Malicious social user detection method based on adversarial learning
A detection method and user technology, applied in the field of malicious social user detection, can solve the problems of neural network error high-confidence prediction target, reduce the stability and reliability of malicious social user detection, and low robustness of neural network. The effect of semantic complexity, enhanced generalization ability, and increased representation ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
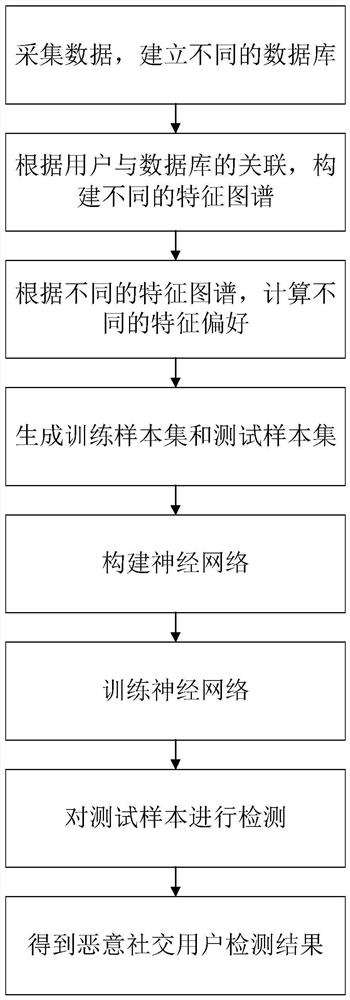
[0032] The embodiments and effects of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0033] refer to figure 1 , the implementation of this example includes the following steps:
[0034] Step 1, collecting data and establishing different databases.
[0035] 1.1) Collect the social data in the social network platform, perform data cleaning, data transformation and data standard preprocessing on the collected social data in sequence, and obtain the preprocessed social data:
[0036]This example uses, but is not limited to, the zeroing method for data cleaning, the smooth aggregation method for data transformation, and the unified method for data standardization, that is, first set the invalid and missing values of the collected social data to zero, and then use smooth aggregation Process and convert the set social data into a form suitable for social data mining, and then convert the converted social data into ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com