A privacy protection face recognition system and method for smart home
A technology for smart home and human protection, applied in the field of information security, can solve the problems of inability to balance recognition accuracy, communication overhead and time overhead, leakage of user privacy, lack of encryption modules, etc., achieving low communication overhead and algorithm space complexity, Improves privacy and security, meets hardware conditions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
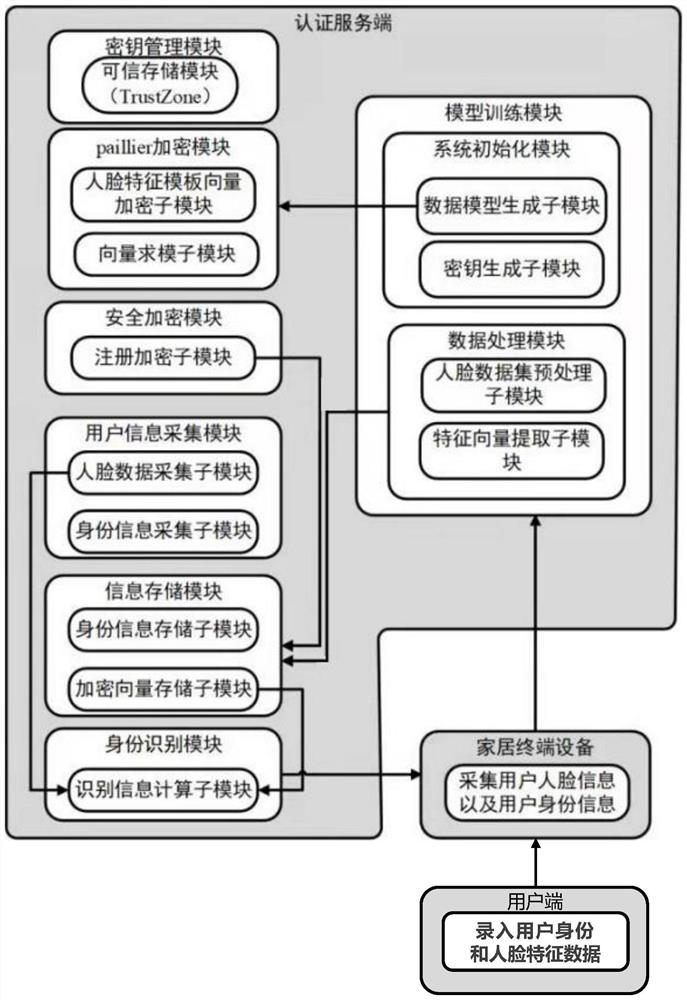
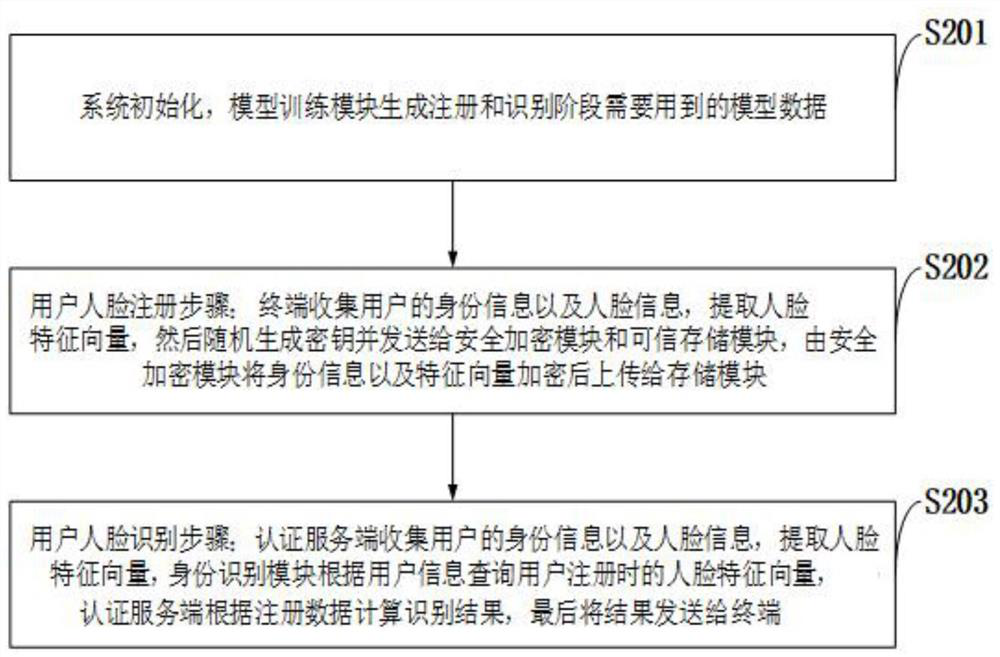
[0042] like figure 1 As shown, it is a schematic structural diagram of a smart home-oriented privacy protection face recognition system of the present invention. The system includes three components: user terminal, home terminal equipment and authentication server. in:
[0043] The client is used to collect facial feature data and user identity information, and submit them to the home terminal device together with the user request.
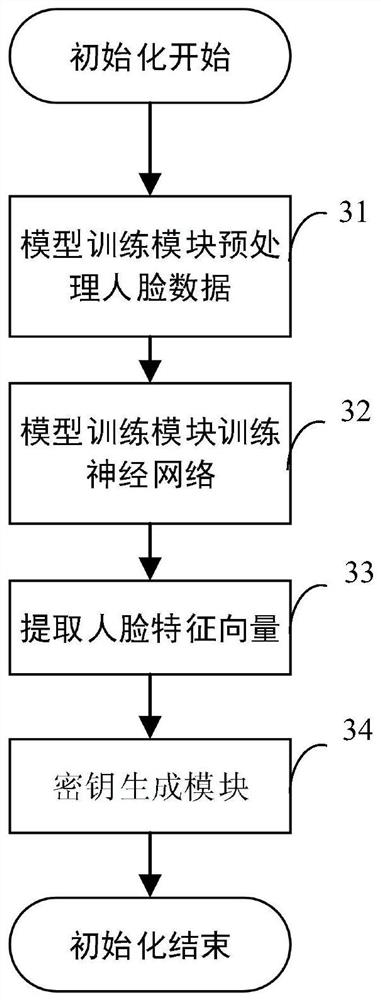
[0044] The home terminal device is used to receive the user's request and the collected facial feature data and user identity information, and submit the request and information to the model training module of the authentication server. The model training module includes a system initialization module and a data processing module;
[0045] The authentication server (such as the host of the smart...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com