Wearable computing autonomous security authentication system and security authentication method
A security authentication and wearable device technology, applied in the field of secure communication, can solve the problems of insecure communication, lack of user anonymity and untraceability, and inability to resist theft attacks of mobile devices and wearable devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
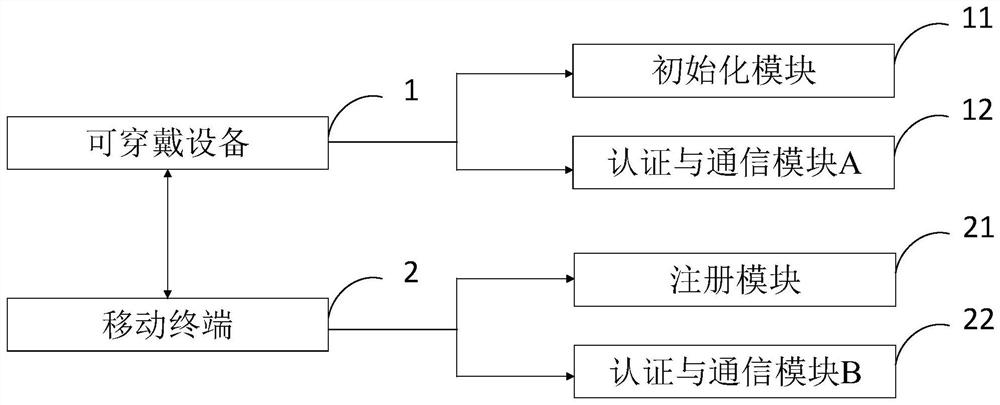
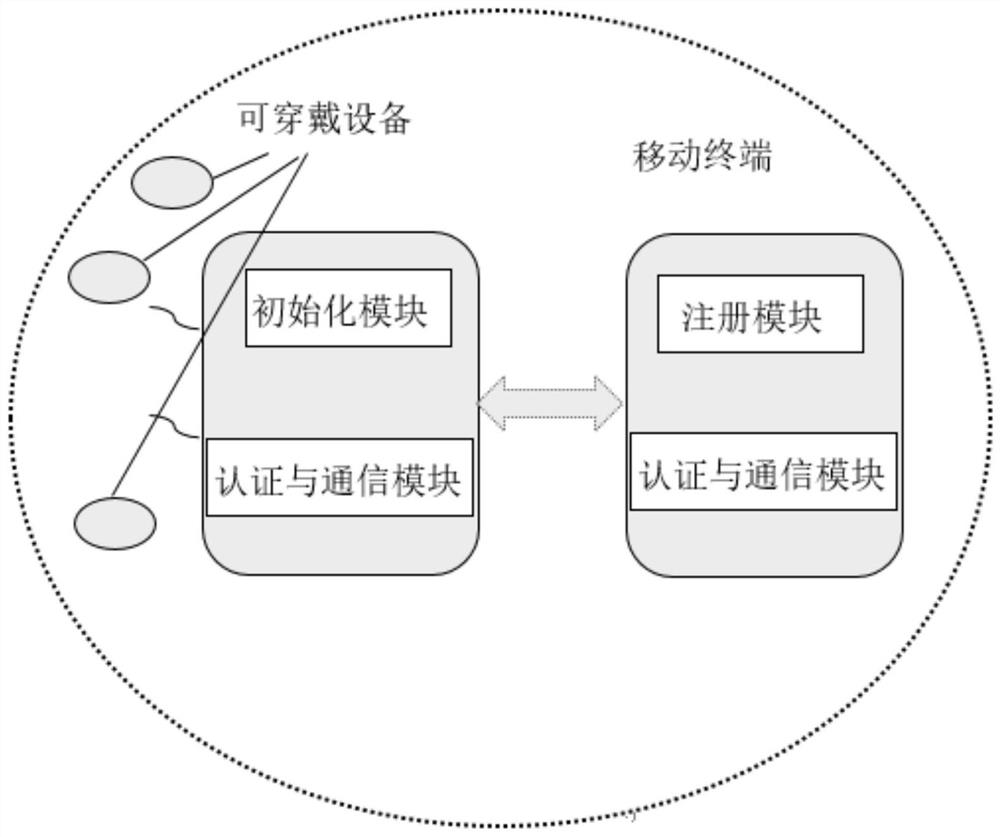
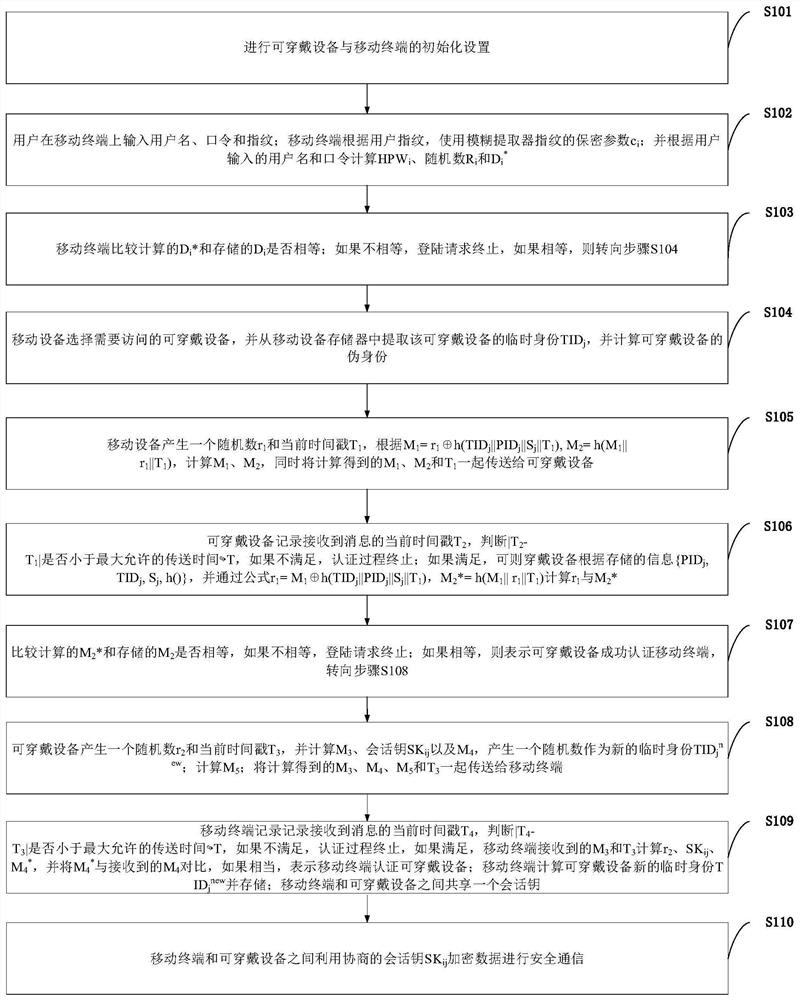
[0136] The technical scheme includes three aspects: the setup scheme of the initialization module of the wearable device, the setup scheme of the mobile terminal registration module, and the technical scheme of security authentication between the wearable device and the mobile terminal.
[0137] The initialization mode setting scheme for the wearable device includes the following steps:
[0138] (1) The user chooses a unique ID for each wearable device j and a temporary identity TID j , to generate two sufficiently long random numbers R 1 and R 2 .
[0139] (2) Calculate the pseudo-identity PID of the wearable device j =h(ID j ||R 1 ), where h(·) represents the hash function in cryptography.
[0140] (3) The user according to the current timestamp T j , to compute a secret parameter S for the wearable device j =h(ID j ||T j ||R 2 ).
[0141] (4) The user stores information in the wearable device {PID j ,TID j ,S j ,h(·)}.
[0142] The setting scheme of the mob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com