Systems and methods for data management of multiple cloud services
A technology for data management and cloud services, which is applied in the field of systems and methods for data management of multiple cloud services, and can solve problems such as difficulty for companies or end users to manage and store data consistently and accurately
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
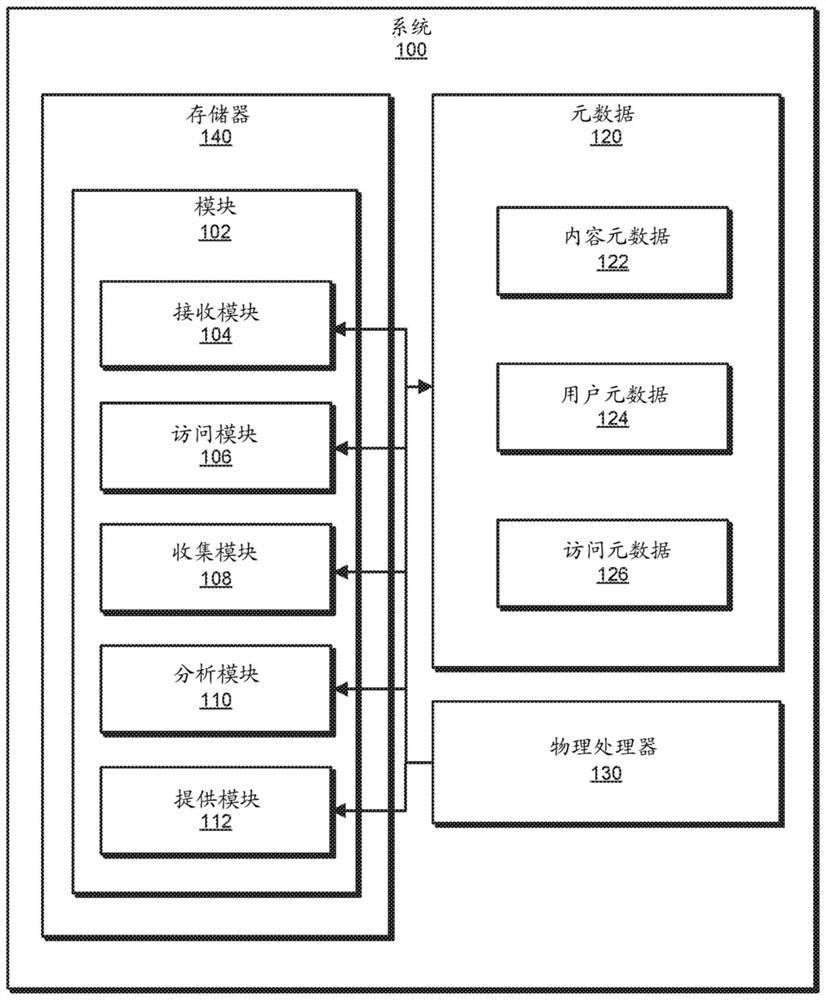
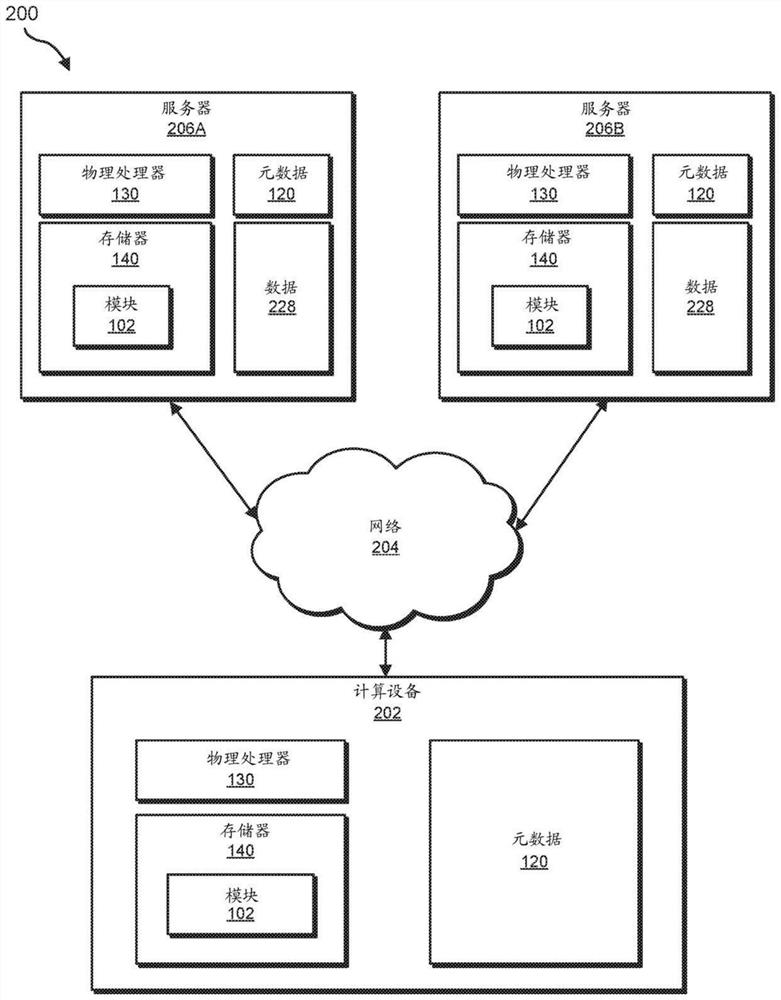
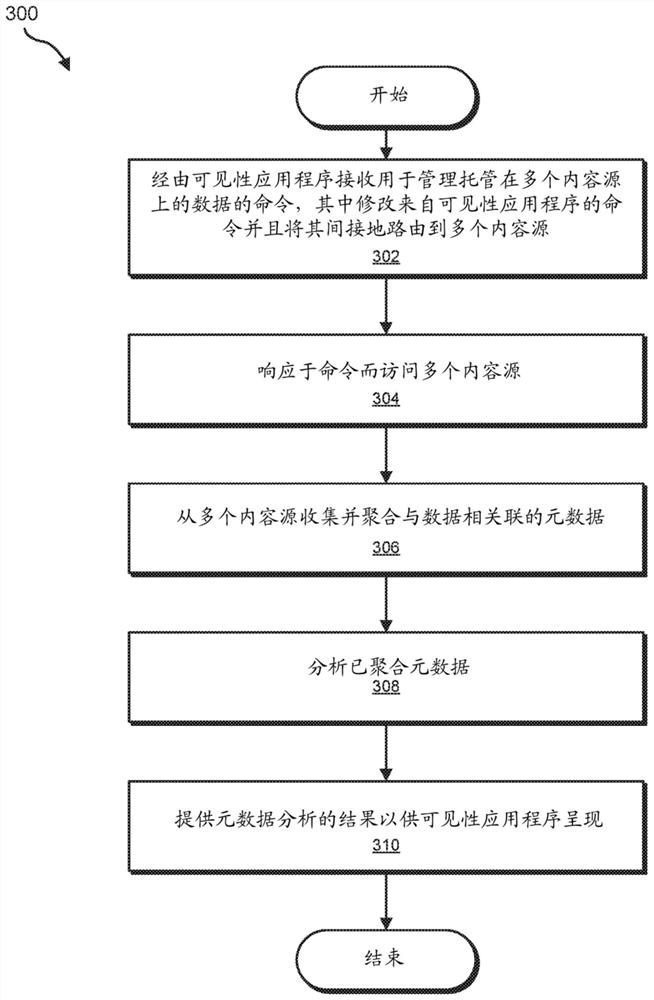
[0025] The present disclosure generally relates to systems and methods for data management of multiple cloud services. As organizations need to increase their data storage needs, they can rely on a variety of data storage solutions, including externally managed cloud-based services and / or internally managed on-premises storage solutions. Without a predefined data model and / or due to various incompatibilities between storage solutions, the volume of unstructured data can grow too unmanageable. As will be explained in more detail below, a platform for multi-cloud data management can access multiple content sources storing data and aggregate and analyze metadata associated with the data. The platform can provide an application programming interface (API) for a visibility application that can present analysis results and present a user interface for users to issue commands to the platform. Platforms can provide tools to better manage unstructured data via visibility applications....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com