System and method for secure device connection
一种通信装置、访问装置的技术,应用在安全装置、安全通信装置、计算机安全装置等方向,能够解决维护用户隐私等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
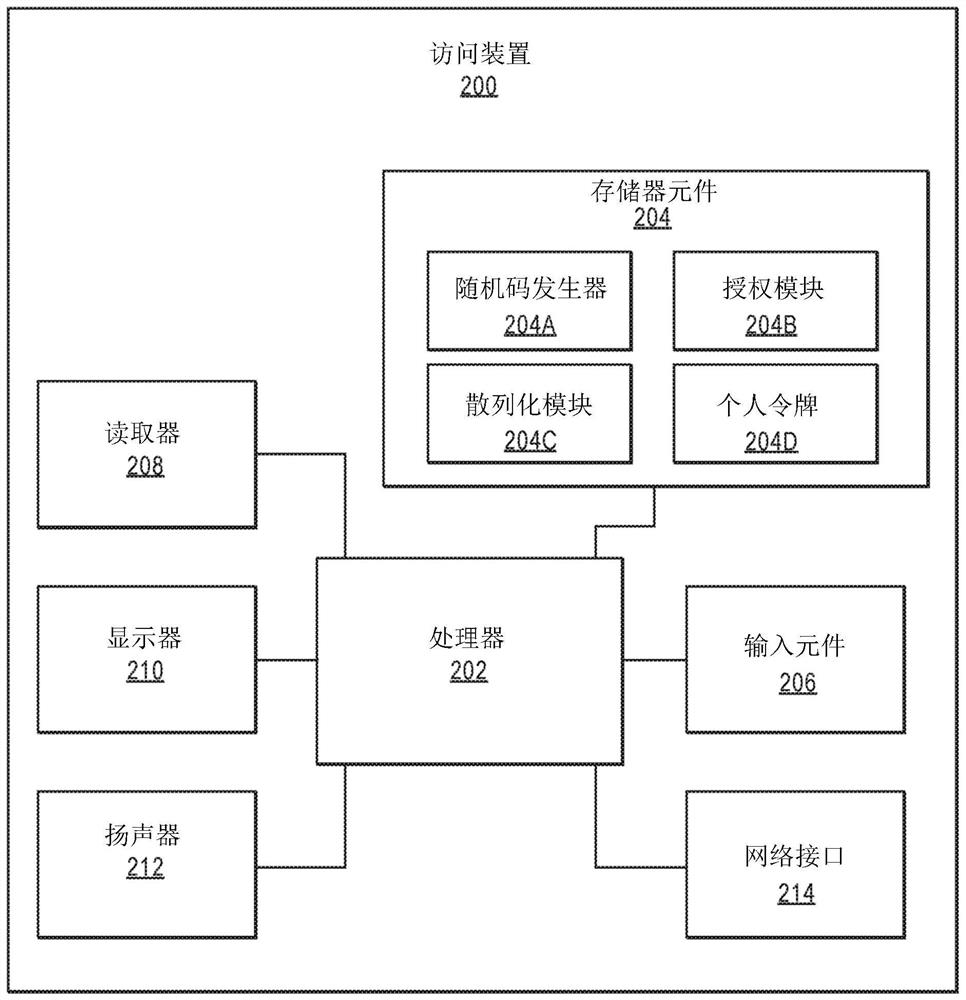
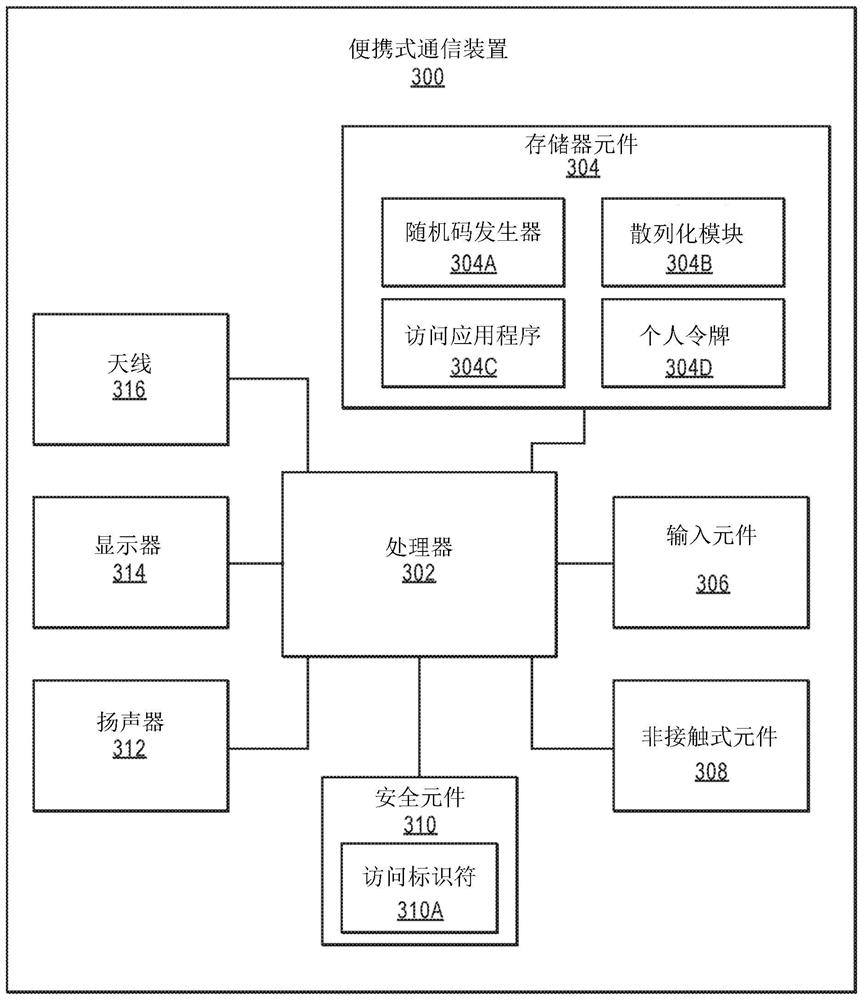
[0026] Portable communication devices (eg, mobile phones, wearable devices, IoT devices) may communicate using medium-range communication protocols such as Bluetooth and WiFi. New access devices (eg, smart POS devices, mobile POS devices) can also communicate using medium-range communication protocols. A portable communication device may interact with an access device using such a medium-range communication protocol.
[0027] The medium-range communication protocol has the following advantages. First, the user can use the portable communication device to transact with the access device hands-free without sliding, reaching or tapping the portable communication device against the access device. Furthermore, although OR codes have been used, they are difficult to implement in two-way communication between an access device and a portable communication device. Second, a user with a portable communication device can also perform transactions without being physically in close proxi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com