Data encryption bus self-adaptive industrial equipment remote system upgrading method
A technology of industrial equipment and data encryption, applied in the direction of digital transmission system, transmission system, bus network, etc., can solve problems such as abnormal work, lagging industrial equipment system upgrade, no frequency band protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
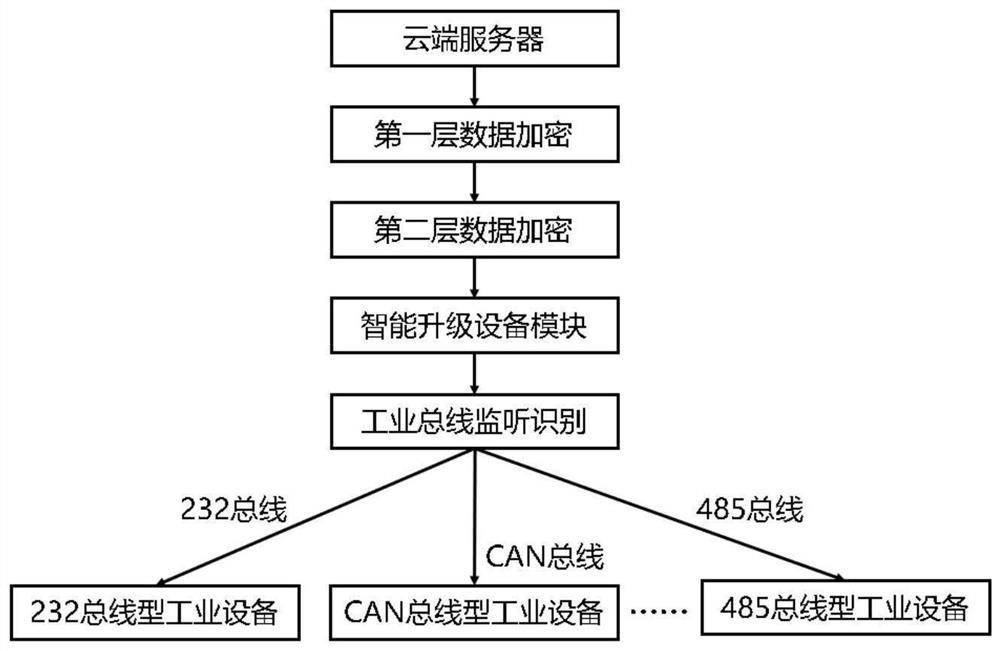
[0023] This embodiment discloses a data encryption bus adaptive remote system upgrade method for industrial equipment, such as figure 1 As shown, the method includes: connecting the smart device to the bus network owned by the industrial equipment; after the smart device is powered on, connects to the remote server, connects the transmission link through network technology, and the remote server receives the networking request of the smart device Finally, after establishing the transmission link and waiting for the connection to be completed, listen to the instructions of the remote server; after the remote server sends the data, it performs the first layer of encryption of the software data, and the first layer of encryption is the conversion of the software data to be transmitted ; After the binary conversion of the data is completed, the data is encrypted by the second layer, wherein, the encrypted data of the second layer includes network IP and port; the data encrypted by ...
Embodiment 2
[0044] This embodiment discloses a data encryption bus adaptive remote upgrade system for industrial equipment, which at least includes smart devices and remote servers. The smart devices are connected to the bus network of industrial devices. After the smart devices are powered on, they connect to the remote server. The transmission link is connected through network technology. After the remote server receives the networking request of the smart device, it establishes the transmission link and waits for the connection to be completed, then monitors the instructions of the remote server; after the remote server sends the data, it performs the first layer of encryption of the software data. The first layer of encryption is the conversion of the software data to be transmitted; after the conversion of the data is completed, the second layer of encryption is carried out to the data, wherein, the network IP and port are included; after the second layer of encryption The final data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com