A Trusted Booting Method of Operating System Based on Real Mode Technology
An operating system and real-mode technology, applied in the field of guidance, can solve problems such as inability to actively defend, actively defend, and insecure information systems, and achieve the effect of strengthening integrity verification and protection, eliminating attack methods, and ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings.
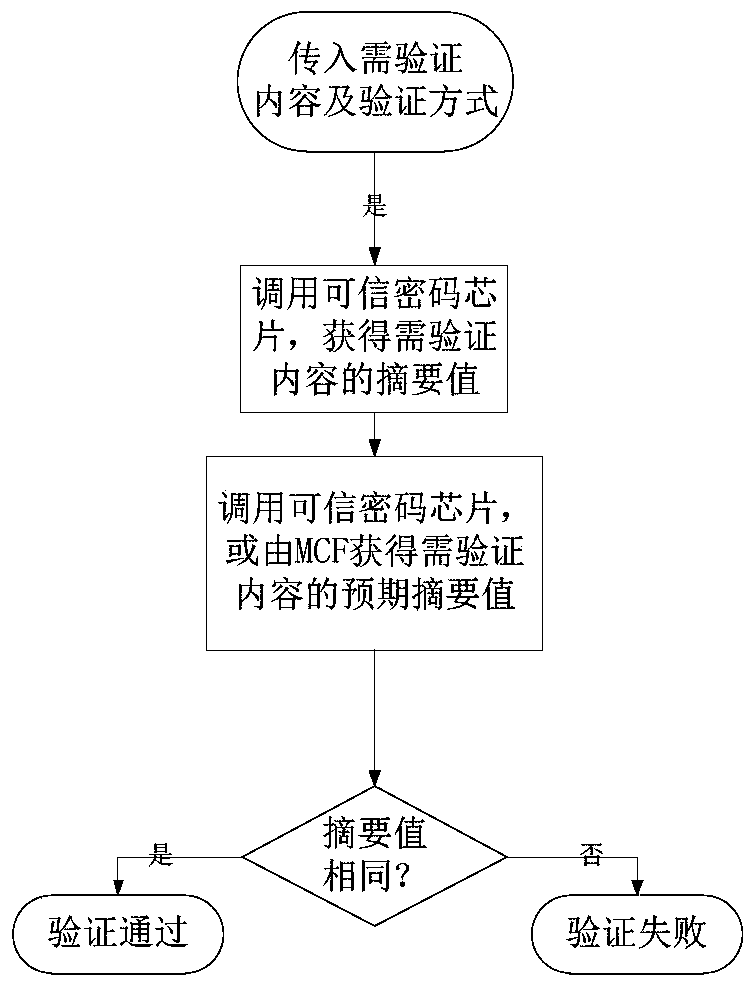
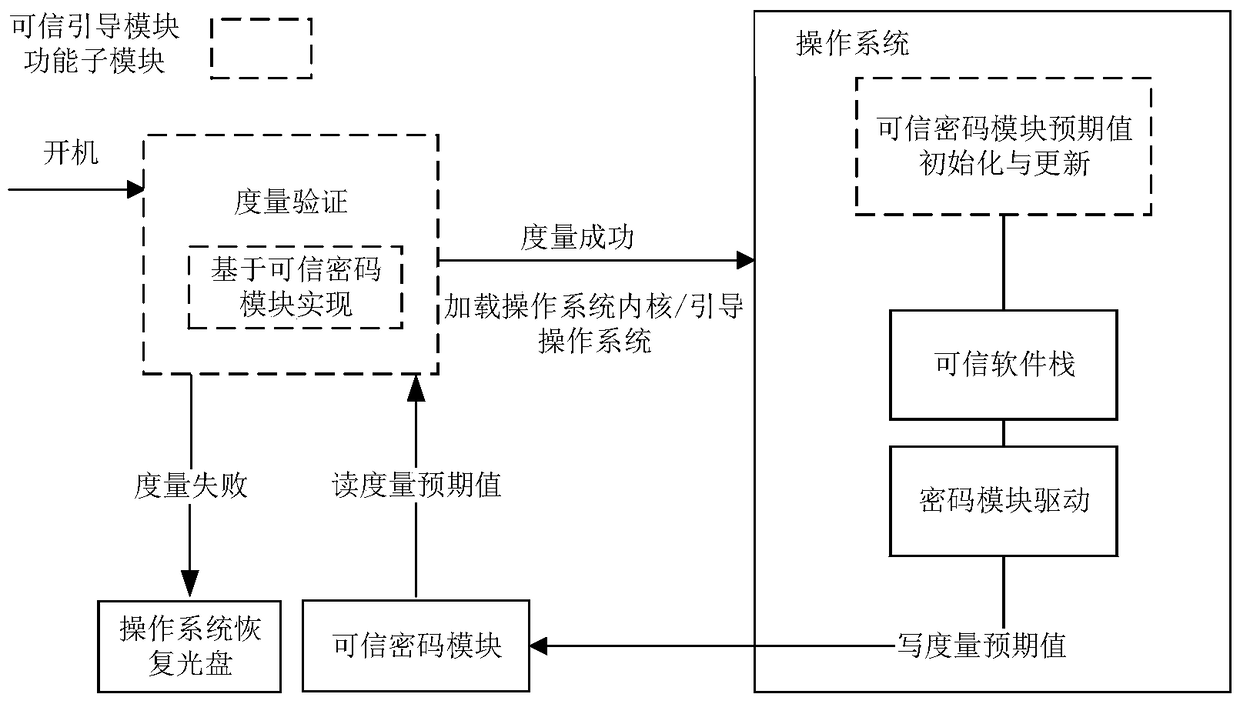
[0038] combine figure 1 and figure 2 As shown, a method for trusted booting of an operating system based on real mode technology, the method includes: (1) obtaining trusted boot program information for verification, and performing trusted measurements for different stages;
