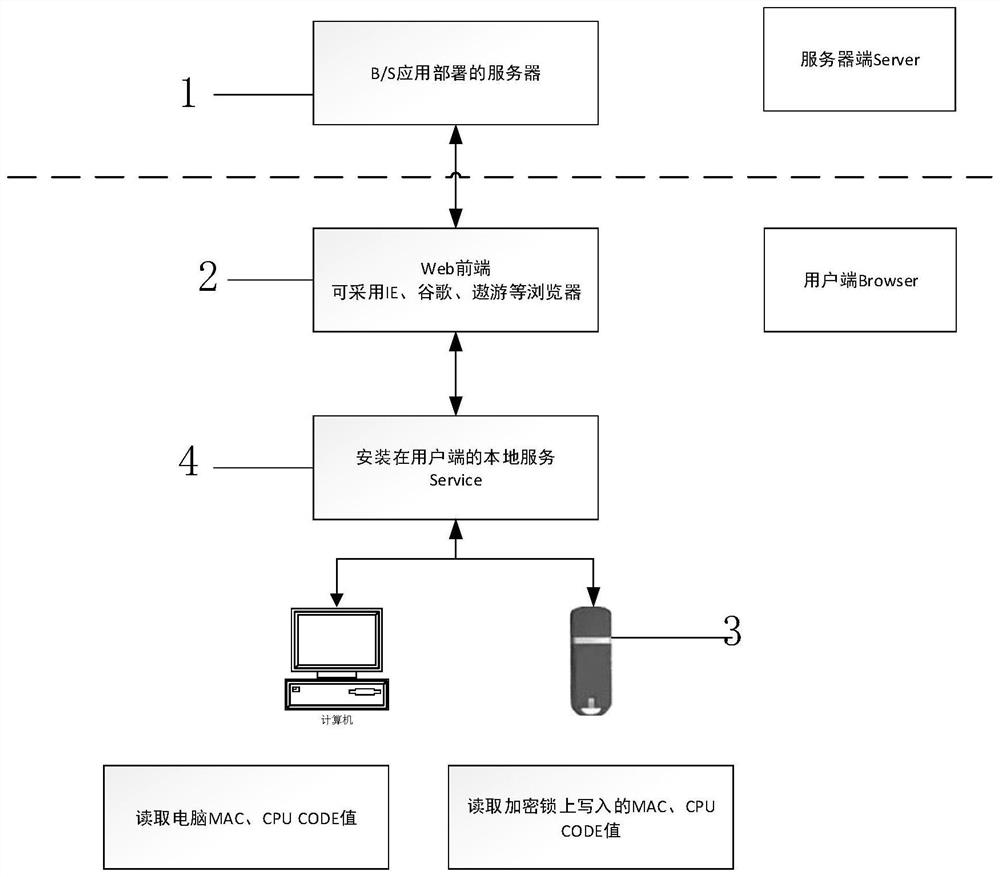
Identity verification method for BS application service binding hardware codes in offline state
An application service and authentication technology, which is applied in the authentication field of BS application service binding hardware code in offline state, which can solve the problem of restricting computers or other terminals to log in to the system, unable to meet application requirements, and limited browser read and write permissions, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
[0048] In the prior art, users can log in at any terminal with the same user name and password, and it is impossible to log in to the system with a specific computer in a specific environment. Even if the hardware code of the terminal hardware computer, such as the MAC address, is entered in the background database in advance, because the web front end does not have the authority to read the system hardware address, the user name cannot be bound to the login hardware. In the prior art, some online banking apps on the PC side are developed using a C / S structure, which requires separate installation of the program of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com