A carrier-free text steganography method and a carrier-free text steganography device for a component histogram
A histogram, carrier-free technology, applied in the field of information security, can solve the problems of low success rate of hiding and small information hiding capacity, and achieve the effect of good effect, improved security, and reduced fine-grainedness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
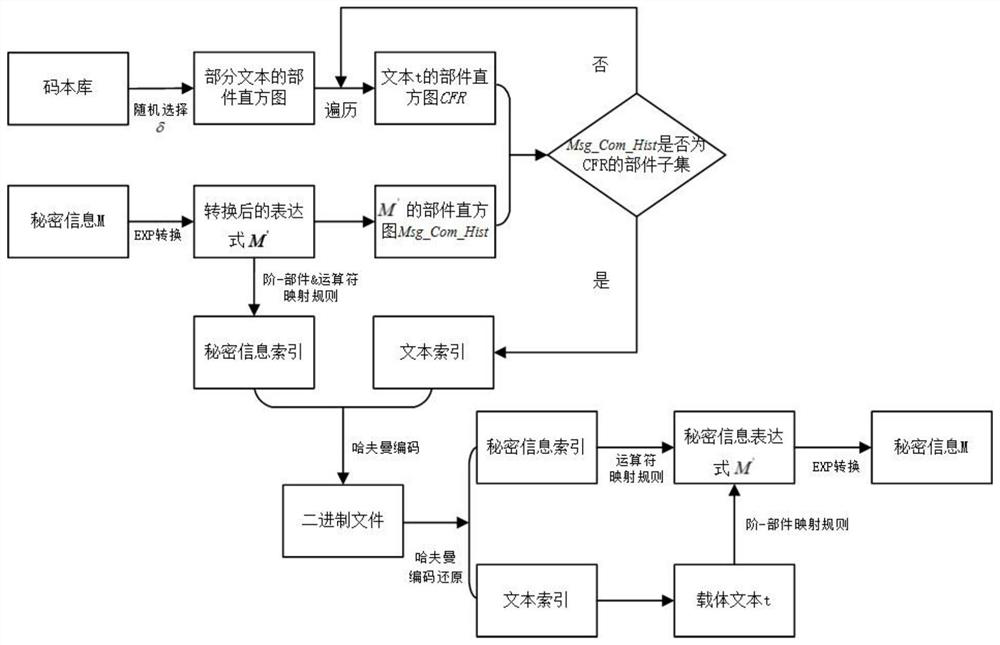
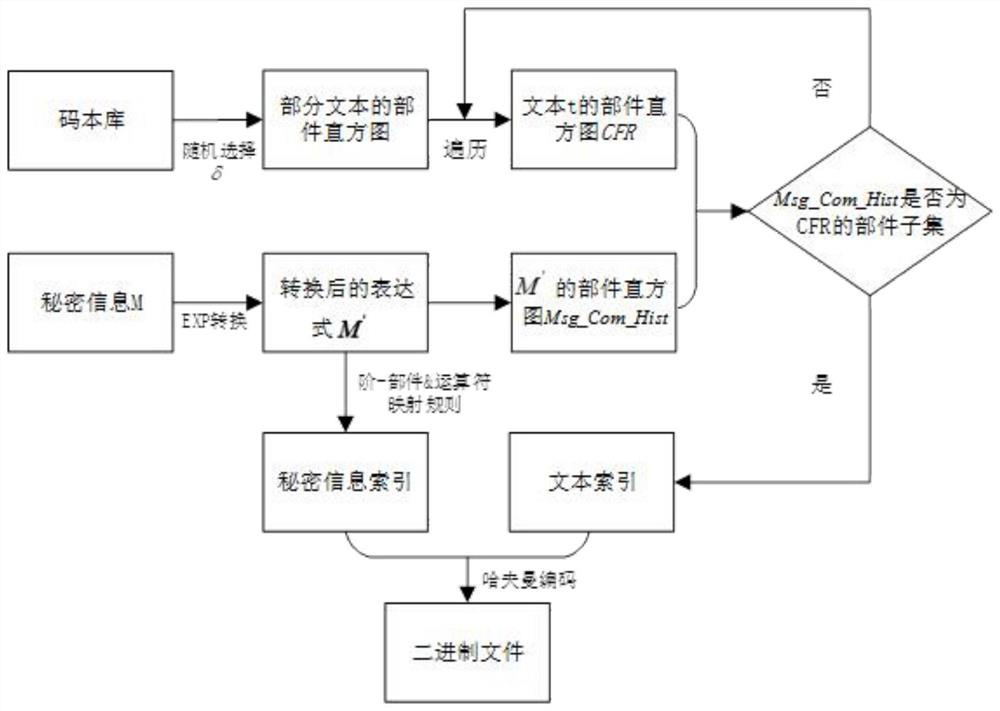
[0069] refer to Figure 1-5 The present invention discloses a method and device for text-less steganography of component histograms.
[0070] This section takes passing a secret message "fight tiger tonight" as an example to show the whole process of information hiding and restoration. The information hiding process is as follows:
[0071] (1) First, the sender converts each Chinese character of the secret message into a mathematical expression of Chinese characters:
[0072] ['today','night','fight','old','tiger']=>['116','102lr234','430lr6','338lu21','386lu13']
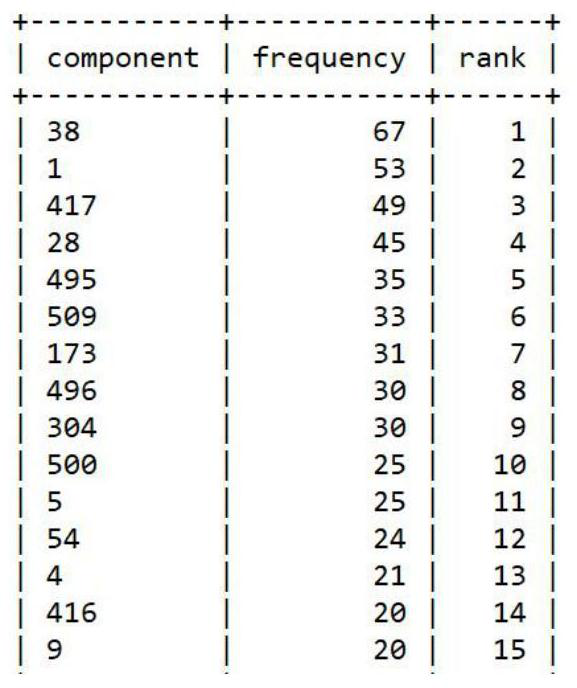
[0073] (2) Given a random selection threshold, for example, by randomly selecting 0.1 times the total number of texts in the text_table, through Algorithm 2, to obtain the histogram of the encrypted text and its components, assuming that the obtained encrypted text number is '71490'.
[0074] (3) Assume that the components and orders in the histogram of the encrypted text components have the following corresponde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com