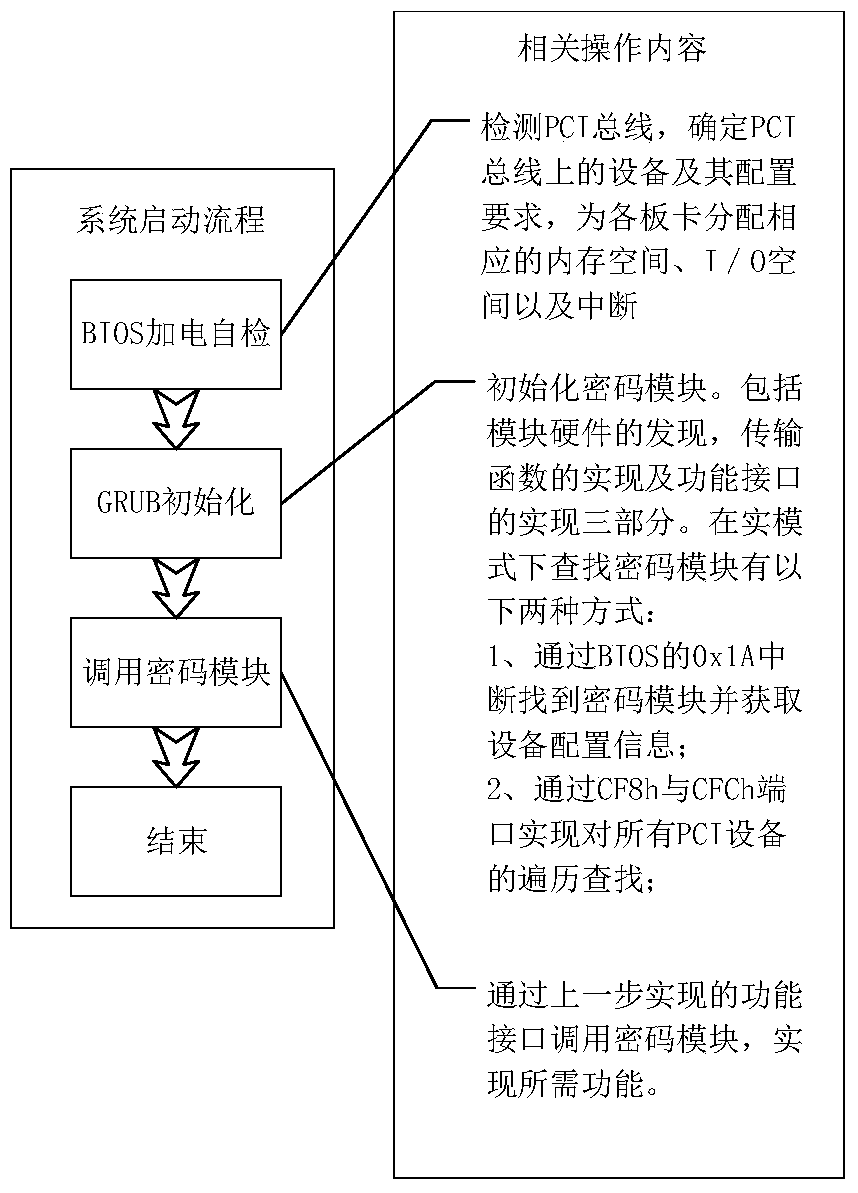
[0039] Among them, such as image 3 As shown, the real mode workflow includes: Since the original hardware driver and dynamic library of the PC-AT compatible computer system need the support of the operating system and cannot be called before the operating system is loaded, it is necessary to implement the real mode driver, which is the measurement of the GRUB stage Provide a call interface, take the same 16-bit segment and offset as 8086 for addressing, the maximum addressing space is 1MB, the maximum segment is 64KB, and 32-bit instructions can be used.
[0040] Such as Figure 4 As shown, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com