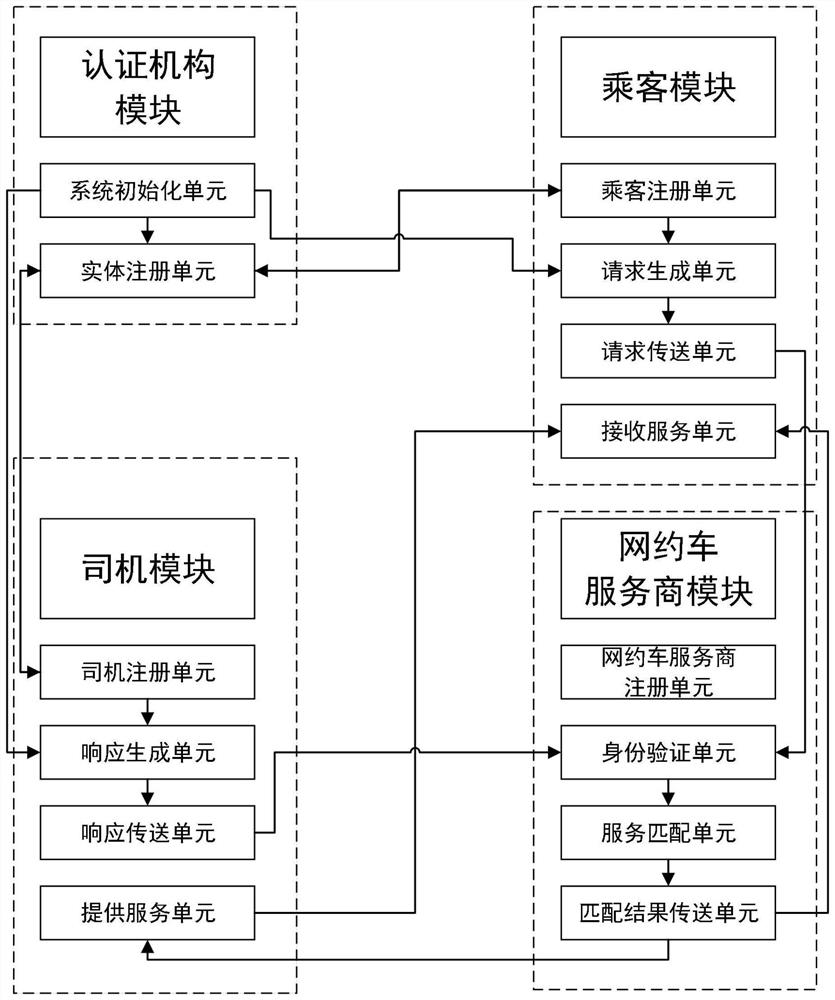
Privacy protection online car-hailing method and system for excluding matched drivers
ActiveCN113158250APrevent knowingEnsure identity anonymityDigital data protectionDigital data authenticationComputer networkPrivacy protection
The invention discloses a privacy protection online car-hailing method and a privacy protection online car-hailing system for excluding matched drivers. The privacy protection online car-hailing method and the privacy protection online car-hailing system are applied to an online car-hailing system environment consisting of a plurality of passenger modules, a plurality of driver modules, an online car-hailing service provider module and a certification authority module. The passenger module registers passenger information, generates a service request and transmits the service request to the online car-hailing service provider module; the driver module registers driver information, generates a service response and transmits the service response to the online car-hailing service provider module; the online car-hailing service provider module verifies the service request and the service response, generates a matching result and transmits the matching result to the corresponding paired passenger and driver; and the certification authority module is responsible for system initialization and entity registration. According to the invention, the privacy of passengers can be effectively protected, and the process of receiving the online car-hailing service is safe and reliable, so that the potential risk of maliciously matching the driver is effectively avoided.
Owner:HEFEI UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com