IoT ddos detection, defense method, detection device and storage medium based on distributed machine learning and blockchain
A machine learning and detection device technology, applied in the field of data processing, can solve the problems of insufficient DDoS traffic identification and filtering efficiency, insufficient early warning of similar attacks, etc., to achieve improved identification accuracy, low hardware performance requirements, and iterative optimization Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
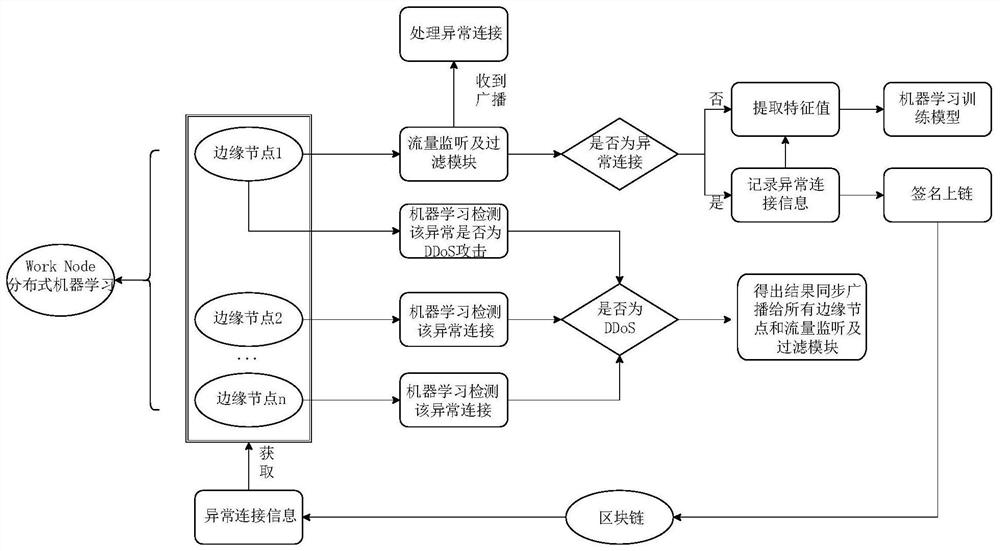
[0048] Embodiment one, refer to figure 1 , Figure 3-Figure 4 , illustrating this embodiment, a method for detecting DDoS in the Internet of Things based on distributed machine learning and blockchain, comprising the following steps:
[0049] Step 1, the traffic monitoring and filtering module obtains the traffic input by the edge node, and judges whether the traffic is an abnormal connection, if so, execute step 3, if not, execute step 2;
[0050] Among them, the traffic monitoring and filtering module can capture and analyze traffic, capture data packets flowing through the network card, and filter abnormal traffic by establishing rules.
[0051] Among them, the establishment rules specifically include:
[0052] Step 11, within a unit time, if a source ip sends access times v exceeding the set upper limit, it is determined to be abnormal.
[0053] Step 1 and 2: After receiving the SYN message, the traffic monitoring and filtering module responds with a specific cookie. If...
Embodiment 2
[0089] Embodiment two, refer to figure 2 , to illustrate this embodiment, the present invention proposes a DDoS detection device for the Internet of Things based on distributed machine learning and blockchain, including a traffic monitoring and filtering module, a machine learning module and a blockchain module; the traffic monitoring and filtering module It is used to receive traffic sent by edge nodes, and to filter and feature extract abnormal traffic; the machine learning module is used to learn and detect abnormal traffic; the block chain module is used to store abnormal traffic; the traffic monitoring and filtering module The extracted features are transmitted to the blockchain module; edge nodes obtain abnormal traffic data from the blockchain module and transmit them to the machine learning module.
[0090] The traffic monitoring and filtering module described in this embodiment has a traffic forwarding function, a traffic interception function and a feature extraction ...
Embodiment 3
[0093] Embodiment three, refer to Figure 5 Illustrate this embodiment, a kind of Internet of things DDoS defense method based on distributed machine learning and block chain, comprises the following steps:
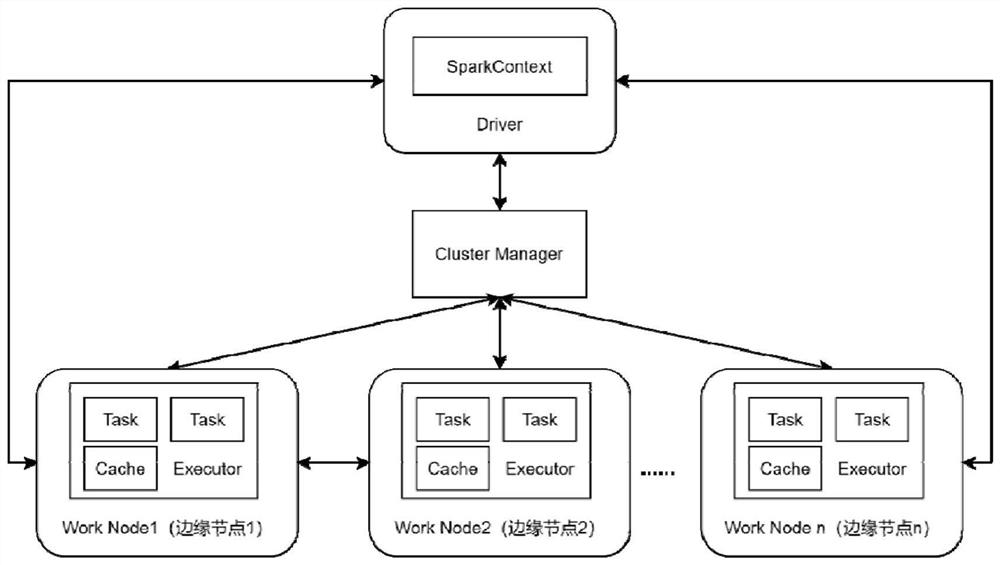
[0094] S110. Run the detection device described in Embodiment 2 at the entrance of the Internet of Things network, and start the Spark MLlib distributed machine learning framework;
[0095] S120. When the user uses the IoT device, the traffic monitoring and filtering module captures and extracts its characteristic value and records it locally as a machine learning data set;
[0096] S130. After encountering abnormal traffic, the edge node records the abnormal connection information and uploads it to the blockchain;
[0097] S140. All edge nodes use the machine learning model to detect the abnormal connection information, and if it is a DDoS attack, verify the block information and record it locally;
[0098] S150. The blockchain module synchronizes all edge nodes in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com