Abnormal access behavior identification method and device, computer equipment and storage medium
An identification method and technology of a computer program, applied in the direction of using information identifiers to retrieve web data, special data processing applications, website content management, etc. The effect of improving intelligence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] It should be understood that the specific embodiments described here are only used to explain the present application, not to limit the present application.
[0049] It should be noted that all directional indications (such as up, down, left, right, front, back...) in the embodiments of the present application are only used to explain the relationship between the components in a certain posture (as shown in the drawings). If the specific posture changes, the relative positional relationship, movement conditions, etc., the directional indication will also change accordingly, and the connection may be a direct connection or an indirect connection.
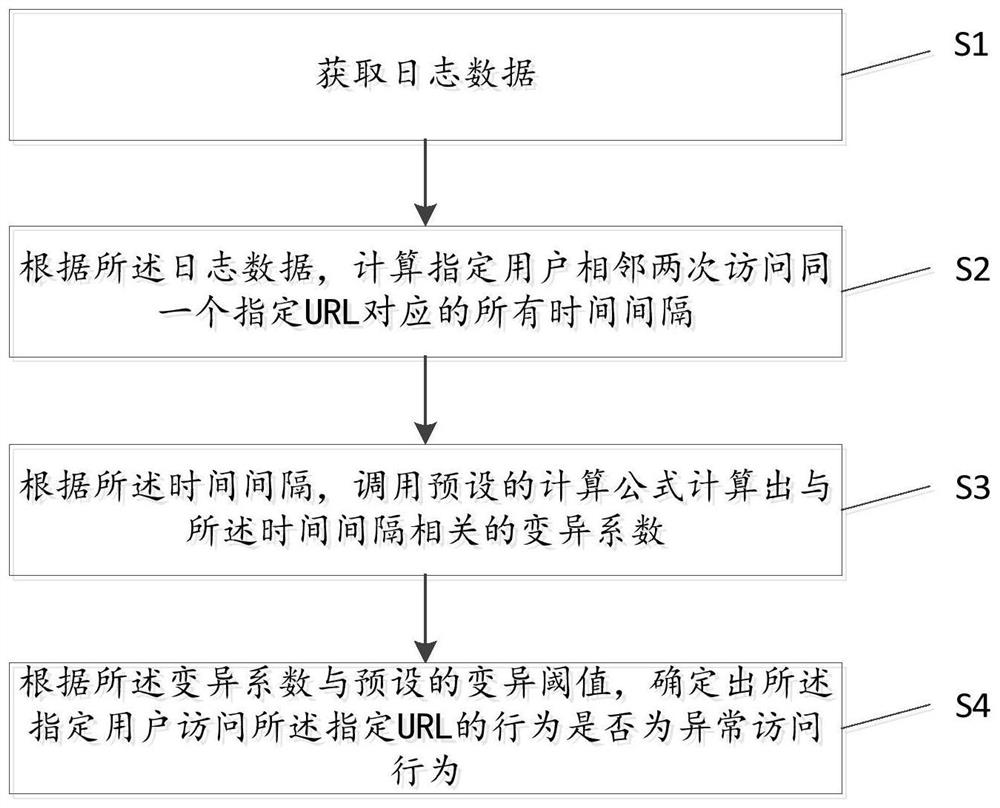
[0050] refer to figure 1 , the abnormal access behavior identification method of an embodiment of the present application, including:
[0051] S1: Obtain log data;
[0052] S2: According to the log data, calculate all the time intervals corresponding to two adjacent visits by the specified user to the same specified URL, whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com