Method for digital key misbehavior and sybil attack detection through user profiling
A key, digital technology, applied in the field of digital key misbehavior and sybil attack detection through user archives, which can solve problems such as vehicle security damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
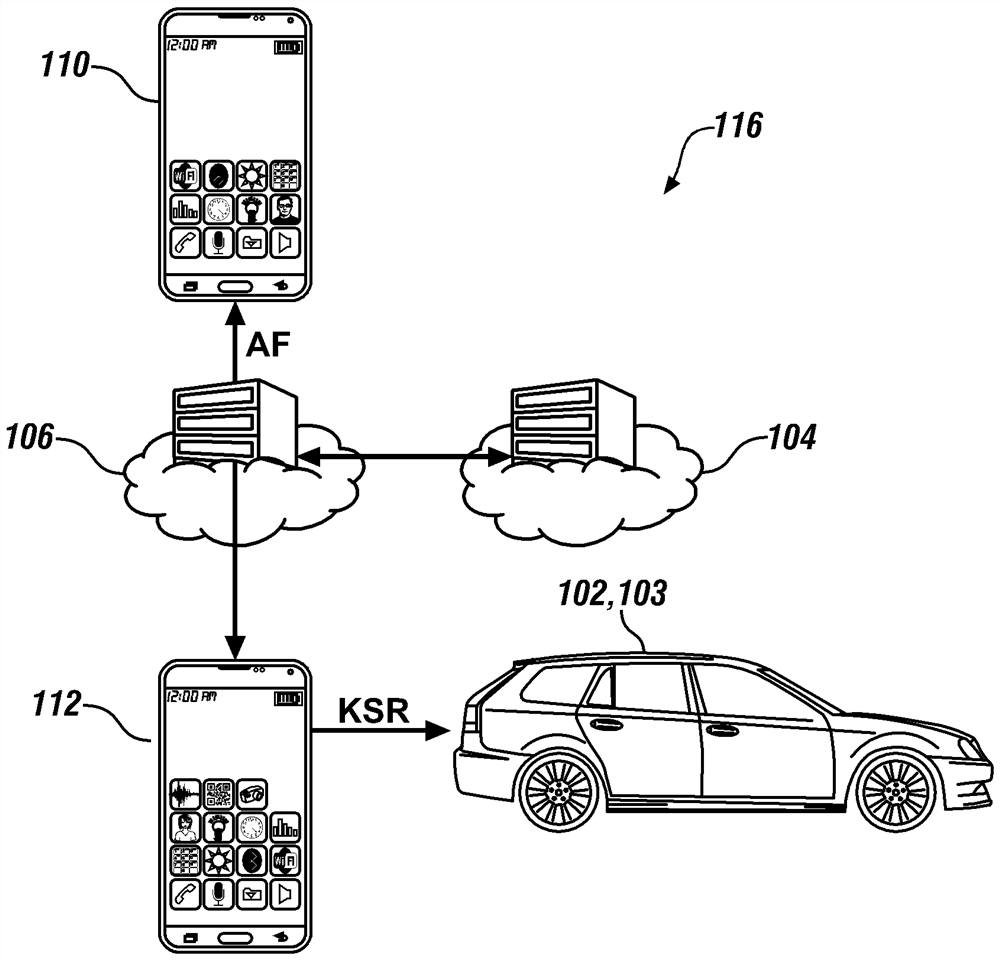
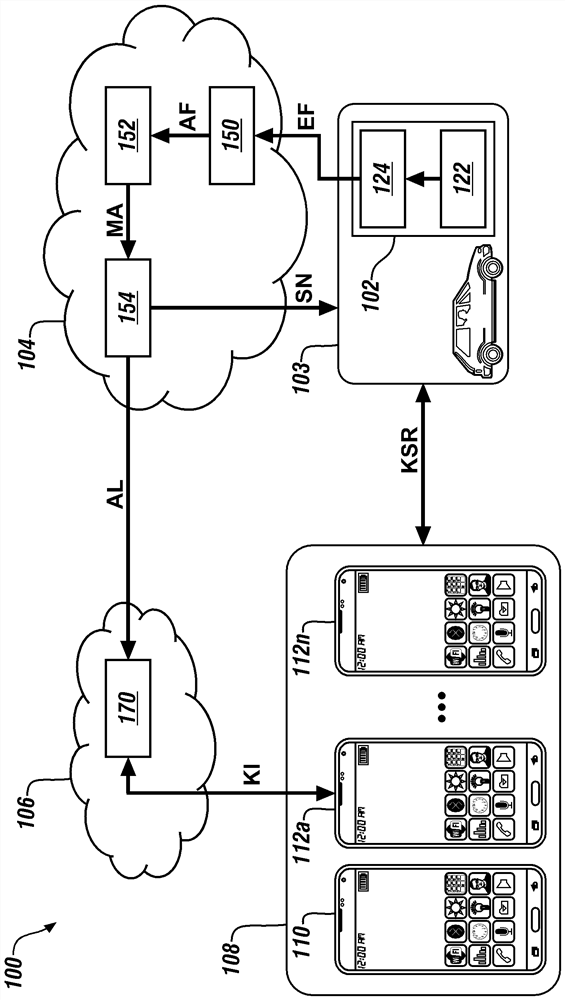
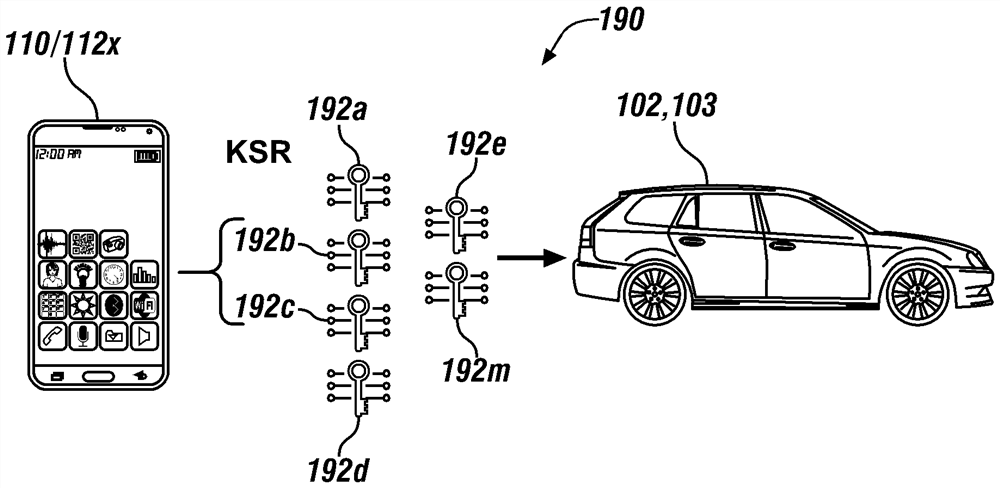
[0069] Embodiments of the present disclosure generally describe a technique to detect bad behavior and Sybil attacks in digital key creation and sharing by identifying key aspects of system and / or user behavior. Inconsistencies in the spatial and / or temporal distribution of generated digital keys may invoke alert notifications from vehicle backend systems. This technique typically builds a detection system built around a digital key system that enhances attack detection capabilities. A Sybil attack typically involves generating many inappropriate (or invalid) digital key-sharing requests that prevent the electronic circuitry utilizing the digital key from distinguishing between valid and invalid requests.
[0070] The definition of the characteristics that make up the behavior pattern of the issued digital keys can be established on a per user basis. The technique typically derives user patterns through statistical analysis and archives them. Statistical analysis can establi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com