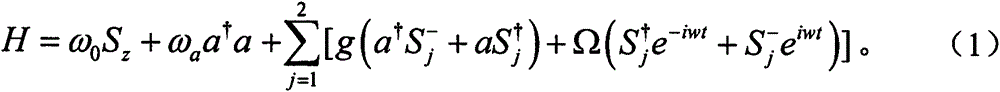Cavity QED-based quantum privacy comparison method
A quantum and privacy technology, applied in the field of quantum cryptography, to achieve the effect of high qubit efficiency, resistance to external attacks and participant attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0135] 1. Application example of quantum privacy comparison method
[0136] here to and The method of the present invention is illustrated by way of example. Without loss of generality, suppose The ith product state prepared by TP TP will Feed into the single mold cavity described above. Driven by a classical field, two atoms and Simultaneously react with this single mode cavity. TP selects the rabbi frequency and response time to satisfy Ωt=π and λt=π / 4. so, will undergo the evolution shown in equation (6). and become entangled after evolution. After they fly out of the single-mode cavity, the TP will Send to Alice(Bob). Then, Alice(Bob) uses the Z-base to measure the atom Without loss of generality, suppose The measurement result of is |e>, then according to formula (6), The measurement result of should be |g>. therefore, is 1, is 0. Alice(Bob) calculation get Then, Alice (Bob) publicly tells TP prepared according to step S2 The i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com