Distributed key generation and authentication method and communication device for executing method
A technology for communication equipment and key generation, applied in key distribution, which can solve the problems that ZigBee and ZigBeePro networks cannot be applied, increase the risk of key leakage, increase the amount of network data, etc., and achieve good success rate and authentication speed , save hardware cost, easy to integrate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
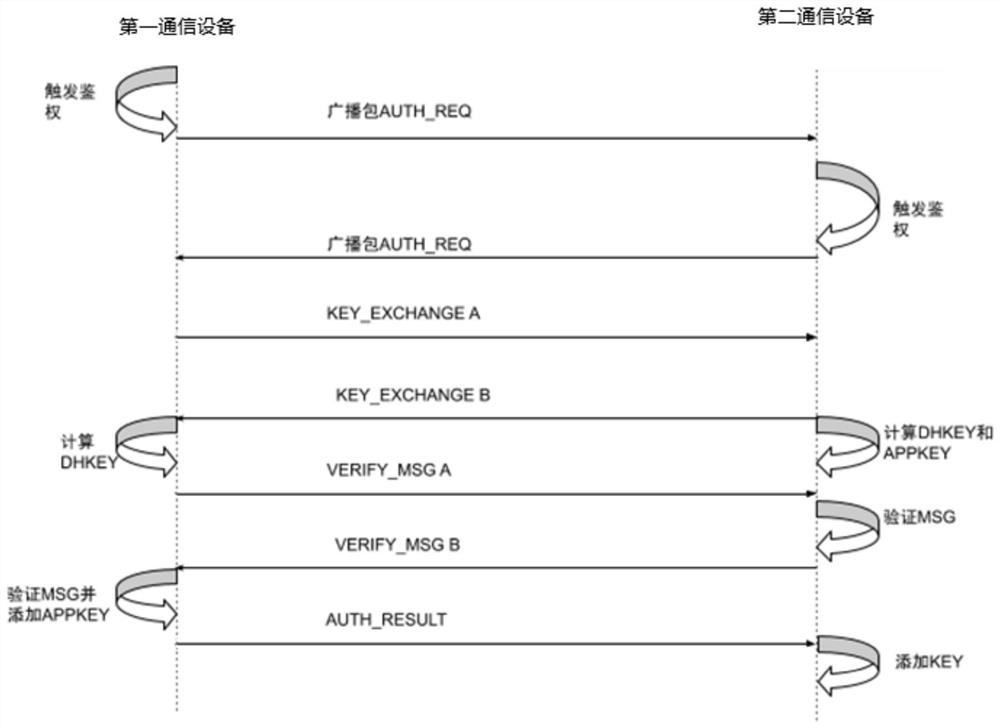
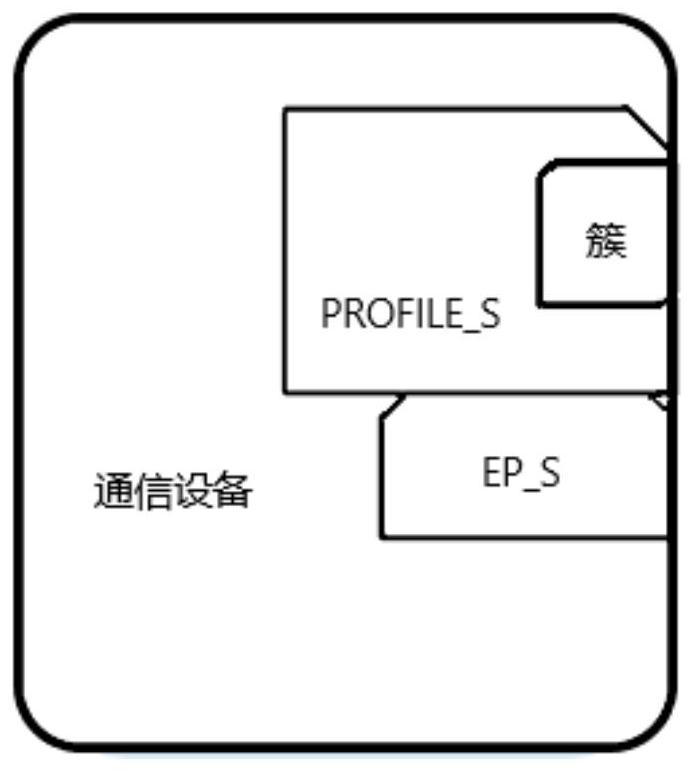
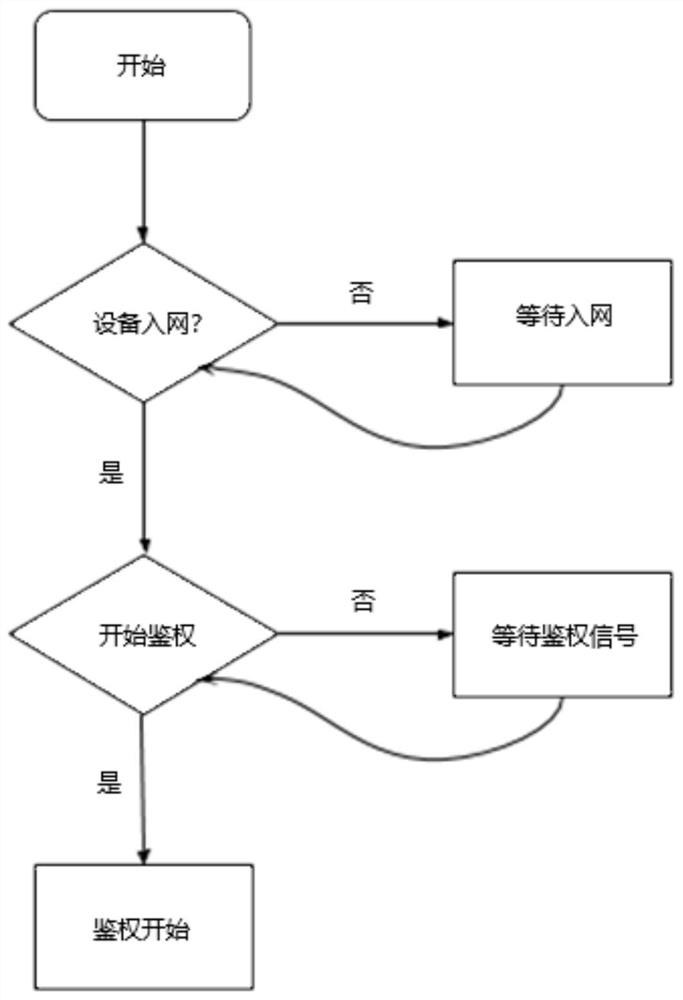
[0041] like figure 1 , 2 As shown, in a preferred embodiment of the present invention, a distributed key generation and authentication method for a wireless network of the present invention implemented in a ZigBee wireless network, and a communication method for implementing the method in a ZigBee wireless network are provided The application layer architecture of the device. based on figure 1 The illustrated method can be used in two ZigBee wireless networks such as figure 2 Application keys are generated and authenticated between the depicted communication devices (ie, the first communication device and the second communication device) for subsequent encrypted data transmission between the two communication devices. For the confidentiality of encrypted data, reference may be made to level 2 in the aforementioned levels, that is, commercial-level confidentiality.
[0042] In this embodiment, the two communication devices are, for example, an electricity meter and a meter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com