Trusted execution environment construction method, system and storage medium
A technology of execution environment and construction method, applied in the direction of internal/peripheral computer component protection, platform integrity maintenance, etc., can solve problems such as reducing software operation security, unable to provide software operation environment, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] In the description of the present invention, if related to orientation description, such as "up", "down", "front", "rear", "left", "right"
[0052] Intel SGX was proposed by Intel in 2013, and this technology includes a series of new additions to Intel processors
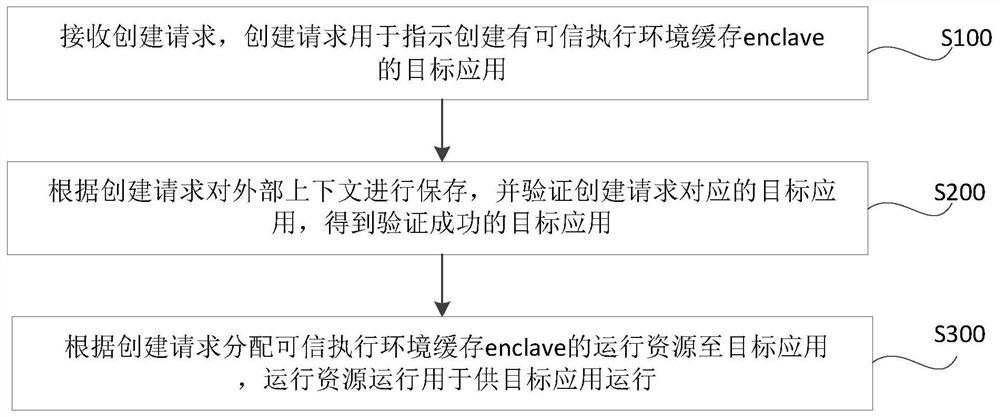
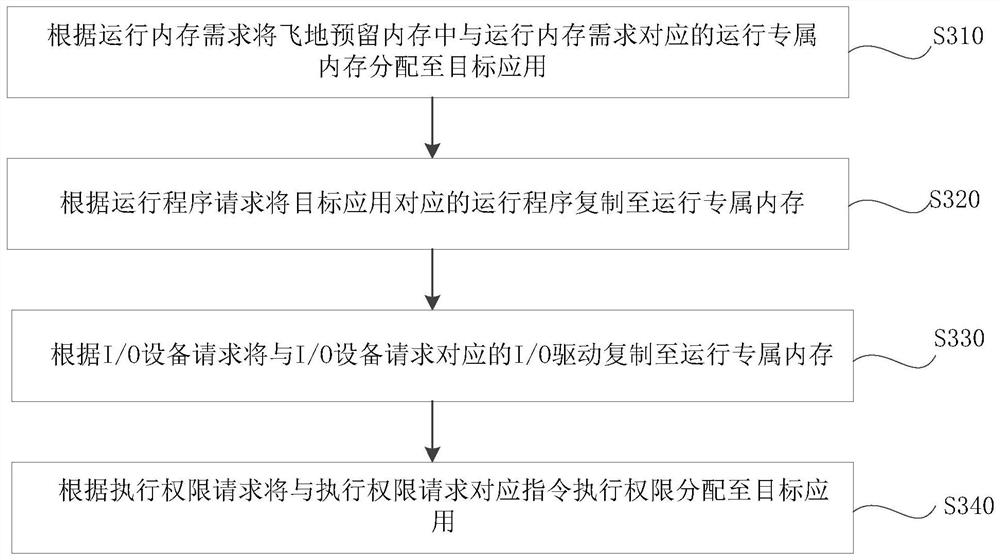
[0063] In some embodiments, creating a request includes: a running memory requirement, a running program request, an I / O device request, an execution
[0064] An enclave is an application that can create a protected execution environment in memory, and each target application can
[0069] S340, assign the instruction execution authority corresponding to the execution authority request to the target application according to the execution authority request.
[0072] S400, if the enclave reserved memory is less than the memory size corresponding to the running memory requirement, re-monitor the creation request.
[0077] S600, the I / O driver completes the initialization of the I / O device corresponding to the I / O devi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com