A Portable Secure Computer System Based on Cryptographic Hash Tag Protection
A secure computer and portable technology, which is applied in the field of network security transmission, can solve the problems of low efficiency and inability to make full use of the convenience of data communication, and achieve the effect of ensuring storage security, preventing the disclosure of plaintext sensitive data, and ensuring security and storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0082] This embodiment provides a portable secure computing architecture based on encrypted hash tag protection, specifically as follows:
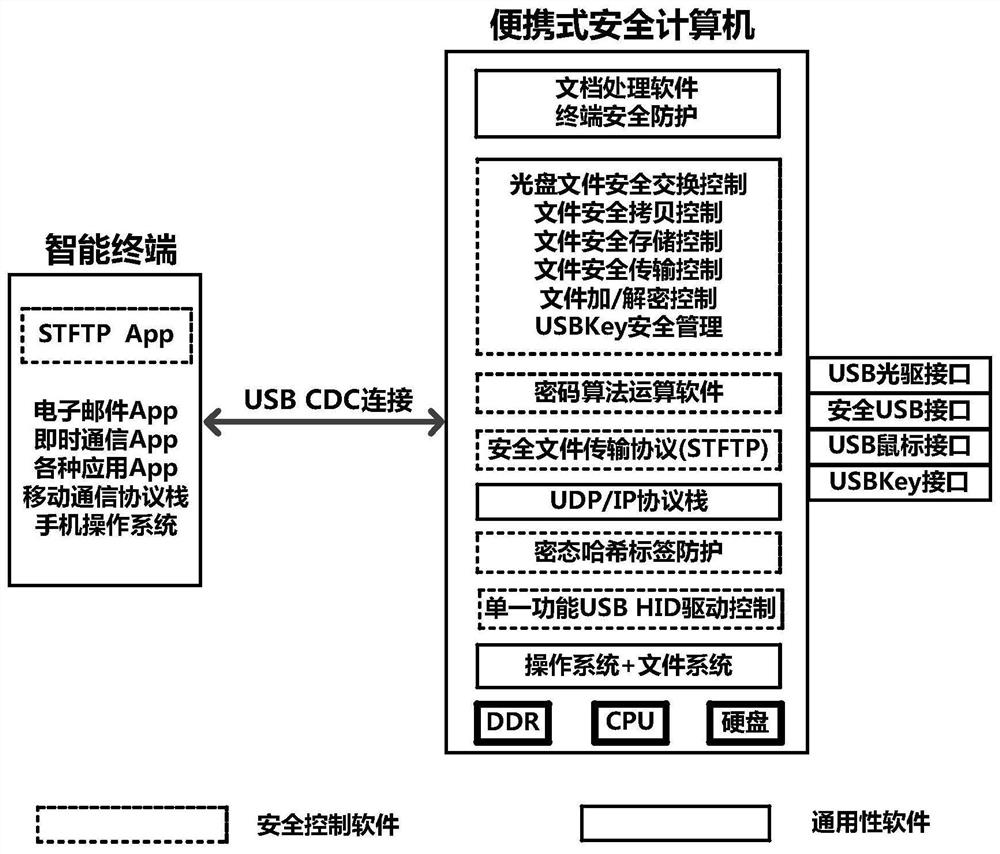
[0083] Portable secure computer systems based on cryptographic hash tag protection such as figure 1 As shown, it is implemented by a portable computer with various security control functions. Together with a mobile smart terminal (including a smart phone) running a secure TFTP App (STFTP App), it provides safe processing for the editing, storage, transmission and copying of sensitive files Create a safe computing environment. The portable security computer and the smart terminal are connected by USB CDC, based on the secure TFTP (STFTP) protocol to realize the secure exchange of encrypted sensitive files, and based on the strict isolation of the data block encrypted hash tag security mechanism to defend against network attacks and prevent Data breach of sensitive files.
[0084] The mobile smart terminal installed and running the secure ...
Embodiment 2
[0097] This embodiment is on the basis of embodiment 1:
[0098] The present embodiment provides the security mechanism that portable security computer system realizes, specifically as follows:
[0099] The design goal of the portable security computer system is to establish a safe and fully controlled operating environment that is strictly isolated from the mobile Internet to meet the security application requirements of the production, transmission, copy, storage and editing of sensitive files.
[0100] In order to achieve this security application goal, this embodiment designs a portable secure computing rack based on encrypted hash tag protection, which realizes strict password isolation between the secure computing environment and the mobile Internet environment. By adopting data block encryption hash tag mechanism, secure transmission protocol control mechanism, file encryption storage mechanism, file randomization and segmentation encrypted transmission protection mecha...
Embodiment 3
[0145] This embodiment is on the basis of embodiment 2:
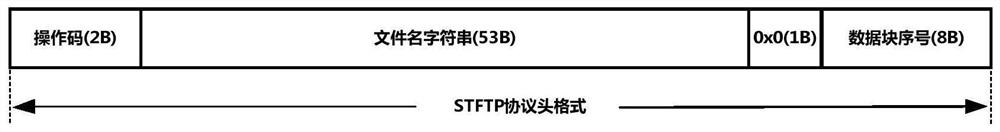
[0146] This embodiment provides the processing workflow of the encrypted hash tag protection module, which is as follows:
[0147] When a PPP (point-to-point) link based on USB CDC connection is established between the portable security computer and the intelligent terminal, different IP addresses of the same network segment are set at both ends, and the working state of the encrypted hash tag protection module is set to the initial state , initialize the serial number control value to 0, initialize the message repetition counter value to 0, and turn off the state reset timer. After the portable security computer reads the USBKey data protection key stored in the hidden file, and reads out the encrypted data of the data block protection key and the encrypted state data of the hash tag key from the USBKey, and decrypts it with the USBKey data protection key, both parties You can use the STFTP protocol for encrypted file...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com