Illegal evidence tracing system based on block chain
A traceability system and blockchain technology, applied in the field of information recording, can solve problems such as illegality, inability to trace videos or images, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
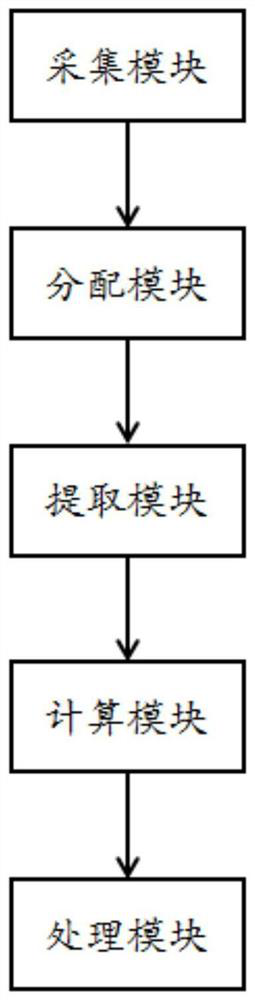
[0031] The embodiment is basically as attached figure 1 shown, including:
[0032] The collection module is used to collect original illegal evidence, which includes surveillance video and surveillance images;
[0033] The allocation module is used to obtain the progress information of the case, and distribute the original illegal evidence to the case nodes according to the progress information. The case nodes are public security nodes, procuratorate nodes and court nodes in the blockchain network;
[0034] The extraction module is used to extract the leaked original illegal evidence, which is recorded as the leaked illegal evidence, and the relationship between the change amount and time of the pixel set of the leaked illegal evidence is related to the case node;
[0035] The calculation module is used to obtain the original illegal evidence corresponding to the leaking illegal evidence, and obtain key information; and obtain multiple pairs of key frames from the leaking ill...
Embodiment 2
[0045] The only difference from Embodiment 1 is that before assigning the original illegal evidence according to the progress information, the distribution module adds the information of the person in charge to the original illegal evidence to obtain encrypted illegal evidence. In this embodiment, after receiving the calling instruction of the input original illegal evidence, the information of the person in charge corresponding to the calling instruction is obtained, and the original illegal evidence is extracted, and the variation of the pixel set in the original illegal evidence is changed according to the information of the person in charge. According to the relationship of time, the encrypted illegal evidence is obtained. When the original illegal evidence is leaked, the corresponding person in charge can be quickly found based on the information of the person in charge, which is conducive to accurate traceability. At the same time, the distribution module uses the hash a...
Embodiment 3
[0048] The only difference from Embodiment 2 is that in this embodiment, for collecting the original illegal evidence, the technical idea of "photographing first, then deleting" is adopted, that is to say, the surveillance video is collected first, and then the surveillance video is captured. Surveillance images that do not meet the requirements are deleted. It should be noted that, technically speaking, surveillance video is composed of several surveillance images. Specifically, in this embodiment, firstly, the monitoring video is collected by the camera; then, the image data of the monitoring image with the preset frame number in the monitoring video is extracted, and the monitoring image with the preset frame number in the monitoring video is detected by image recognition technology. Whether the image data of the image changes: If the image data of the surveillance image with the preset number of frames changes, an evidence electronic stamp is generated according to the su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com