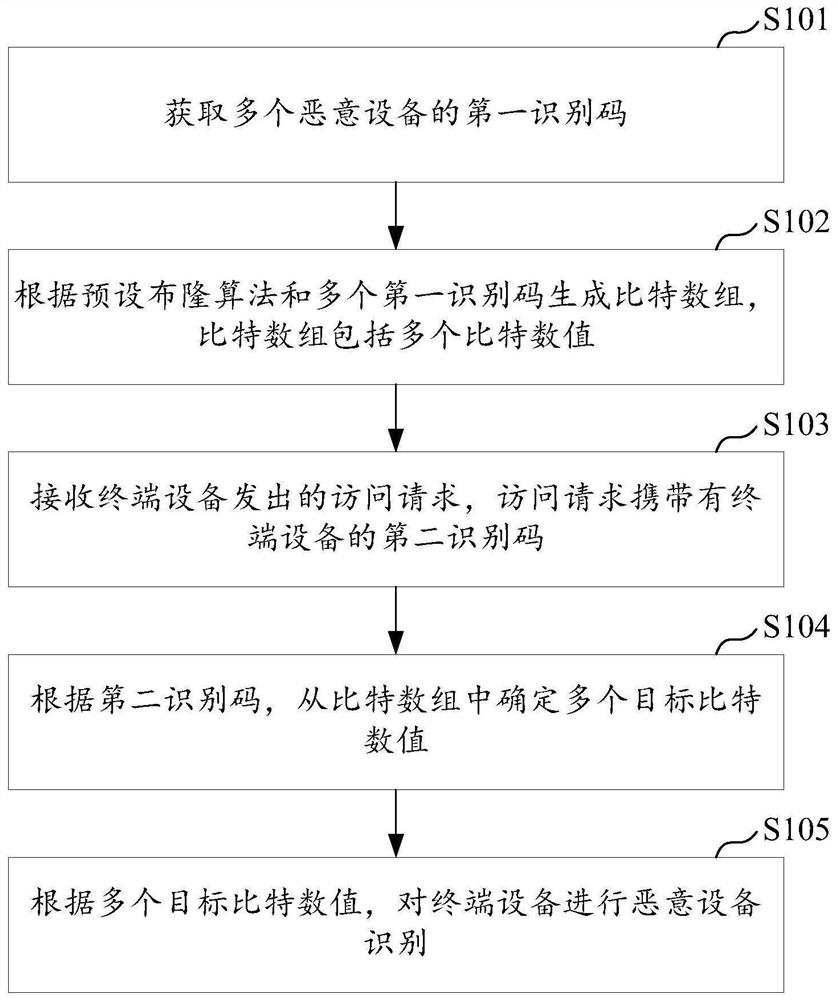
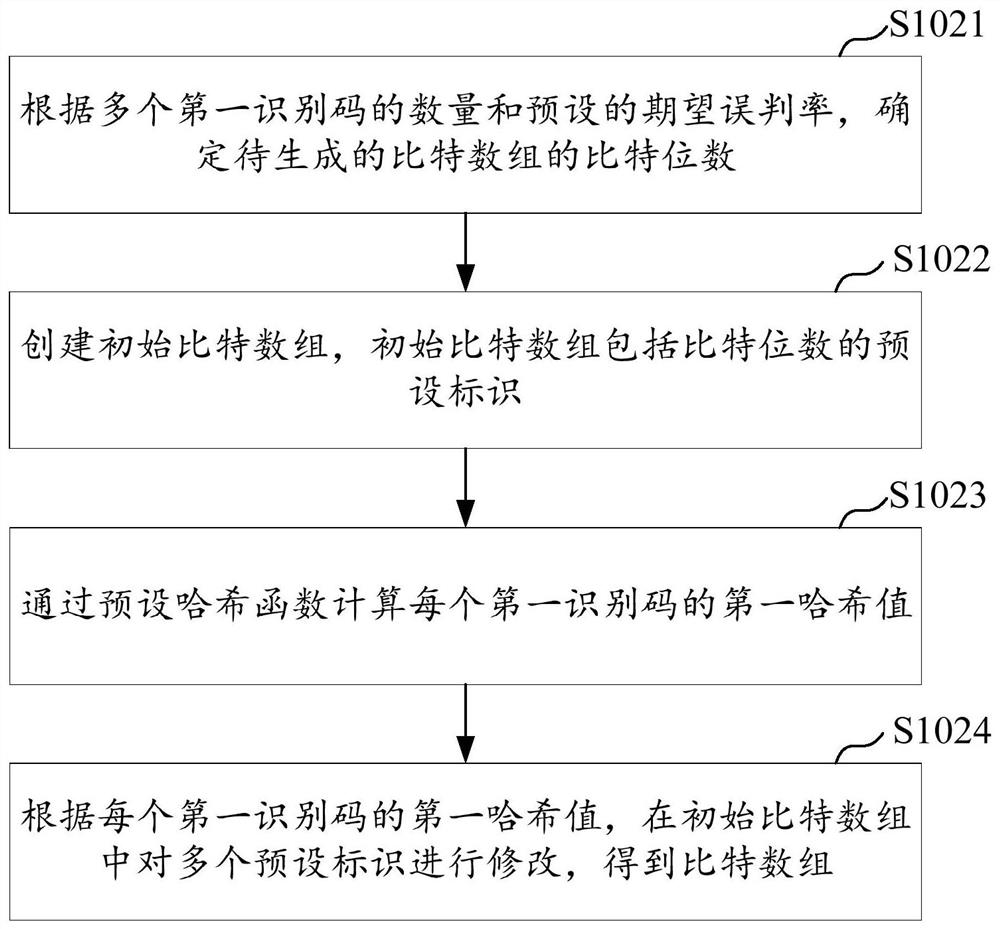
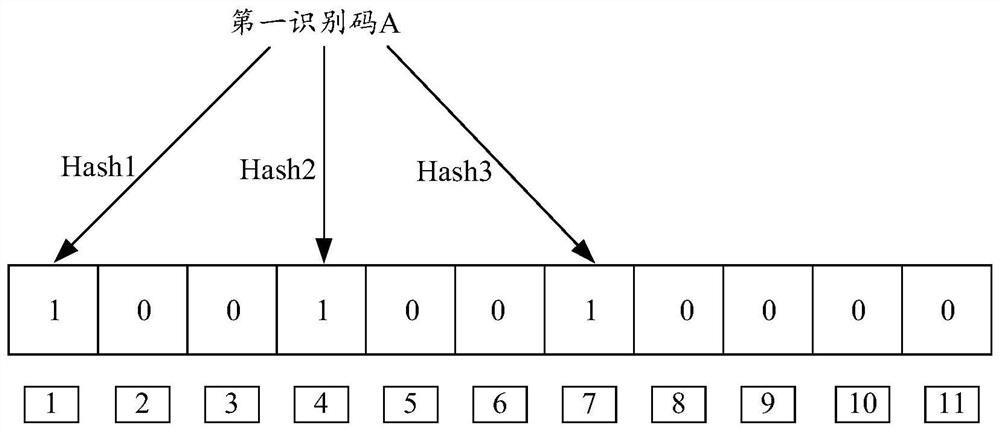
Malicious device identification method and apparatus, server and storage medium
A device identification and malicious technology, applied in computer security devices, instruments, special data processing applications, etc., can solve the problems of low identification efficiency, consume more time, and a large amount of memory space, and achieve the effect of improving identification efficiency and accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Next, the technical scheme in the present application will be clear and completely, and the embodiments described herein are described herein, and not all of the embodiments of the present disclosure, not all of the embodiments of the present application. Based on the embodiments in the present application, all other embodiments obtained by those of ordinary skill in the art without making creative labor premises, all of the present application protected.
[0029] The flowchart shown in the drawings is merely illustrative, and it is not necessary to include all content and operation / steps, nor must be performed in the described order. For example, some operations / steps can also be decomposed, combined, or partially combined, so the order actually performed may change according to the actual situation. Further, although the functional module is divided in the apparatus, in some cases, in some cases, the module different from the apparatus is divided into modules.
[0030...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap