Key management system and method for federated learning security audit, and storage medium
A key management system and security audit technology, applied in integrated learning, transmission systems, digital transmission systems, etc., can solve the problems of federated learning norms and security threats, loss of private keys, lack of key management records, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
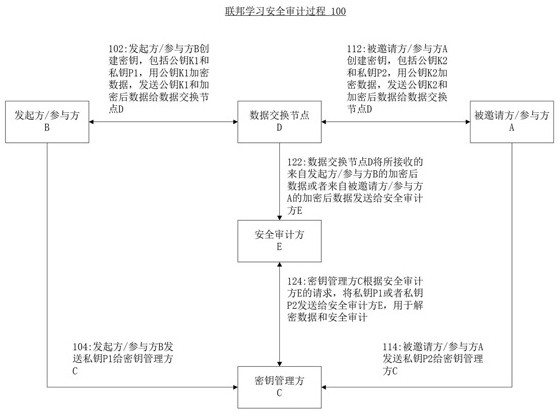
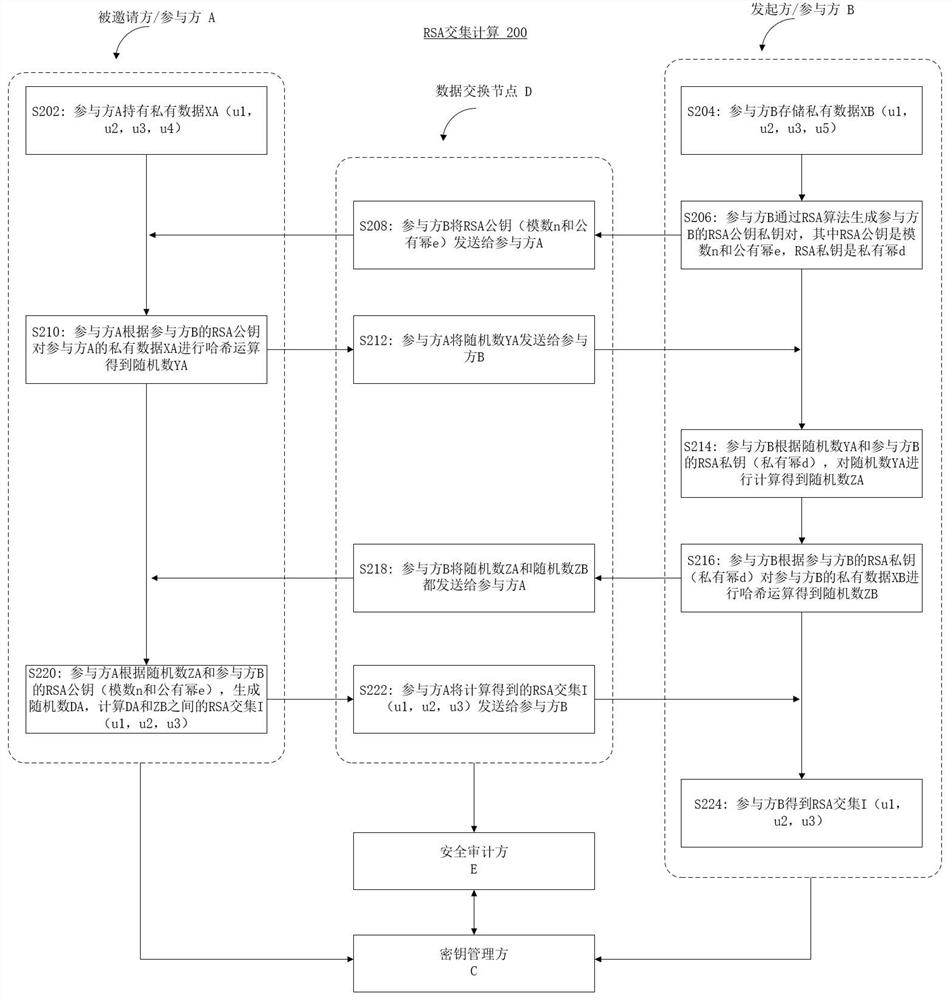
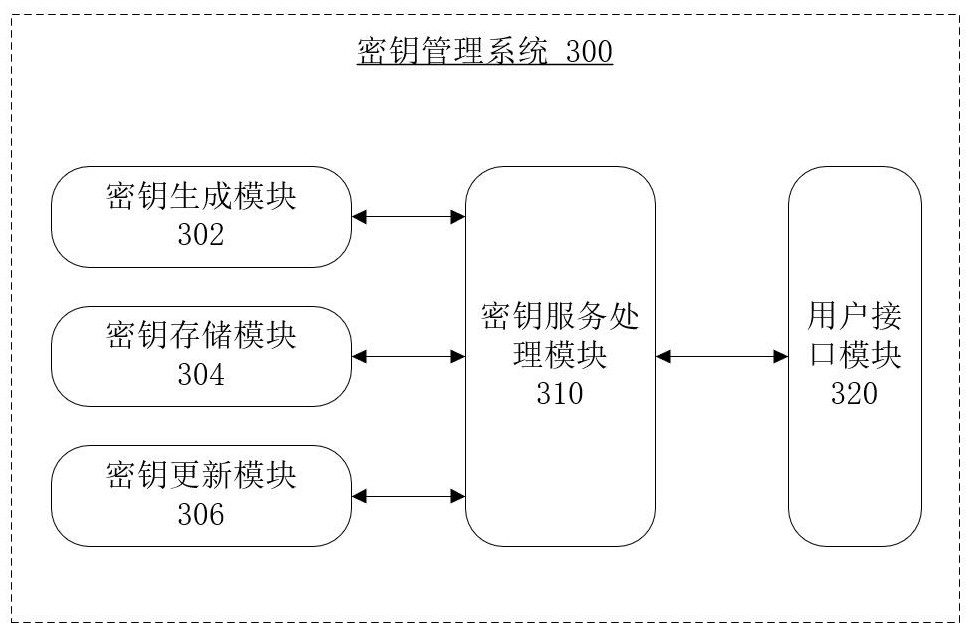
[0042] The embodiment of the present application provides a key management system, method and storage medium for federated learning security audit. The key management system includes: a user interface module, wherein the user interface module receives user requests; a key service processing module, wherein the key service processing module is connected to the user interface module, and the key service processing module The key service processing module is configured to generate a visible key space specific to the user, and keys in the visible key space specific to the user can be used to respond to the user's request; the key generation module, wherein, The key generation module is connected to the key service processing module; and a key storage module. Wherein, the state of each key stored in the key storage module is determined according to whether the federated learning task corresponding to the key is completed and whether the security audit requirement corresponding to t...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap