Container mirror image security detection method, terminal equipment and storage medium
A technology of security detection and mirroring, applied in computer security devices, instruments, software deployment, etc., can solve problems such as insufficient data detection and inability to meet container security usage scenarios, and achieve the effect of improving the level of security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
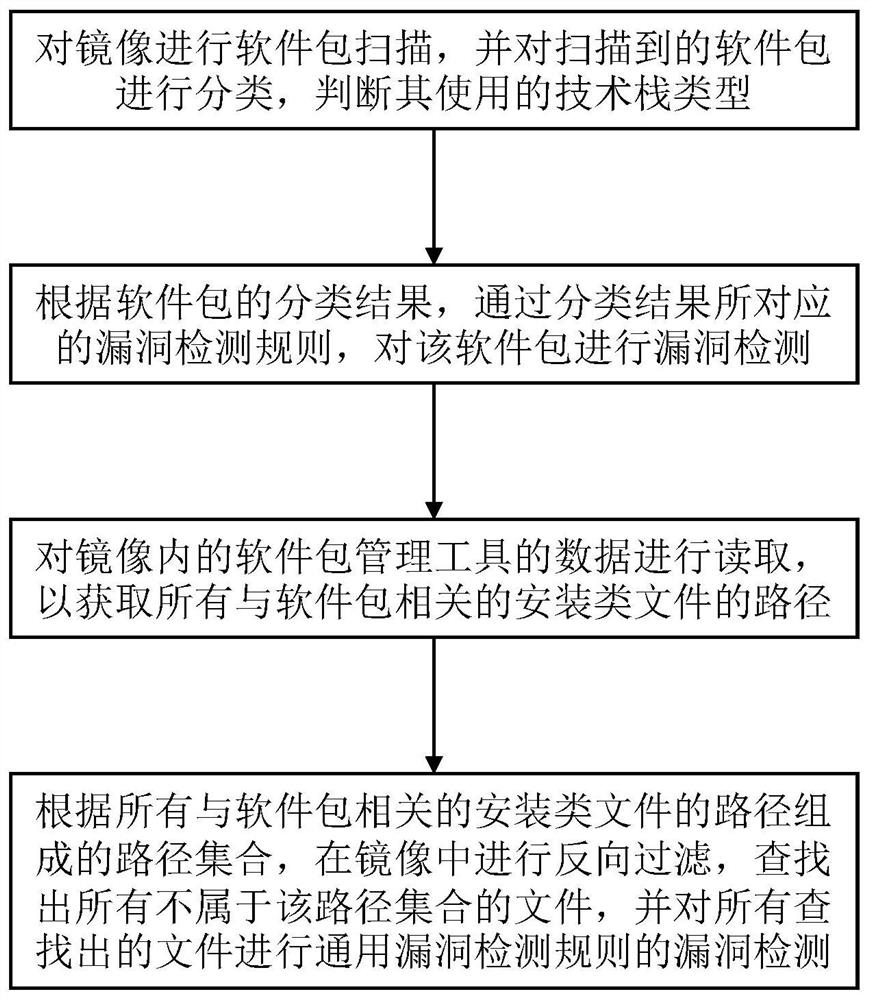
[0023] The embodiment of the present invention provides a container image security detection method, such as figure 1 As shown, the method includes the following steps:
[0024] S1: Scan the image for software packages, classify the scanned software packages, and determine the type of technology stack used.
[0025] When classifying the software package, it is classified according to the file name and file suffix of each file corresponding to the software package. The result of the classification is the type of the technology stack to which it belongs, such as the type with java as the main service, and the type with php as the main service. different types, etc., different types have pre-established different vulnerability detection rules. Through targeted vulnerability detection, it is possible to detect sensitive information (password leakage, unobfuscated WEB source code), viruses, Trojan horses, web backdoors and other security risks that cannot be detected by convention...
Embodiment 2
[0044] The present invention also provides a container image security detection terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the computer program, the present invention is realized. Steps in the above method embodiment of the first embodiment of the invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com