Longitudinal federated learning-based social network cross-platform malicious user detection method
A malicious user and social network technology, applied in machine learning, platform integrity maintenance, data processing applications, etc., can solve the problem that data is difficult to meet the detection requirements, so as to improve the generalization ability and detection effect, and ensure security and accuracy sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
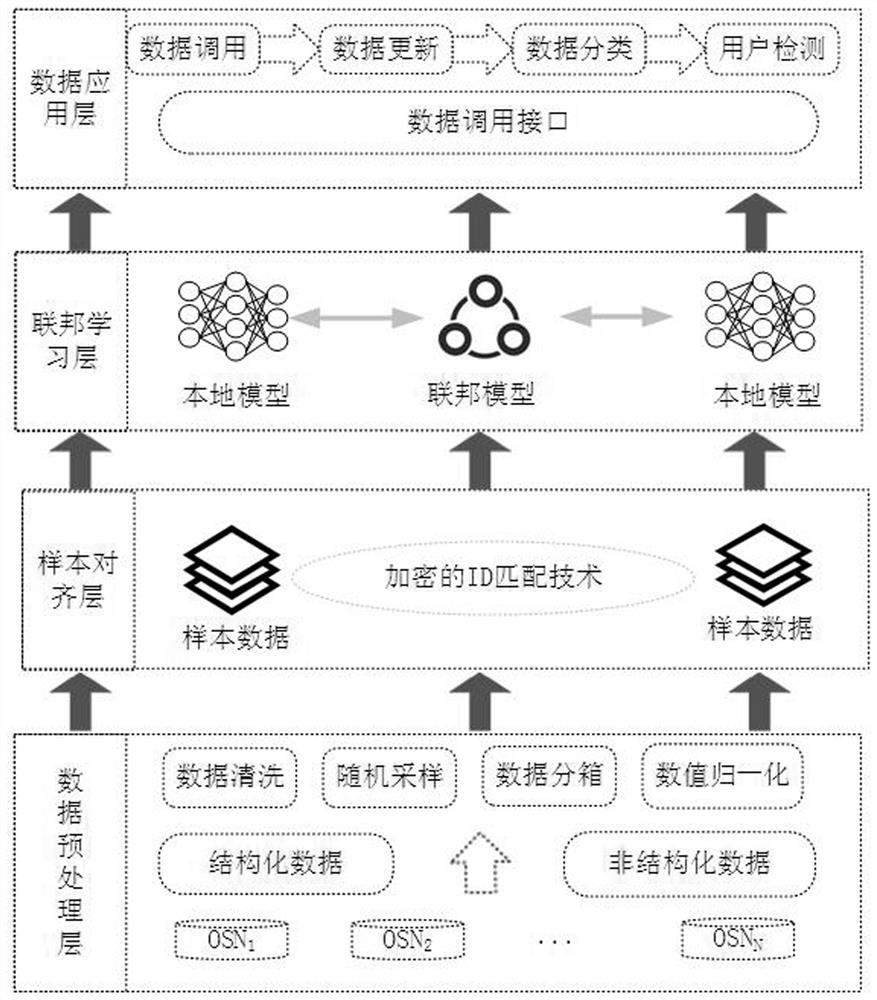
[0089]The present invention combines the multimedia social network CyVOD to expand and improve the existing federated learning framework, and builds a social network cross-platform malicious user detection framework based on vertical federated learning, such as Figure 6 As shown, the safe and compliant fusion of multi-party data for modeling analysis can achieve high-quality detection of malicious users and further maintain the ecological environment of social networks.
[0090] The whole architecture is divided into four parts, which are data preprocessing stage, sample alignment stage, federated learning stage, and data application stage.
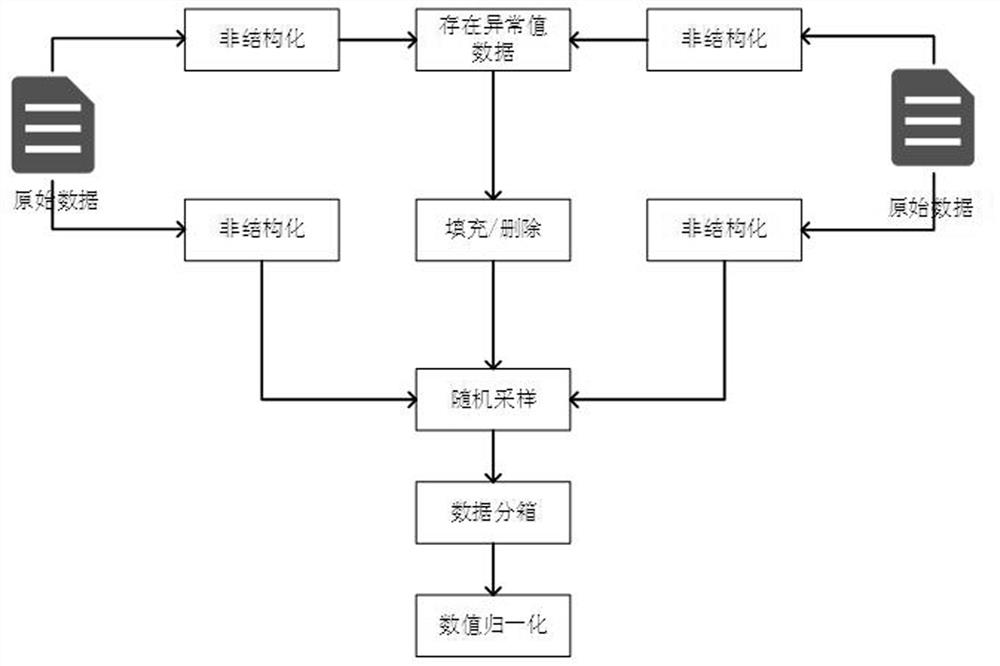
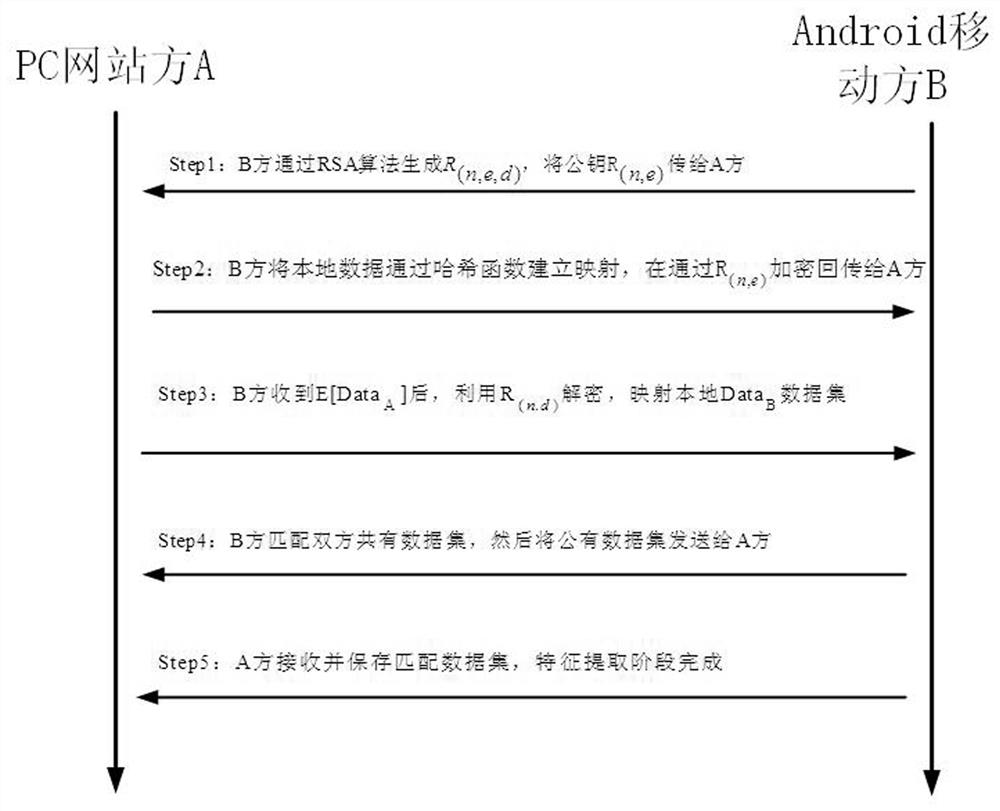
[0091] Data preprocessing stage: In this stage, the instance objects select CyVOD’s Android mobile side (active side) and PC website side (passive side) as data providers, and build OSNs six-tuples (video, policy, guide, Notifications, posts, false information) metadata experiment platform, a total of 68 user click actions, a total of 50...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com