Multi-layer encryption privacy protection method for content-centric network
A content-centric network and multi-layer encryption technology, which is applied to the public key and key distribution of secure communication, can solve the problems of maintaining a large amount, being unable to prevent the response of illegal interest packets, and easily leaking the publisher's privacy, so as to achieve the goal of protecting privacy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, rather than all the embodiments. Based on the embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative work shall fall within the protection scope of the present invention.
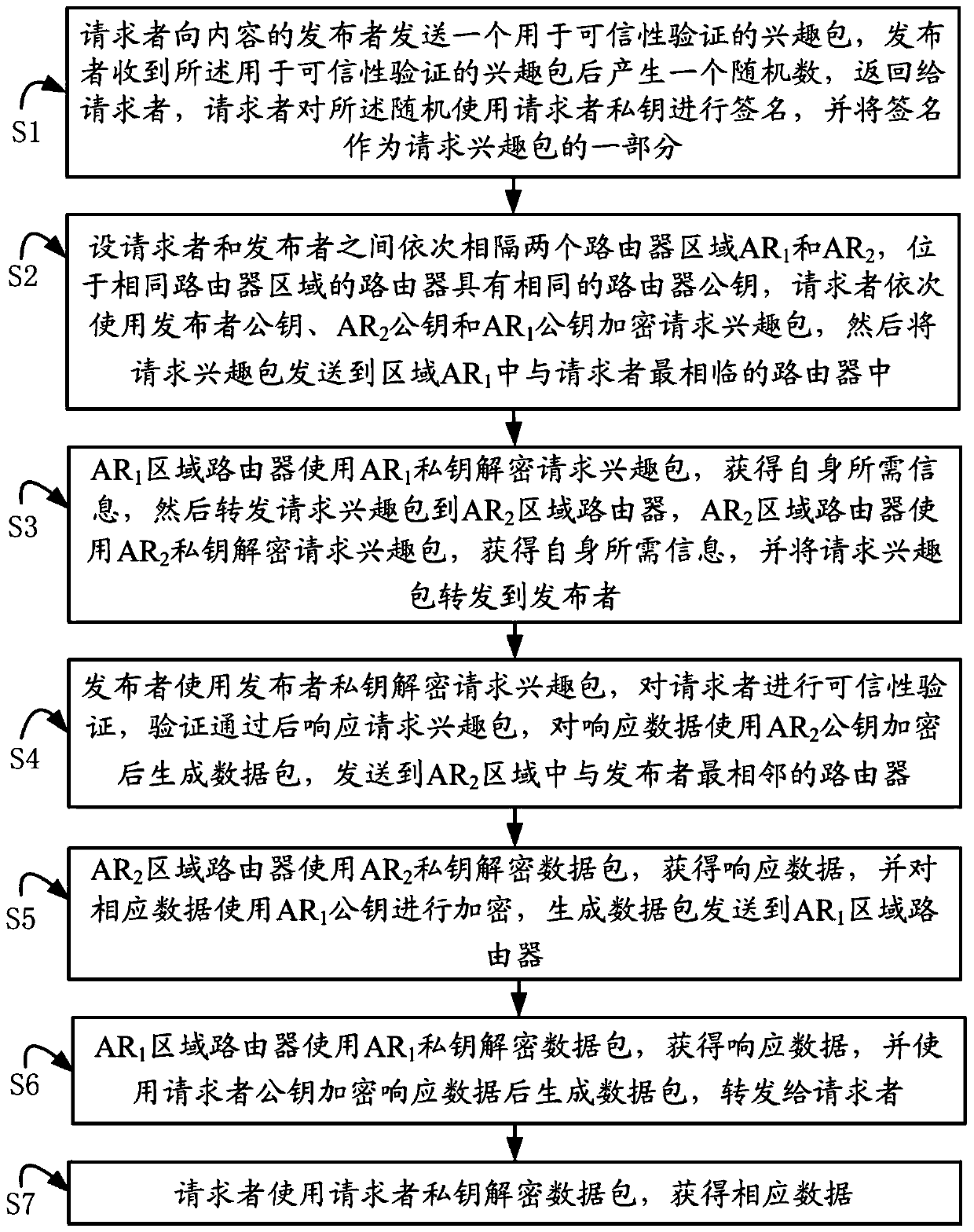
[0029] See figure 1 , First give the meaning of each symbol involved in the method described in this embodiment: the set of routers is AR set ; Router area AR 1 , AR 2 The public / private key pair is (puk1|pri1) and (puk2|pri2); the public / private key pair of the content publisher is (puk1│pri1); the public / private key pair of the requester is (puk_r|pri_r) ; Data is an encrypted data packet verifying that the requester is a trusted reque...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com